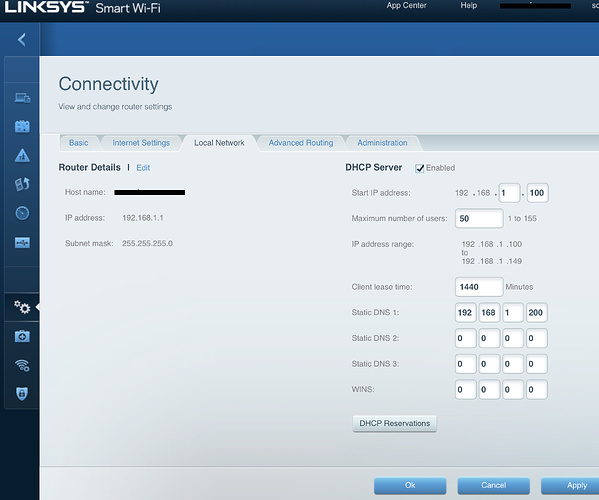
I having problems with wireless clients on my network still seeing ads. Ive set the DNS on my router to my Pi-hole’s iP address. It is the only DNS configured. My clients are set up to automatically configure DNS, which in turn is 192.168.1.1 the address of my router. The Pi-hole's IP is static. When I attempt view a webpage with ads, they are shown. If I black list a site like cnn.com, I can still access it. In the web admin page I do see some traffic being blocked, but not it does not appear to seeing all traffic for some reason. I must have overlooked something here, any suggestions?
Things I’ve tried
- Pi Hole using wireless connection
- Pi Hole using usb wired connection
- Reboot clients
- Renewed Lease on clients
- Reboot Pi
- Reboot Router
- Clean install of Rasbian
- Clean install of Pi Hole
- Swapping to a different router
- Using a different Pi
Hardware:
- Pi Zero W running RASPBIAN Stretch With Desktop
- Linksys EA6400
- Wireless clients: iPad, iPhone, MacBook ProThis text will be hidden
Debug Token: 8ub9o35uqz
*** [ INITIALIZING ]
[i] 2018-03-05:05:35:24 debug log has been initialized.
*** [ INITIALIZING ] Sourcing setup variables
[i] Sourcing /etc/pihole/setupVars.conf...
*** [ DIAGNOSING ]: Core version
[i] Core: v3.3 (How do I update Pi-hole?)
[i] Branch: master
[i] Commit: v3.3-0-g1e87850
*** [ DIAGNOSING ]: Web version
[i] Web: v3.3 (How do I update Pi-hole?)
[i] Branch: master
[i] Commit: v3.3-0-ge48aa29
*** [ DIAGNOSING ]: FTL version
[✓] FTL: v3.0
*** [ DIAGNOSING ]: dnsmasq version
[i] 2.76
*** [ DIAGNOSING ]: lighttpd version
[i] 1.4.45
*** [ DIAGNOSING ]: php version
[i] 7.0.27
*** [ DIAGNOSING ]: Operating system
[✓] Raspbian GNU/Linux 9 (stretch)
*** [ DIAGNOSING ]: SELinux
[i] SELinux not detected
*** [ DIAGNOSING ]: Processor
/opt/pihole/piholeDebug.sh: line 470: $'[\E[32m✓\E[0m] \E[32marmv6l\E[0m': command not found
*** [ DIAGNOSING ]: Networking
[✓] IPv4 address(es) bound to the eth0 interface:
192.168.1.200/24 matches the IP found in /etc/pihole/setupVars.conf
[✓] IPv6 address(es) bound to the eth0 interface:
fe80::1cd5:9486:11e2:5a36 does not match the IP found in /etc/pihole/setupVars.conf (Use IPv6 ULA addresses for Pi-hole)
^ Please note that you may have more than one IP address listed.
As long as one of them is green, and it matches what is in /etc/pihole/setupVars.conf, there is no need for concern.
The link to the FAQ is for an issue that sometimes occurs when the IPv6 address changes, which is why we check for it.
[i] Default IPv4 gateway: 192.168.1.1
- Pinging 192.168.1.1...
[✓] Gateway responded.
