I've been reading about the choices on this and other forums, but found no convincing answer to this question, so I decided to test them all myself (ongoing). After a while, I figured out how to run them all together, thus getting DNS privacy by obscurity.
Here is my setup:
I'm still only using ipv4, my provider refuses to exchange the docsis cable modem to a v3 modem.
I'm still running the production version of pihole, so no FTLDNS yet, because dnsmasq2.80test2 has a fix for DNSSEC. FTLDNS, based on dnsmasq2.79, doesn't have that fix.
DNSSEC is handled by dnsmasq, this to be able to identify (false) BOGUS dns entries, using the pihole admin page and the dnsmasq log. Also, it is recommended to keep DNSSEC evaluation as close to the client as possible, dnsmasq is the entry point for clients.
I'm still in the process of optimizing the configs, but here is what I got so far:
the dnsmasq config (/etc/dnsmasq.d/04-servers.conf) . As you know, you can add multiple configuration files to this folder, so I removed all server settings from /etc/dnsmasq.d/01-pihole.conf and created a separate file for servers:
server=127.10.10.1#5551
server=127.10.10.2#5552
server=127.10.10.3#5553
As you know, dnsmasq has a built in mechanism to determine the fastest server available.
you can change the defaults, if you want to, by changing
#define FORWARD_TEST 50 /* try all servers every 50 queries */
#define FORWARD_TIME 20 /* or 20 seconds */
in the source, (/dnsmasq-2.80test2/src/config.h) before compiling dnsmasq. You cannot change these settings, once compiled.
This implies, dnsmasq will test all specified resolvers every 50 queries OR every 20 seconds. Notice the entries in the log:
dnsmasq[10498]: 14986 192.168.2.228/64790 forwarded nav.smartscreen.microsoft.com to 127.10.10.1
dnsmasq[10498]: 14986 192.168.2.228/64790 forwarded nav.smartscreen.microsoft.com to 127.10.10.2
dnsmasq[10498]: 14986 192.168.2.228/64790 forwarded nav.smartscreen.microsoft.com to 127.10.10.3
That's the speed test. The domain name will be different, It's just the domain name you are trying to resolve when the (timer) conditions are met.
Another thing you can change, before compiling dnsmasq, is the maximum cache size, by changing:
if (size < 0)
size = 0;
else if (size > 10000)
size = 10000;
in the source (/dnsmasq-2.80test2/src/option.c). Change the value to, for example 65535 (twice). Once everything is up and running, including pihole, you can than increase the cache size by changing the value in /etc/dnsmasq.d/01-pihole.conf and restart dnsmasq. Remember, 01-pihole.conf reverts to default (10000) whenever you run 'pihole -r' or pihole -up'. The result (in the dnsmasq log):
dnsmasq[29727]: started, version 2.80test2 cachesize 65535
I try to keep all my configuration files intact, including comments. for the sake of keeping things small, I ran
sed '/^[[:blank:]]*#/d;s/#.*//' <filename>
before pasting them in this topic. This implies, the configurations also lists the default (original) settings.
The unbound setup and config:
I followed this wiki to setup unbound, and modified the configuration (/etc/unbound/unbound.conf.d/pi-hole.conf) as follows:
server:
logfile: /var/log/unbound.log
verbosity: 1
interface: 127.10.10.2
port: 5552
do-ip4: yes
do-udp: yes
do-tcp: yes
do-ip6: no
root-hints: "/var/lib/unbound/root.hints"
harden-glue: yes
use-caps-for-id: no
cache-min-ttl: 3600
cache-max-ttl: 86400
prefetch: yes
num-threads: 1
so-rcvbuf: 1m
edns-buffer-size: 1472
private-address: 192.168.0.0/16
private-address: 172.16.0.0/12
private-address: 10.0.0.0/8
'edit'
ref: added comment from @mibere, see below
changed the setting 'use-caps-for-id: no'
added the setting 'edns-buffer-size: 1472'
'/edit'
The stubby setup and config:
I followed this and this wiki to setup stubby, and modified the configuration (/etc/stubby.yml) as follows:
resolution_type: GETDNS_RESOLUTION_STUB
dns_transport_list:
- GETDNS_TRANSPORT_TLS
tls_authentication: GETDNS_AUTHENTICATION_REQUIRED
tls_query_padding_blocksize: 256
edns_client_subnet_private : 1
idle_timeout: 10000
listen_addresses:
- 127.10.10.3@5553
round_robin_upstreams: 1
upstream_recursive_servers:
- address_data: 145.100.185.15
tls_auth_name: "dnsovertls.sinodun.com"
tls_pubkey_pinset:
- digest: "sha256"
value: 62lKu9HsDVbyiPenApnc4sfmSYTHOVfFgL3pyB+cBL4=
- address_data: 145.100.185.16
tls_auth_name: "dnsovertls1.sinodun.com"
tls_pubkey_pinset:
- digest: "sha256"
value: cE2ecALeE5B+urJhDrJlVFmf38cJLAvqekONvjvpqUA=
- address_data: 185.49.141.37
tls_auth_name: "getdnsapi.net"
tls_pubkey_pinset:
- digest: "sha256"
value: foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9Q=
As you can see, I'm still using the default resolvers, awaiting suggestions...
