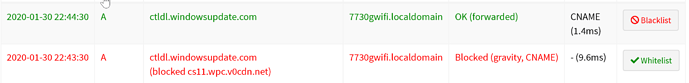
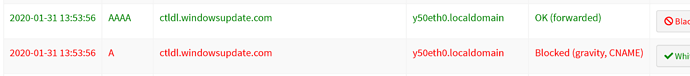
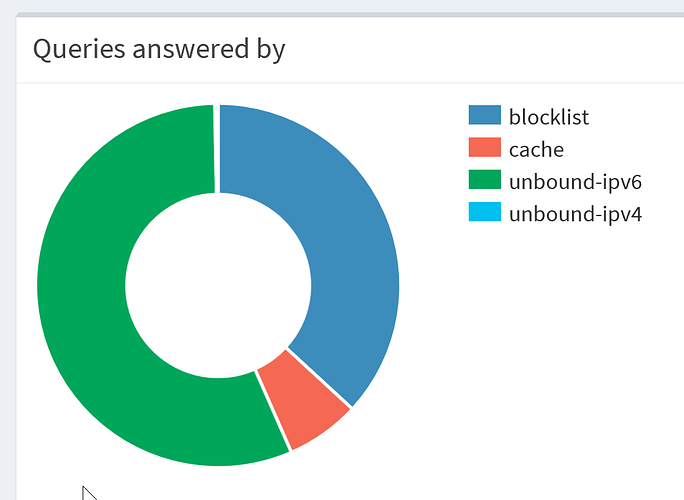
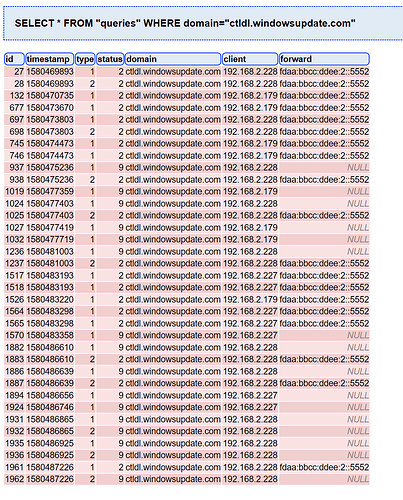
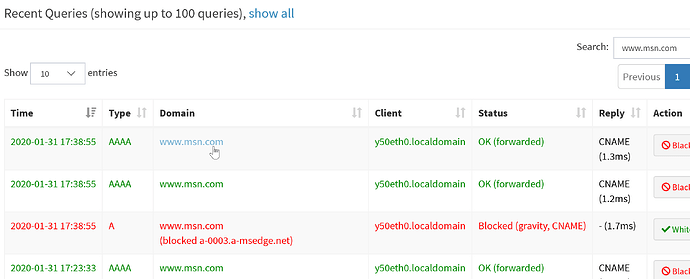
caught one, using the above method, make sure you read the entire post, something else I noticed, explained before the second screenshot..
relevant FTL debug data (13:53:56):
[2020-01-31 13:53:56.719 28875] **** new UDP query[A] "ctldl.windowsupdate.com" from 192.168.2.228 (ID 1737, FTL 936, src/dnsmasq/forward.c:1571)
[2020-01-31 13:53:56.719 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 13:53:56.720 28875] **** got cache answer for ctldl.windowsupdate.com / / <unknown> (ID 1737, src/dnsmasq/rfc1035.c:1714)
[2020-01-31 13:53:56.720 28875] **** forwarded ctldl.windowsupdate.com to fdaa:bbcc:ddee:2::5552 (ID 1737, src/dnsmasq/forward.c:566)
[2020-01-31 13:53:56.721 28875] **** forwarded ctldl.windowsupdate.com to 127.10.10.2 (ID 1737, src/dnsmasq/forward.c:558)
[2020-01-31 13:53:56.721 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 13:53:56.721 28875] CNAME ctldl.windowsupdate.com
[2020-01-31 13:53:56.721 28875] **** got reply ctldl.windowsupdate.com is (CNAME) (ID 1737, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.722 28875] audownload.windowsupdate.nsatc.net is known as not to be blocked
[2020-01-31 13:53:56.722 28875] CNAME ctldl.windowsupdate.com ---> audownload.windowsupdate.nsatc.net
[2020-01-31 13:53:56.722 28875] **** got reply audownload.windowsupdate.nsatc.net is (CNAME) (ID 1737, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.722 28875] wu.azureedge.net is not known
[2020-01-31 13:53:56.723 28875] CNAME audownload.windowsupdate.nsatc.net ---> wu.azureedge.net
