running Raspberry Pi OS (32-bit) Lite (Linux raspberrypi 4.19.118-v7+ #1311 SMP Mon Apr 27 14:21:24 BST 2020 armv7l GNU/Linux)
On Windows 10, privacy extensions are enabled by default. This implies my IPv6 address, used to connect to the outside world changes regulary, making it harder for the outside world to identify me (unless of course I have to authenticate to use the service).
Apparently, Raspbian also has the option to use privacy extensions, disabled by default. The default setting implies that all my DNS request originate from the same IPv6 address.
I'm already using unbound, this setup implies that no one party is able to identify my browsing habits, however, the frequently visited parties still can identify when and how frequently I request DNS info from their nameservers.
I was looking into this, and found some interesting links, here, here and here, which resulted in the following configuration:
# https://www.kernel.org/doc/Documentation/networking/ip-sysctl.txt
net.ipv6.conf.eth0.use_tempaddr=2
net.ipv6.conf.default.use_tempaddr=0
net.ipv6.conf.eth0.temp_prefered_lft = 7200
net.ipv6.conf.default.temp_prefered_lft = 86400
net.ipv6.conf.eth0.temp_valid_lft = 9000
net.ipv6.conf.default.temp_valid_lft = 604800
After activating this configuration, ifconfig now shows:
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.2.249 netmask 255.255.255.192 broadcast 192.168.2.255
inet6 2a02:1810:xxxx:6903:496f:yyyy:819a:zzzz prefixlen 64 scopeid 0x0<global>
inet6 fe80::18f:25da:8971:5687 prefixlen 64 scopeid 0x20<link>
inet6 2a02:1810:4d02:6903:cc3b:9557:84b1:23e5 prefixlen 64 scopeid 0x0<global>
ether b8:27:eb:29:72:97 txqueuelen 1000 (Ethernet)
RX packets 832 bytes 662692 (647.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 789 bytes 97365 (95.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
2a02:1810:xxxx:6903:496f:yyyy:819a:zzzz (masked) being the real IPv6 address of the test system.
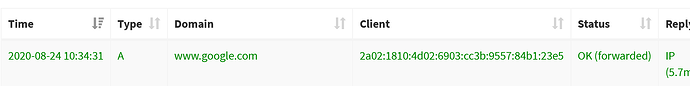
2a02:1810:xxxx:6903:cc3b:9557:84b1:23e5 being the temporary IPv6 address.
I rebooted the system to check if the temporary address really changes (did not have the patience yet to wait 7200 - third setting), it does...
edit
I can confirm after two hours (7200) the system adds an additional temporary IPv6 address. Dig immediately uses the new address (visible in the query log). According to this (run the grep command) the system default will allow up to 16 IPv6 addresses on a single adapter. The reason for this would be to keep existing connections on the previous temporary address open. Since I'm only using pihole + unbound (connections only open for a very short time), I'm testing the following additional settings:
net.ipv6.conf.eth0.max_addresses=3
net.ipv6.conf.default.max_addresses=16
I will have to wait for several hours to see the effect of these settings.
/edit
edit2
It turns out the setting max_addresses doesn't have any impact on the number of temporary addresses, so I removed it. After querying for information on the Raspbian forum, a user pointed me in the right direction, the setting temp_valid_lft is the one that does the trick. I've updated the settings I'm using (see above) to reflect the settings I'm currently testing.
With these settings, a new global temporary dynamic address is generated (and used) every two hours, the global temporary deprecated dynamic address is removed 30 minutes later.
/edit2
The question(s).
- Is it correct to assume this will increase my privacy, by preventing individual DNS servers to build a history of my DNS requests.
- Anybody tried this (or has it enabled by default) and knows if this has any impact on the functionality of pihole or unbound.
edit Anybody has an idea how to identify the real versus the temporary IPv6 address? both ifconfig (on the test system) and ndp -na (on the pfsense router) do not provide info to identify the addresses.answer: ip -6 a
/edit
Test scenario:
- pihole + unbound running on primary system.
- latest (clean) Raspbian version on test system + dnsutils
- executed dig command on test system: dig @2a02:1810:xxxx:6902:da97:yyyy:55e:zzzz www.google.com (2a02:1810:xxxx:6902:da97:yyyy:55e:zzzz = IPv6 of primary system)
result (query log):
which shows the temporary IPv6 address is indeed the address, used to initiate the query.
Any insight is welcome, IPv6 still has a lot of secrets (for me, possibly others).