The dnscrypt-proxy setup and config:
I followed wiki to setup dnscrypt-proxy, and modified the configuration (/opt/dnscrypt-proxy/dnscrypt-proxy.toml) as follows:
server_names = ['scaleway-fr', 'de.dnsmaschine.net']
listen_addresses = ['127.10.10.1:5551', '[::1]:5551']
max_clients = 250
ipv4_servers = true
ipv6_servers = false
dnscrypt_servers = true
doh_servers = true
require_dnssec = true
require_nolog = true
require_nofilter = true
force_tcp = false
timeout = 2500
keepalive = 30
lb_strategy = 'p2'
log_level = 0
log_file = '/var/log/dnscrypt-proxy.log'
cert_refresh_delay = 240
dnscrypt_ephemeral_keys = true
tls_cipher_suite = [52392, 49199]
fallback_resolver = '208.67.222.222:53'
ignore_system_dns = false
log_files_max_size = 10
log_files_max_age = 7
log_files_max_backups = 1
block_ipv6 = false
cache = false
cache_size = 512
cache_min_ttl = 600
cache_max_ttl = 86400
cache_neg_min_ttl = 60
cache_neg_max_ttl = 600
[query_log]
format = 'tsv'
[nx_log]
format = 'tsv'
[blacklist]
[ip_blacklist]
[whitelist]
[schedules]
[sources]
[sources.'public-resolvers']
urls = ['https://raw.githubusercontent.com/DNSCrypt/dnscrypt-resolvers/master/v2/public-resolvers.md', 'https://download.dnscrypt.info/resolvers-list/v2/public-resolvers.md']
cache_file = 'public-resolvers.md'
minisign_key = 'RWQf6LRCGA9i53mlYecO4IzT51TGPpvWucNSCh1CBM0QTaLn73Y7GFO3'
refresh_delay = 72
prefix = ''
[static]
Here, I've done some research. I want, as you can see in the configuration, servers with the following options: 'no filter', 'no logging' and 'DNSSEC'.
A lot of the servers, listed here, seem to match the criteria, however, a lot of these servers also have a problem with DNSSEC. I found 2 ipv4 servers that don't seem to have this problem: 'scaleway-fr' and 'de.dnsmaschine.net'
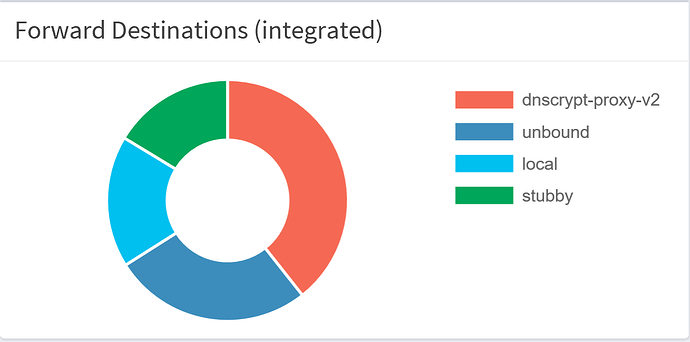
The result, after running this for 24 hours:
Inevitable questions:
Q: How to get the resolvers names in the graph?
A: Simply add the resolvers names to /etc/hosts
# dnscrypt-proxy v2
127.10.10.1 dnscrypt-proxy-v2
# unbound
127.10.10.2 unbound
# stubby
127.10.10.3 stubby
Q: Why so many local requests?
A: I've added two files to the dnsmasq config, to resolve internal IP addresses.
/etc/localdns.list, don't forget to change the domain name (localdomain), format (example):
192.168.2.57 raspberry57.localdomain wpad.localdomain raspberry57 wpad
192.168.2.68 macbook.localdomain macbook
192.168.2.99 tx-l42d25e.localdomain tx-l42d25e
192.168.2.100 ps3.localdomain ps3
/etc/dnsmasq.d/06-localdns.conf
domain=localdomain
expand-hosts
local=/localdomain/
addn-hosts=/etc/localdns.list
Windows 10 keeps querying wpad.localdomain and my other windows machines. This explains the high local query count. This behavior started as soon as I configured a domain in pfsense (mandatory).
You can eliminate a timeout on the wpad request by adding it to the localdns.list (see above) and placing a reply (/var/www/html/wpad.dat) in the pihole webservers directory
function FindProxyForURL(url, host)
{
return "DIRECT";
}
Q: How to compile dnsmasq from source (on raspbian)
A: Run the following script (sudo). Don't do this if you're running FTLDNS!
#!/bin/bash
# Make sure only root can run our script
if [ "$(id -u)" != "0" ]; then
echo "This script must be run as root" 1>&2
exit 1
fi
# install build-essential from STRETCH
sudo DEBIAN_FRONTEND=noninteractive apt-get -yq install build-essential
# install necessary system packages for dnsmasq
# the packages required to build from source are specified under Build-depends in the file debian/control
sudo apt-get -yq install gettext
sudo apt-get -yq install libnetfilter-conntrack-dev
sudo apt-get -yq install libidn11-dev
sudo apt-get -yq install libdbus-1-dev
sudo apt-get -yq install libgmp-dev
sudo apt-get -yq install nettle-dev
sudo apt-get -yq install libbsd-dev
sudo apt-get -yq install liblua5.2-dev
# dnsmasq
file=dnsmasq-2.80test2
mkdir -p dnsmasq
cd dnsmasq
wget http://www.thekelleys.org.uk/dnsmasq/test-releases/$file.tar.gz
tar xzf $file.tar.gz
cd $file
fakeroot debian/rules binary
cd ..
sudo dpkg -i dnsmasq*.deb
cd ..
Q: How many dns queries where performed during the test?
A: I use this software to preform load tests, I run them simultaneously on multiple machines. Pihole stats:
Total queries (6 clients): 4169
Queries blocked: 555
Domains on block list: 601791
I'm NOT a Linux savy, I'm just really good at implementing wiki's and find solutions in duckduckgo. Therefore, I'm willing to answer any question, however, no promises made...
'edit' Typo's '/edit'
discuss...