[2020-01-31 13:53:56.723 28875] **** got reply wu.azureedge.net is (CNAME) (ID 1737, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.723 28875] wu.ec.azureedge.net is not known
[2020-01-31 13:53:56.724 28875] CNAME wu.azureedge.net ---> wu.ec.azureedge.net
[2020-01-31 13:53:56.724 28875] **** got reply wu.ec.azureedge.net is (CNAME) (ID 1737, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.724 28875] wu.wpc.apr-52dd2.edgecastdns.net is not known
[2020-01-31 13:53:56.725 28875] CNAME wu.ec.azureedge.net ---> wu.wpc.apr-52dd2.edgecastdns.net
[2020-01-31 13:53:56.725 28875] **** got reply wu.wpc.apr-52dd2.edgecastdns.net is (CNAME) (ID 1737, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.725 28875] hlb.apr-52dd2-0.edgecastdns.net is not known
[2020-01-31 13:53:56.726 28875] CNAME wu.wpc.apr-52dd2.edgecastdns.net ---> hlb.apr-52dd2-0.edgecastdns.net
[2020-01-31 13:53:56.726 28875] **** got reply hlb.apr-52dd2-0.edgecastdns.net is (CNAME) (ID 1737, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.726 28875] cs11.wpc.v0cdn.net is not known
[2020-01-31 13:53:56.726 28875] Blocking cs11.wpc.v0cdn.net as domain is gravity blocked
[2020-01-31 13:53:56.726 28875] CNAME hlb.apr-52dd2-0.edgecastdns.net ---> cs11.wpc.v0cdn.net
[2020-01-31 13:53:56.727 28875] **** new UDP query[AAAA] "ctldl.windowsupdate.com" from 192.168.2.228 (ID 1738, FTL 937, src/dnsmasq/forward.c:1571)
[2020-01-31 13:53:56.727 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 13:53:56.728 28875] **** forwarded ctldl.windowsupdate.com to fdaa:bbcc:ddee:2::5552 (ID 1738, src/dnsmasq/forward.c:566)
[2020-01-31 13:53:56.730 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 13:53:56.730 28875] CNAME ctldl.windowsupdate.com
