Please follow the below template, it will help us to help you!
If you are Experiencing issues with a Pi-hole install that has non-standard elements (e.g you are using nginx instead of lighttpd, or there is some other aspect of your install that is customised) - please use the Community Help category.
Expected Behaviour:
Using DNSSEC does not create DNS resolving issues at all.
BUT (long story):
During the last years I tried several times to enable DNSSEC at http://pi.hole/admin/settings.php?tab=dns. Earlier this gave pretty ugly results like
- de.wikipedia.org not loading (iOS)
- buying apps on iOS not possible (p18-buy.itunes.apple.com)
- Firefox sync not working (token.services.mozilla.com)
- Updating QOwnNotes not possible (api.qownnotes.org)
- YouTube not playing videos
- Spotify not able to download content (iOS-App)
- ...
Therefore I had to disable DNSSEC again. The problem is, all those issues get discovered only painfully after quite some time (over days and weeks) as things are not working as they should.
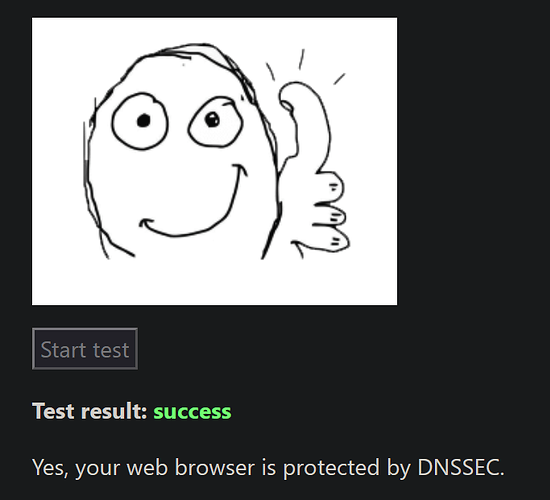
Today I gave it a try and enabled it again. So far all of the above seems to work (it's been a few years since those experiences), BUT: DNSSEC Resolver Test does not load anymore at all (iOS, Windows seems to have it cached from prior to enabling DNSSEC, details with nslookup below).
Actual Behaviour:
This is the setup:
- Pi-Hole up to date (stable)
- Upstream servers:
PIHOLE_DNS_1=9.9.9.9
PIHOLE_DNS_2=5.9.164.112
While Quad9 supports DNSSEC (Frequently Asked Questions | Quad9), I could not verify that for 5.9.164.112 (Zensurfreier DNS-Server | Digitalcourage).
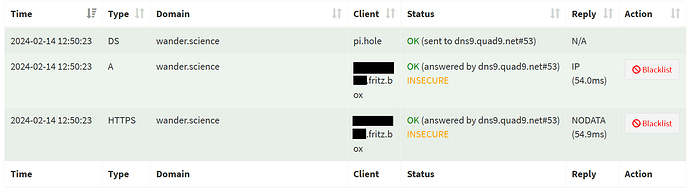
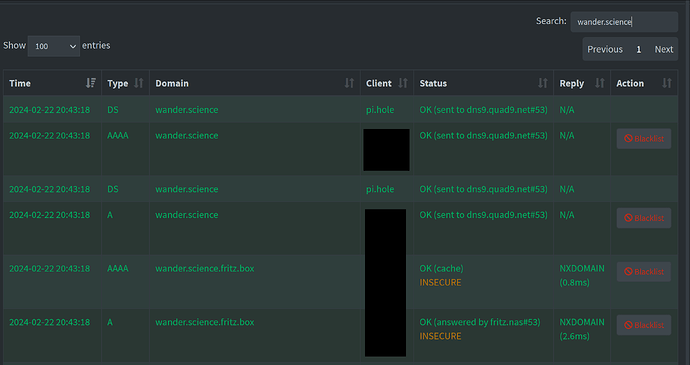
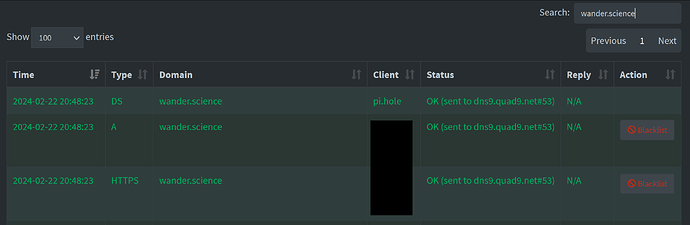
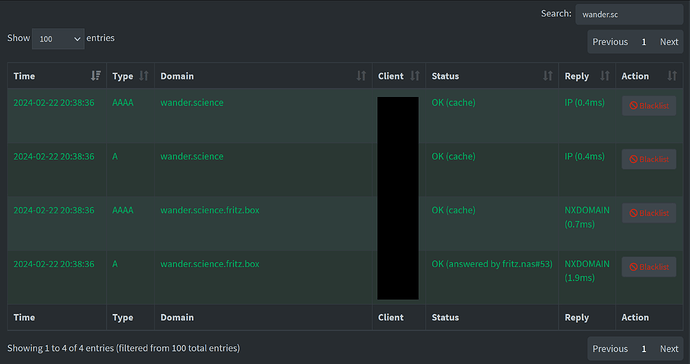
BUT as according to Pi-Hole log Quad9 seems to answer the request on wander.science, I don't get why it seems to fail.
Additionally from a Windows client:
- [DNSSEC enabled] Using Pi-Hole as resolver (
nslookup wander.scienceornslookup wander.science ip-address-of-pi-hole):
Either (first test on Windows endpoint 1):
Server: pi.hole
Address: xxx.xxx.xxx.xxx
DNS request timed out.
timeout was 2 seconds.
Nicht autorisierende Antwort:
Name: wander.science
Or (second test on Windows endpoint 2):
Server: pi.hole
Address: xxx.xxx.xxx.xxx
*** wander.science wurde von pi.hole nicht gefunden: Unspecified error.
with query log output:
This is the query log output when trying to access wander.science in Safari browser on an iOS device:
- [DNSSEC disabled] Once DNSSEC is disabled, using Pi-Hole (
nslookup wander.science/nslookup wander.science ip-address-of-pi-holegives):
Server: pi.hole
Address: xxx.xxx.xxx.xxx
Nicht autorisierende Antwort:
Name: wander.science
Addresses: 2a01:4f8:13b:2048::113
195.201.14.36
...and query log shows:
- [DNSSEC enabled] Using Quad9 as resolver (
nslookup wander.science 9.9.9.9):
Server: dns9.quad9.net
Address: 9.9.9.9
Nicht autorisierende Antwort:
Name: wander.science
Addresses: 2a01:4f8:13b:2048::113
195.201.14.36
- [DNSSEC enabled] Same for using the other upstream DNS server (
nslookup wander.science 5.9.164.112):
Server: dns3.digitalcourage.de
Address: 5.9.164.112
Nicht autorisierende Antwort:
Name: wander.science
Addresses: 2a01:4f8:13b:2048::113
195.201.14.36
I absolutely don't get what happens inside Pi-Hole. This is just an example which is likely a good one to discover why DNSSEC creates such resolving issues.
Feel free to move this to Community Help - Pi-hole Userspace.