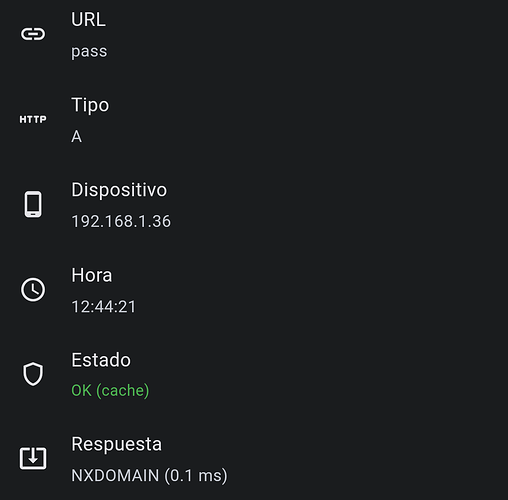
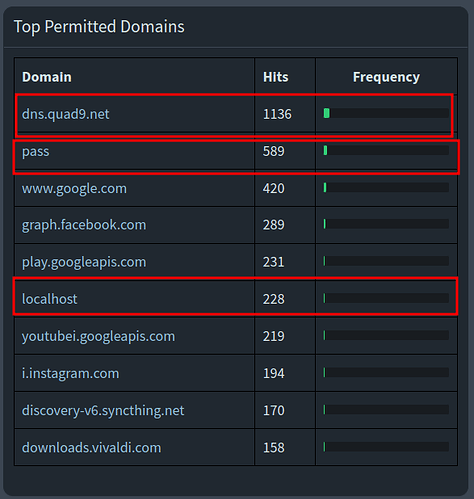
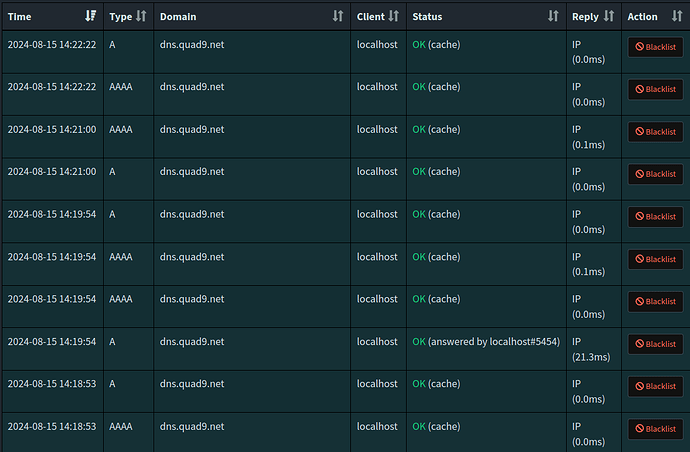
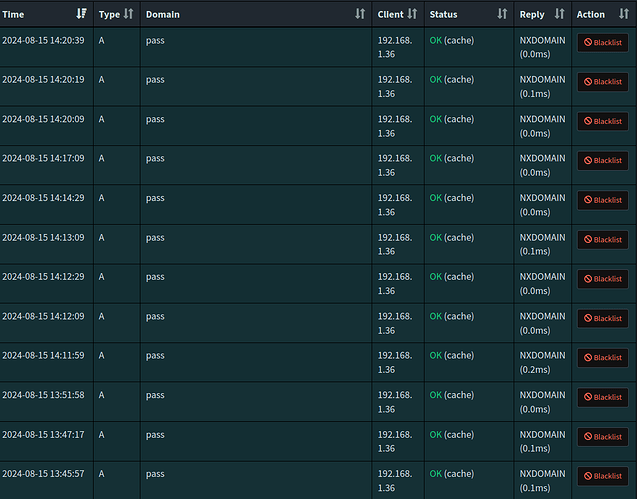
hi, i have been observing for a few days that my Pi-Hole makes many queries to these 3 domains: "dns.quad9.net", "pass" and "localhost". i don't know if it is really bad, but it makes me curious, i provide screenshots below. by the way, i have cloudflared configured with Quad9 as upstream.
Pi-hole would not request resolution of those domains, and those screenshots do not look like Pi-hole ones.
How/why do you think Pi-hole would be involved?
well they are from DroidHole which is an app to have an easier access on the device, but these queries come from Pi-Hole, even in the official web interface they appear.
Since I do not use DroidHole, I can't really comment on those screenshots.
Could you share some of the Pi-hole screens you mention?
Also, please upload a debug log and post just the token URL that is generated after the log is uploaded by running the following command from the Pi-hole host terminal:
pihole -d
or do it through the Web interface:
Tools > Generate Debug Log
While that screenshot shows that dns.quad9.net is the top allowed domain, it does not tell us which clients have requested it.
Clicking on that domain in Pi-hole's dashboard should take you to the filtered Query Log, which should list some of the client IPs or names.
As Pi-hole would not request resolution itself other than for its updates via GitHub (and DNSSEC related ones, which we don't observe here), you'd have to investigate the clients for the software that issues them.
This would include requests send by the localhost client, which would originate from one of the other processes running on your Pi-hole machine.
A few requests for localhost would be generally expected, and so likely would be dns.quad9.net in your specific case.
As you are running a DoH proxy, it would be likely that it is that cloudflared proxy that is requesting dns.quad9.net, especially if you had configured it for that very domain.
I have no idea why your .36 client would request pass, and whether that would be normal under certain circumstances.
You'd have to figure that on that specific client yourself.
okey I understand, by the way, does it make any sense to activate DNSSEC in Pi-Hole if the upstream dns already has it?
Enabling Pi-hole's DNSSEC validation in addition to cloudflared's would not add much security here, but it certainly would add some transparency if you'd be keen to learn about DNSSEC.
Having a read of Understanding DNSSEC validation using Pi-hole's Query Log may help you decide how keen you would be. ![]()
understood, thank you very much for the help and the quick response.
A post was split to a new topic: Why would clients request dns.quad9.net?
This topic was automatically closed 21 days after the last reply. New replies are no longer allowed.