[2020-01-31 13:53:56.730 28875] **** got reply ctldl.windowsupdate.com is (CNAME) (ID 1738, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.730 28875] audownload.windowsupdate.nsatc.net is known as not to be blocked
[2020-01-31 13:53:56.731 28875] CNAME ctldl.windowsupdate.com ---> audownload.windowsupdate.nsatc.net
[2020-01-31 13:53:56.731 28875] **** got reply audownload.windowsupdate.nsatc.net is (CNAME) (ID 1738, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.731 28875] au.download.windowsupdate.com.edgesuite.net is known as not to be blocked
[2020-01-31 13:53:56.731 28875] CNAME audownload.windowsupdate.nsatc.net ---> au.download.windowsupdate.com.edgesuite.net
[2020-01-31 13:53:56.732 28875] **** got reply au.download.windowsupdate.com.edgesuite.net is (CNAME) (ID 1738, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.732 28875] a767.dscg3.akamai.net is known as not to be blocked
[2020-01-31 13:53:56.732 28875] CNAME au.download.windowsupdate.com.edgesuite.net ---> a767.dscg3.akamai.net
[2020-01-31 13:53:56.732 28875] **** got reply a767.dscg3.akamai.net is 2a02:26f0:ed::5c7a:3512 (ID 1738, src/dnsmasq/cache.c:487)
[2020-01-31 13:53:56.732 28875] a767.dscg3.akamai.net is known as not to be blocked
[2020-01-31 13:53:56.733 28875] CNAME a767.dscg3.akamai.net
[2020-01-31 13:53:56.733 28875] **** got reply a767.dscg3.akamai.net is 2a02:26f0:ed::5c7a:352b (ID 1738, src/dnsmasq/cache.c:487)
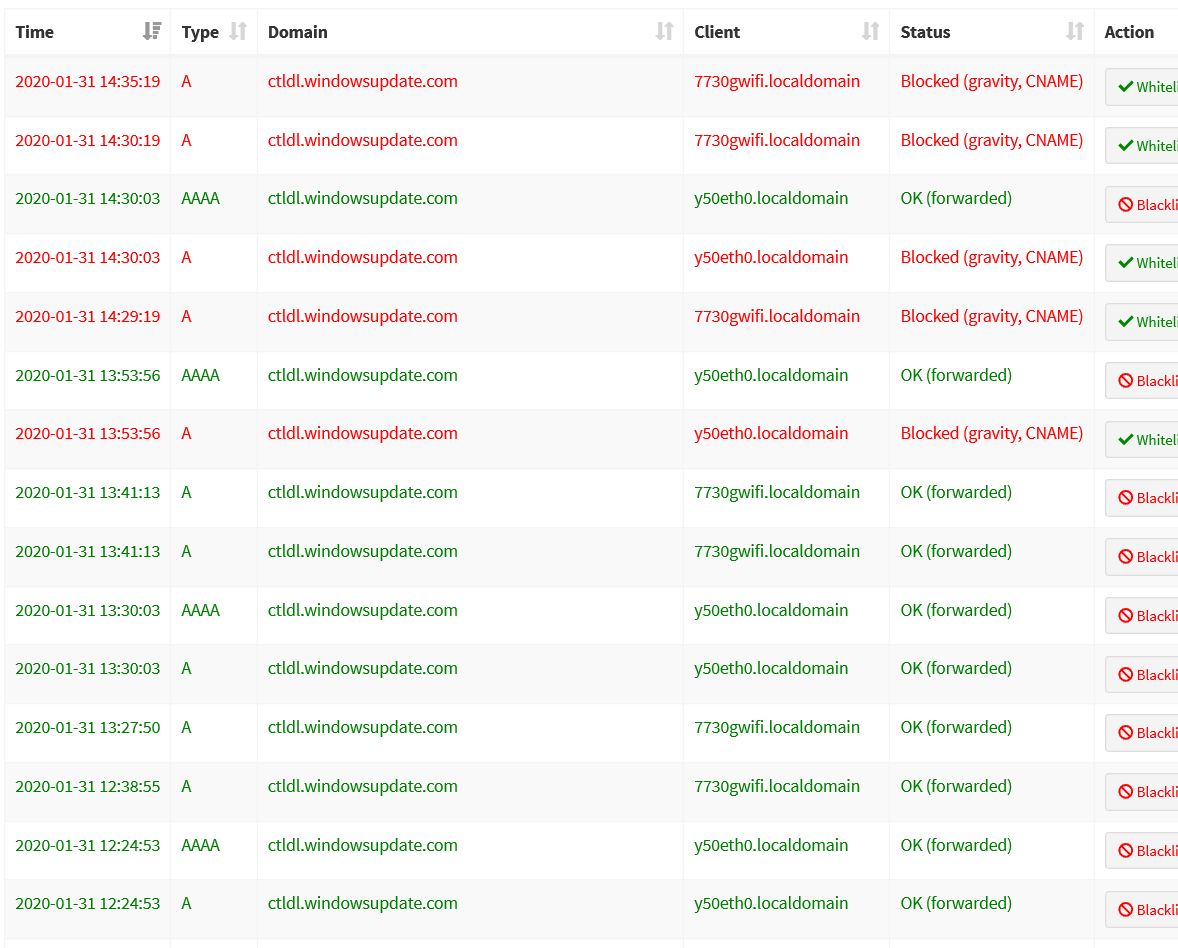
My method reveals another point of interest:
The list reveals this is NOT always happening. Sometimes the query simply has a forwarded status.
I'm also including the debug log for the event at 12:24:53 (forwarded), this may clarify somethings.