*** [ DIAGNOSING ]: Ports in use
is in use by
[22] is in use by sshd
[53] is in use by dnsmasq
[80] is in use by lighttpd
[4711] is in use by pihole-FTL
*** [ DIAGNOSING ]: Name resolution (IPv4) using a random blocked domain and a known ad-serving domain
[✓] cdn.complexmedianetwork.com is 192.168.1.200 via localhost (127.0.0.1)
[✓] cdn.complexmedianetwork.com is 192.168.1.200 via Pi-hole (192.168.1.200)
[✓] doubleclick.com is 74.125.197.102 via a remote, public DNS server (8.8.8.8)
*** [ DIAGNOSING ]: Pi-hole processes
[✓] dnsmasq daemon is active
[✓] lighttpd daemon is active
[✓] pihole-FTL daemon is active
*** [ DIAGNOSING ]: Setup variables
PIHOLE_INTERFACE=eth0
IPV4_ADDRESS=192.168.1.200/24
IPV6_ADDRESS=
PIHOLE_DNS_1=9.9.9.9
PIHOLE_DNS_2=149.112.112.112
QUERY_LOGGING=true
INSTALL_WEB=true
LIGHTTPD_ENABLED=1
*** [ DIAGNOSING ]: Dashboard and block page
[✓] X-Pi-hole: A black hole for Internet advertisements.
[✓] X-Pi-hole: The Pi-hole Web interface is working!
*** [ DIAGNOSING ]: Gravity list
-rw-r--r-- 1 root root 5025183 Mar 5 05:09 /etc/pihole/gravity.list
-----head of gravity.list------
192.168.1.200 0.0.0.0
192.168.1.200 0000mps.webpreview.dsl.net
192.168.1.200 0001.2waky.com
192.168.1.200 000dom.revenuedirect.com
-----tail of gravity.list------
192.168.1.200 zzvjaqnkq.bid
192.168.1.200 zzwzjidz.bid
192.168.1.200 zzz.clickbank.net
192.168.1.200 zz.zeroredirect1.com
*** [ DIAGNOSING ]: contents of /etc/pihole
-rw-r--r-- 1 root root 784 Mar 5 03:16 /etc/pihole/adlists.list
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
https://mirror1.malwaredomains.com/files/justdomains
http://sysctl.org/cameleon/hosts
https://zeustracker.abuse.ch/blocklist.php?download=domainblocklist
https://s3.amazonaws.com/lists.disconnect.me/simple_tracking.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
https://hosts-file.net/ad_servers.txt
https://adaway.org/hosts.txt
https://v.firebog.net/hosts/AdguardDNS.txt
https://v.firebog.net/hosts/Easylist.txt
http://winhelp2002.mvps.org/hosts.txt
-rw-r--r-- 1 root root 8 Mar 5 05:23 /etc/pihole/blacklist.txt
cnn.com
-rw-r--r-- 1 root root 43 Mar 5 05:09 /etc/pihole/local.list
192.168.1.200 pihole
192.168.1.200 pi.hole
-rw-r--r-- 1 root root 234 Mar 5 05:05 /etc/pihole/logrotate
/var/log/pihole.log {
su root root
daily
copytruncate
rotate 5
compress
delaycompress
notifempty
nomail
}
/var/log/pihole-FTL.log {
su root root
weekly
copytruncate
rotate 3
compress
delaycompress
notifempty
nomail
}
-rw-r--r-- 1 root root 163 Mar 5 03:17 /etc/pihole/whitelist.txt
raw.githubusercontent.com
mirror1.malwaredomains.com
sysctl.org
zeustracker.abuse.ch
s3.amazonaws.com
hosts-file.net
adaway.org
v.firebog.net
winhelp2002.mvps.org
*** [ DIAGNOSING ]: contents of /etc/dnsmasq.d
-rw-r--r-- 1 root root 1516 Mar 5 05:05 /etc/dnsmasq.d/01-pihole.conf
addn-hosts=/etc/pihole/gravity.list
addn-hosts=/etc/pihole/black.list
addn-hosts=/etc/pihole/local.list
localise-queries
no-resolv
cache-size=10000
log-queries=extra
log-facility=/var/log/pihole.log
local-ttl=2
log-async
server=9.9.9.9
server=149.112.112.112
interface=eth0
*** [ DIAGNOSING ]: contents of /etc/lighttpd
-rw-r--r-- 1 root root 3027 Mar 5 05:05 /etc/lighttpd/lighttpd.conf
