I upgraded to V6.0, but now I can't access the internet unless I pick the "Permit all origins" option. I don't know if I should be doing this. I also uninstalled PiHole and reinstalled PiHole, but I still had to "Permit all origins" to access the internet. Do I need to block port 53 on my router to be able to use PiHole?
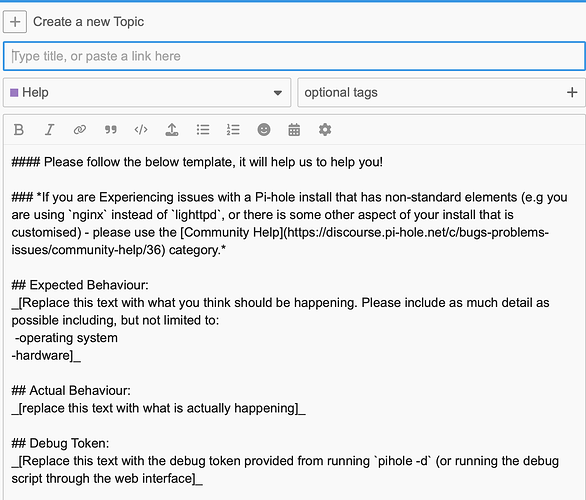
Per our help template, please generate a debug log, upload the log when prompted and post the token URL here.
Are you referring to the templet when the support request is created:
-
- Pi-hole version: [version number]
- Router model: [model name]
- Affected devices: [device types]
- Specific website that is not being blocked: [website URL]
-
What I've tried:
- Verifying DNS settings on devices are set to point to Pi-hole
- Clearing browser cache and cookies
- Checking the blocklist for the website
I'm referring to the last lines in the help template:
Please upload a debug log and post just the token URL that is generated after the log is uploaded by running the following command from the Pi-hole host terminal:
pihole -d
Here is the Token
https://discourse.pi-hole.net
Any new info on this?
It looks like you didn't actually post your token. You posted the homepage URL of these pi-hole.net forums.
You'll have to ssh into your raspberry pi and run the command pihole -d. Let it run, and at the end when it asks you to upload the log, choose 'Yes'. Then it will give you a URL that looks like this: https://tricorder.pi-hole.net/n7e9o2o/. Post that in this thread.
Hope this helps.
I have pasted the support token
Thanks for the help on this..
You're welcome.
That should be blocked by default by the Firewall on your Router so I would not worry about that too much ![]()
What does your network setup look like ??
This is how I have the pihole set up on my router
DNS Server
192.168.1.151 -- Pihole
My machines IP is 192.168.148.x subnet and so is the pihole (Ubuntu VM 192.168.1.151)
Pihole itself is running as a VM on a Synology DS220+ using the "Default" host bridge network interface
If you have more than one subnet then that's the reason you need to Permit All Origins :
- 192.168.1.0/24 subnet
- 192.168.148.0/24 subnet
You can solve this by either leaving it as is or by using VLAN Interfaces for Pi-Hole ![]()
This might have been a typo by the OP.
2: ens3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 02:11:32:2c:93:74 brd ff:ff:ff:ff:ff:ff
altname enp0s3
inet 192.168.1.151/24 brd 192.168.1.255 scope global dynamic noprefixroute ens3
valid_lft 86092sec preferred_lft 86092sec
*** [ DIAGNOSING ]: Network routing table
default via 192.168.1.1 dev ens3 proto dhcp src 192.168.1.151 metric 100
192.168.1.0/24 dev ens3 proto kernel scope link src 192.168.1.151 metric 100
*** [ DIAGNOSING ]: Networking
[i] Default IPv4 gateway(s):
192.168.1.1%ens3
* Pinging first gateway 192.168.1.1...
Network looks OK, I think?
That said - if it's working with permit all then provided that the device is not exposed directly to the internet (i.e it's a local device on your local network and no port forwarding is set up from the router -> VM) then it's safe to use that option
He was editing his post while I was typing and suddenly added that subnet so I assume it's not ?!
Also mentions this :
That's clearly two subnets ![]()
Yes. Its not FWDing any ports and its not exposed to the internet.
So, Do I need to set up a FWD from my router to the pihole VM?
No - don't do that!
Like I said, as long as you are not forwarding port 53 to your Pi-hole - using that setting is perfectly safe to do.
Sorry, Just so I know. I can use the "Permit all origins" option?
... Yes