[2020-01-31 12:24:53.963 28875] **** new UDP query[A] "ctldl.windowsupdate.com" from 192.168.2.228 (ID 27, FTL 26, src/dnsmasq/forward.c:1571)
[2020-01-31 12:24:53.963 28875] ctldl.windowsupdate.com is not known
[2020-01-31 12:24:53.964 28875] **** forwarded ctldl.windowsupdate.com to fdaa:bbcc:ddee:2::5552 (ID 27, src/dnsmasq/forward.c:566)
[2020-01-31 12:24:53.965 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 12:24:53.965 28875] CNAME ctldl.windowsupdate.com
[2020-01-31 12:24:53.965 28875] **** got reply ctldl.windowsupdate.com is (CNAME) (ID 27, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.965 28875] audownload.windowsupdate.nsatc.net is not known
[2020-01-31 12:24:53.966 28875] CNAME ctldl.windowsupdate.com ---> audownload.windowsupdate.nsatc.net
[2020-01-31 12:24:53.966 28875] **** got reply audownload.windowsupdate.nsatc.net is (CNAME) (ID 27, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.966 28875] au.download.windowsupdate.com.edgesuite.net is not known
[2020-01-31 12:24:53.966 28875] CNAME audownload.windowsupdate.nsatc.net ---> au.download.windowsupdate.com.edgesuite.net
[2020-01-31 12:24:53.967 28875] **** got reply au.download.windowsupdate.com.edgesuite.net is (CNAME) (ID 27, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.967 28875] a767.dscg3.akamai.net is not known
[2020-01-31 12:24:53.967 28875] CNAME au.download.windowsupdate.com.edgesuite.net ---> a767.dscg3.akamai.net
[2020-01-31 12:24:53.967 28875] **** got reply a767.dscg3.akamai.net is 2.17.107.33 (ID 27, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.967 28875] a767.dscg3.akamai.net is known as not to be blocked
[2020-01-31 12:24:53.967 28875] CNAME a767.dscg3.akamai.net
[2020-01-31 12:24:53.968 28875] **** got reply a767.dscg3.akamai.net is 2.17.107.18 (ID 27, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.968 28875] **** new UDP query[AAAA] "ctldl.windowsupdate.com" from 192.168.2.228 (ID 28, FTL 27, src/dnsmasq/forward.c:1571)
[2020-01-31 12:24:53.968 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 12:24:53.969 28875] **** forwarded ctldl.windowsupdate.com to fdaa:bbcc:ddee:2::5552 (ID 28, src/dnsmasq/forward.c:566)
[2020-01-31 12:24:53.975 28875] ctldl.windowsupdate.com is known as not to be blocked
[2020-01-31 12:24:53.975 28875] CNAME ctldl.windowsupdate.com
[2020-01-31 12:24:53.976 28875] **** got reply ctldl.windowsupdate.com is (CNAME) (ID 28, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.976 28875] audownload.windowsupdate.nsatc.net is known as not to be blocked
[2020-01-31 12:24:53.976 28875] CNAME ctldl.windowsupdate.com ---> audownload.windowsupdate.nsatc.net
[2020-01-31 12:24:53.976 28875] **** got reply audownload.windowsupdate.nsatc.net is (CNAME) (ID 28, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.976 28875] auto.au.download.windowsupdate.com.c.footprint.net is not known
[2020-01-31 12:24:53.977 28875] CNAME audownload.windowsupdate.nsatc.net ---> auto.au.download.windowsupdate.com.c.footprint.net
[2020-01-31 12:24:53.977 28875] **** got reply auto.au.download.windowsupdate.com.c.footprint.net is 2001:1900:2326:2f03::1fe (ID 28, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.977 28875] auto.au.download.windowsupdate.com.c.footprint.net is known as not to be blocked
[2020-01-31 12:24:53.977 28875] CNAME auto.au.download.windowsupdate.com.c.footprint.net
[2020-01-31 12:24:53.977 28875] **** got reply auto.au.download.windowsupdate.com.c.footprint.net is 2001:1900:2324:2f00::1fe (ID 28, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.977 28875] auto.au.download.windowsupdate.com.c.footprint.net is known as not to be blocked
[2020-01-31 12:24:53.977 28875] CNAME auto.au.download.windowsupdate.com.c.footprint.net
[2020-01-31 12:24:53.978 28875] **** got reply auto.au.download.windowsupdate.com.c.footprint.net is 2001:1900:2324:1c00::1fe (ID 28, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.978 28875] auto.au.download.windowsupdate.com.c.footprint.net is known as not to be blocked
[2020-01-31 12:24:53.978 28875] CNAME auto.au.download.windowsupdate.com.c.footprint.net
[2020-01-31 12:24:53.978 28875] **** got reply auto.au.download.windowsupdate.com.c.footprint.net is 2001:1900:2324:5011::1fe (ID 28, src/dnsmasq/cache.c:487)
[2020-01-31 12:24:53.978 28875] auto.au.download.windowsupdate.com.c.footprint.net is known as not to be blocked
[2020-01-31 12:24:53.978 28875] CNAME auto.au.download.windowsupdate.com.c.footprint.net
[2020-01-31 12:24:53.978 28875] **** got reply auto.au.download.windowsupdate.com.c.footprint.net is 2001:1900:2326:2f12::1fe (ID 28, src/dnsmasq/cache.c:487)