server.modules = (
"mod_access",
"mod_accesslog",
"mod_auth",
"mod_expire",
"mod_compress",
"mod_redirect",
"mod_setenv",
"mod_rewrite"
)
server.document-root = "/var/www/html"
server.error-handler-404 = "pihole/index.php"
server.upload-dirs = ( "/var/cache/lighttpd/uploads" )
server.errorlog = "/var/log/lighttpd/error.log"
server.pid-file = "/var/run/lighttpd.pid"
server.username = "www-data"
server.groupname = "www-data"
server.port = 80
accesslog.filename = "/var/log/lighttpd/access.log"
accesslog.format = "%{%s}t|%V|%r|%s|%b"
index-file.names = ( "index.php", "index.html", "index.lighttpd.html" )
url.access-deny = ( "~", ".inc", ".md", ".yml", ".ini" )
static-file.exclude-extensions = ( ".php", ".pl", ".fcgi" )
compress.cache-dir = "/var/cache/lighttpd/compress/"
compress.filetype = ( "application/javascript", "text/css", "text/html", "text/plain" )
include_shell "/usr/share/lighttpd/use-ipv6.pl " + server.port
include_shell "/usr/share/lighttpd/create-mime.assign.pl"
include_shell "find /etc/lighttpd/conf-enabled -name '*.conf' -a ! -name 'letsencrypt.conf' -printf 'include "%p"
' 2>/dev/null"
$HTTP["url"] =~ "^/admin/" {
setenv.add-response-header = (
"X-Pi-hole" => "The Pi-hole Web interface is working!",
"X-Frame-Options" => "DENY"
)
$HTTP["url"] =~ ".ttf$" {
setenv.add-response-header = ( "Access-Control-Allow-Origin" => "*" )
}
}
$HTTP["url"] =~ "^/admin/.(.*)" {
url.access-deny = ("")
}
include_shell "cat external.conf 2>/dev/null"
*** [ DIAGNOSING ]: contents of /etc/cron.d
-rw-r--r-- 1 root root 1496 Mar 5 05:05 /etc/cron.d/pihole
51 4 * * 7 root PATH="$PATH:/usr/local/bin/" pihole updateGravity
00 00 * * * root PATH="$PATH:/usr/local/bin/" pihole flush once quiet
@reboot root /usr/sbin/logrotate /etc/pihole/logrotate
*/10 * * * * root PATH="$PATH:/usr/local/bin/" pihole updatechecker local
57 19 * * * root PATH="$PATH:/usr/local/bin/" pihole updatechecker remote
@reboot root PATH="$PATH:/usr/local/bin/" pihole updatechecker remote reboot
*** [ DIAGNOSING ]: contents of /var/log/lighttpd
-rw-r--r-- 1 www-data www-data 136 Mar 5 05:33 /var/log/lighttpd/error.log
2018-03-05 05:33:15: (log.c.217) server started
2018-03-05 05:33:15: (server.c.1295) WARNING: unknown config-key: alias.url (ignored)
*** [ DIAGNOSING ]: contents of /var/log
-rw-r--r-- 1 pihole pihole 5794 Mar 5 05:33 /var/log/pihole-FTL.log
[2018-03-05 05:27:18.884] NOTICE: pihole.log has been flushed
[2018-03-05 05:27:18.884] Resetting internal data structure
[2018-03-05 05:27:18.884] Queries in memory before flushing: 984
[2018-03-05 05:27:19.669] Gravity list entries: 141258
[2018-03-05 05:27:19.669] Blacklist entries: 1
[2018-03-05 05:27:19.670] Notice: Increasing wildcards struct size from 0 to 1 (522.00 B)
[2018-03-05 05:27:19.670] Wildcard blocking list entries: 1
[2018-03-05 05:27:19.672] Notice: Increasing queries struct size from 0 to 10000 (440.53 KB)
[2018-03-05 05:27:19.673] Notice: Increasing domains struct size from 0 to 1000 (460.53 KB)
[2018-03-05 05:27:19.673] Notice: Increasing clients struct size from 0 to 10 (460.69 KB)
[2018-03-05 05:27:19.673] New client: 127.0.0.1 localhost (0/10)
