Expected Behavior:
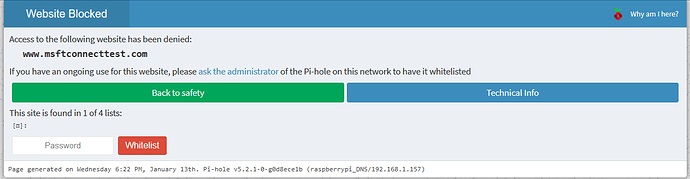
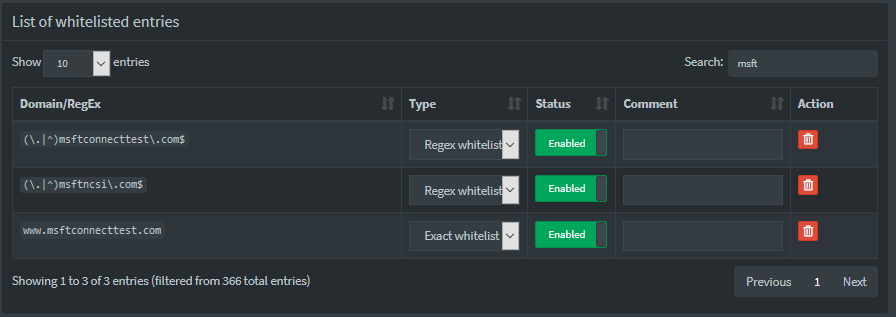
Access should not be blocked to www.msftconnecttest.com due to whitelisting (both exacts and regex's). Even if it were, the actual list it is located in should be listed and I should be able to whitelist.
Actual Behavior:
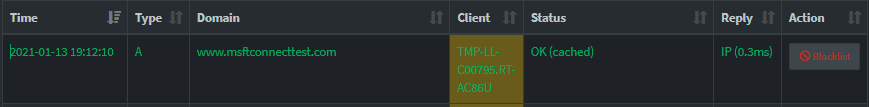
www.msftconnecttest.com is blocked. It is said to be found in 1 of 4 lists. No list is given. Whitelisting it on the block page causes a blue bar to load at the top with no text (as if I whitelisted it). The website is cached and successfully sent over to the device.
Debug Token:
https://tricorder.pi-hole.net/gqusy5pao8
I've confirmed that the whitelist is correct.
I am only using one list, via https://dbl.oisd.nl. The above URLs are not listed in the list.
I posted this question in the community help as I set up cloudflared awhile ago which is working perfect. After having been affected by the Windows 10 NCSI bug where it claims no internet is available even though you do, I wanted to point that service to check my Pi-hole. So I referred to this question (Windows 10 shows Limited internet access but it's connected) where the users jpgpi250 and eejeel discuss on how to point NCSI to check with pi-hole.
I did the following:
1.I created /etc/dnsmasq.d/02-custom_MSncsi.conf.
addn-hosts=/etc/custom_MSncsi.list
2.I created /etc/custom_MSncsi.list.
192.168.1.157 www.msftncsi.com <-- #.#.#.157 is my pi-hole.
192.168.1.157 ipv6.msftncsi.com
192.168.1.157 www.msftconnecttest.com
192.168.1.157 ipv6.msftconnecttest.com
3.I created /var/www/html/connecttest.txt.
Microsoft Connect Test
4.I created /var/www/html/ncsi.txt.
Microsoft NCSI
5.Restart the DNS server.
Does anyone have any ideas? I am a Linux newbie and am picking it up as I go along. It is working, mostly, as devices don't say "No Internet Access" anymore once I've pointed them to 192.168.1.157. It's just the darn webpage opens up as if I didn't, rinse and repeat. Excuse the extra spaces in URLs above as I need to get around the limit of 5.