Ok so having got my guest wifi setup and all working time for the next little 'problem'
I've added a USB to ethernet adaptor as eth1 & configured it for a static IP of 192.168.1.254 with the intention being of issuing DHCP clients with an IP in the range 192.168.1.100-200 (as it does currently) , DNS of 192.168.1.2 (again as per current setup) but with a default gateway of 192.168.1.254
I already have masquerading setup to allow traffic from wlan0 & eth0 and if I configure my laptop statically for testing with
IP 192.168.1.10
DNS 192.168.1.2
DGW: 192.168.1.254
Everything works as expected.
So far so good as that means when I flip the DHCP config everything will still get out to the internet via my main router on 192.168.1.1 (which is set as the DGW for eth0/192.168.1.2)
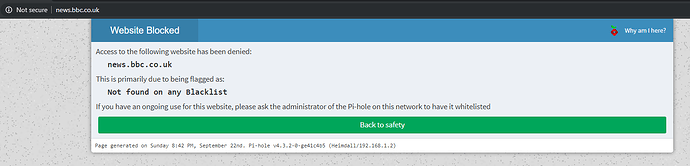
SO my next challenge is intercepting all outbound DNS traffic and forcing it via the PiHole much the same as this post
I've added the Pre routing rules and from the laptop an nslookup without any IP specified works as expected via PiHole.
Nslookup using 192.168.1.1 also works as expected as that bounces it back to the PiHole anyways.
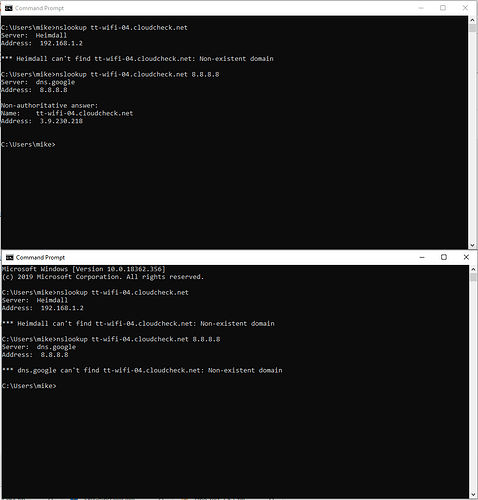
The problem comes when i try running nslookup against say 8.8.8.8
C:\Users\mike>nslookup news.bbc.co.uk 8.8.8.8
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 8.8.8.8
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to UnKnown timed-out
my expectation was that it would route transparently vi the Pihole
pi@Heimdall:~ $ sudo iptables -t nat -L --line-numbers
Chain PREROUTING (policy ACCEPT)
num target prot opt source destination
1 DNAT tcp -- !Heimdall anywhere tcp dpt:domain to:192.168.1.2:53
2 DNAT udp -- !Heimdall anywhere udp dpt:domain to:192.168.1.2:53
Chain INPUT (policy ACCEPT)
num target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
1 MASQUERADE all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
NB1 have also tried it without adding :53 at the end of the destination but that made no difference
NB2 command used to load iptables was
iptables -t nat -A PREROUTING -i eth1 ! -s 192.168.1.2 -p tcp --dport 53 -j DNAT --to 192.168.1.2:53
iptables -t nat -A PREROUTING -i eth1 ! -s 192.168.1.2 -p udp --dport 53 -j DNAT --to 192.168.1.2:53