A while ago, I've setup a separate Pi (i.e in addition to an existing Pi-hole machine) as WLAN access point to isolate my TV from the rest of my network - not quite your setup, but maybe I can provide one hint or another.
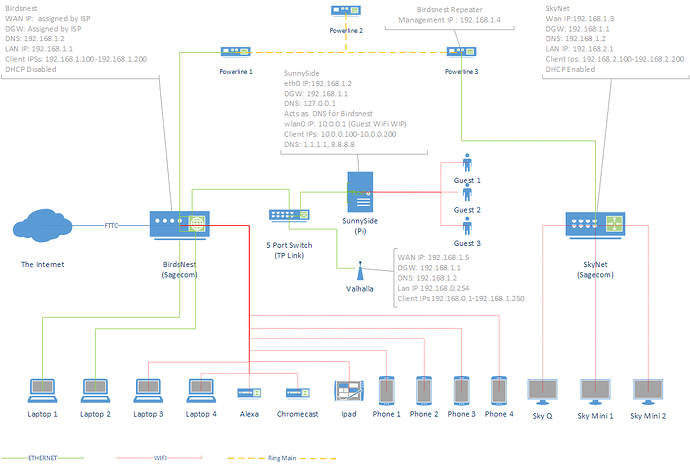
Your network diagram is impressive, but it brings up quite a few questions, so I hope I did understand your setup sufficiently to be of help.
Note
I'd be happy to supply my questions in detail via PM if you'd be interested, but didn't want to make this post any longer than it already is 
If I read your chart correctly, you plan to use your SunnySide-Pi as both a DHCP and a Pi-hole augmented DNS server for two separate sub-networks (which makes this setup a bit trickier than mine).
In my setup, I disabled DHCP client configuration for my WLAN in /etc/dhcpcd.conf:
denyinterfaces wlan0
Instead, I defined a static IP for it in /etc/network/interfaces
# WLAN-interface
allow-hotplug wlan0
iface wlan0 inet static
address 10.10.10.1
netmask 255.255.255.0
In addition, you should consider doing this for your eth0 as well.
more details
I am a bit shy typing that up here as well because I noticed there is a mismatch between your diagram and your description
Your diagram shows 192.168.1.2 as your SunnySide's address, so you'd have to construct the eth0 entries with the correct values for your network.
With regards to iptable's firewall settings, just the following line (exactly the first in your statements) was enough to get me running:
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
The tricky part is going to be the configuration of dnsmasq to serve two subnetworks. In my case, that would've been done by editing /etc/dnsmasq.conf:
# sufficient for my scenario
interface=wlan0
dhcp-range=10.10.10.100,10.10.10.200,24h
dhcp-option=option:dns-server,10.10.10.1
# additional config for your scenario
interface=eth0
dhcp-range=192.168.1.100,192.168.1.200,24h
dhcp-option=option:dns-server,192.168.1.2
This configures a distinct sub-network address range for each interface and hands out the SunnySide's respective IP address as DNS server.
However, as you are using Pi-hole on the same machine in your configuration, you have to find a way to integrate this with Pi-holes built-in dnsmasq (configured via files in the /etc/dnsmasq.d/ directory) and make this configuration survive Pi-hole updates as well as manipulations through Pi-holes web admin UI.
 Perhaps one of the Pi-hole moderators can jump in here and provide us with some insights on how to achieve this ?
Perhaps one of the Pi-hole moderators can jump in here and provide us with some insights on how to achieve this ?