[2018-03-05 05:27:19.673] Notice: Increasing forwarded struct size from 0 to 4 (460.80 KB)
[2018-03-05 05:27:19.681] New forward server: 9.9.9.9 dns.quad9.net (0/4)
[2018-03-05 05:27:19.682] Notice: Increasing overTime struct size from 0 to 100 (464.83 KB)
[2018-03-05 05:27:19.689] New forward server: 149.112.112.112 rpz-public-resolver1.rrdns.pch.net (1/4)
[2018-03-05 05:27:19.697] New client: 192.168.1.1 (1/10)
[2018-03-05 05:27:19.727] New forward server: 208.67.220.220 resolver2.opendns.com (2/4)
[2018-03-05 05:27:19.736] New forward server: 208.67.222.222 resolver1.opendns.com (3/4)
[2018-03-05 05:27:19.736] Notice: Increasing forwarded struct size from 4 to 8 (470.19 KB)
[2018-03-05 05:27:19.749] New client: 192.168.1.200 pihole (2/10)
[2018-03-05 05:27:19.752] Imported 984 queries from the long-term database
[2018-03-05 05:27:19.753] Reading from /var/log/pihole.log (rw-r--r--)
[2018-03-05 05:32:53.030] FATAL: FTL received SIGTERM from PID/UID 1/0, exiting gracefully
[2018-03-05 05:32:53.030] Shutting down...
[2018-03-05 05:32:53.068] NOTICE: Received signal SIGHUP - re-reading gravity files
*** [ DIAGNOSING ]: Pi-hole log
-rw-r--r-- 1 dnsmasq root 31188 Mar 5 05:35 /var/log/pihole.log
-----head of pihole.log------
Mar 5 05:27:19 dnsmasq[14270]: 333 127.0.0.1/59893 query[PTR] 9.9.9.9.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 333 127.0.0.1/59893 cached 9.9.9.9 is dns.quad9.net
Mar 5 05:27:19 dnsmasq[14270]: 334 127.0.0.1/58500 query[PTR] 112.112.112.149.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 334 127.0.0.1/58500 cached 149.112.112.112 is rpz-public-resolver1.rrdns.pch.net
Mar 5 05:27:19 dnsmasq[14270]: 335 127.0.0.1/49499 query[PTR] 1.1.168.192.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 335 127.0.0.1/49499 cached 192.168.1.1 is NXDOMAIN
Mar 5 05:27:19 dnsmasq[14270]: 336 127.0.0.1/48225 query[PTR] 220.220.67.208.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 336 127.0.0.1/48225 cached 208.67.220.220 is resolver2.opendns.com
Mar 5 05:27:19 dnsmasq[14270]: 337 127.0.0.1/34051 query[PTR] 222.222.67.208.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 337 127.0.0.1/34051 cached 208.67.222.222 is resolver1.opendns.com
Mar 5 05:27:19 dnsmasq[14270]: 338 127.0.0.1/48014 query[PTR] 200.1.168.192.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 338 127.0.0.1/48014 /etc/pihole/local.list 192.168.1.200 is pihole
Mar 5 05:27:19 dnsmasq[14270]: 339 127.0.0.1/37798 query[PTR] 1.1.168.192.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 339 127.0.0.1/37798 cached 192.168.1.1 is NXDOMAIN
Mar 5 05:27:19 dnsmasq[14270]: 340 127.0.0.1/33477 query[PTR] 200.1.168.192.in-addr.arpa from 127.0.0.1
Mar 5 05:27:19 dnsmasq[14270]: 340 127.0.0.1/33477 /etc/pihole/local.list 192.168.1.200 is pihole
Mar 5 05:27:23 dnsmasq[14270]: 341 127.0.0.1/40654 query[A] pihole from 127.0.0.1
Mar 5 05:27:23 dnsmasq[14270]: 341 127.0.0.1/40654 /etc/pihole/local.list pihole is 192.168.1.200
Mar 5 05:27:23 dnsmasq[14270]: 342 127.0.0.1/40654 query[AAAA] pihole from 127.0.0.1
Mar 5 05:27:23 dnsmasq[14270]: 342 127.0.0.1/40654 cached pihole is NODATA-IPv6
[✓] ** FINISHED DEBUGGING! **