It was an interesting evening. After some fiddling I don't use any "external" (Quad9, Cloudflare, ...) upstream DNS server in Pi-hole anymore - Pi-hole uses my own now. Controlled and configured by me, located in my country, IPv4 + IPv6, UDP + TCP, no forwarding (no forward-zone), DNSSEC, no logging, no filtering. I like it 
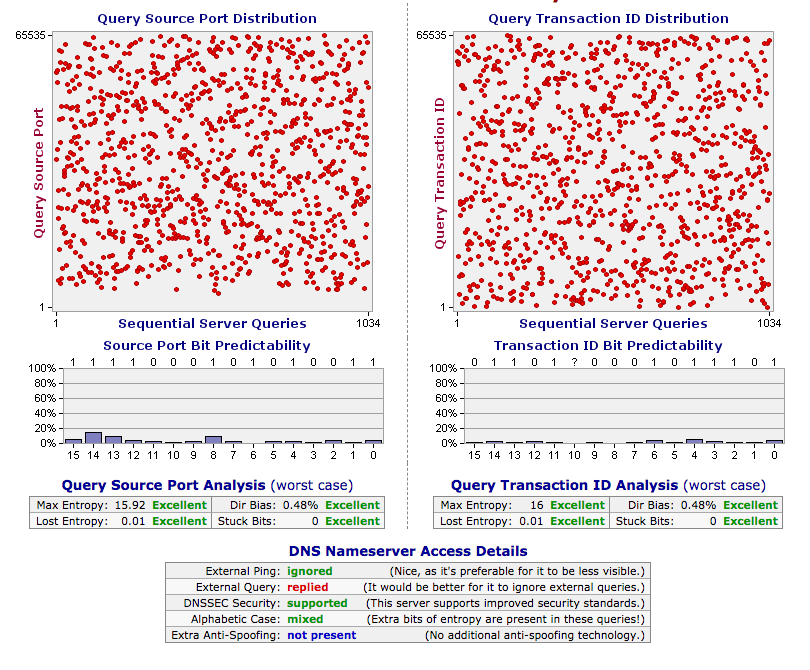
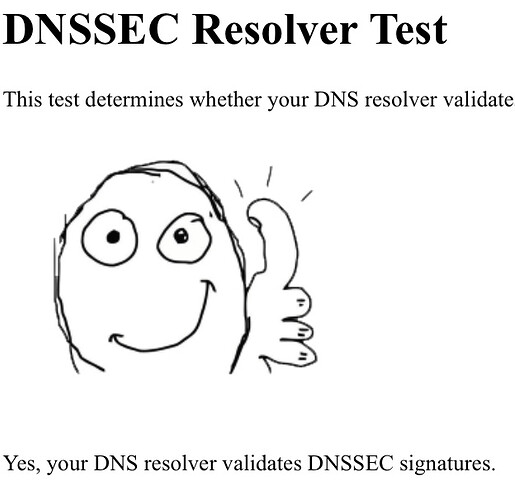
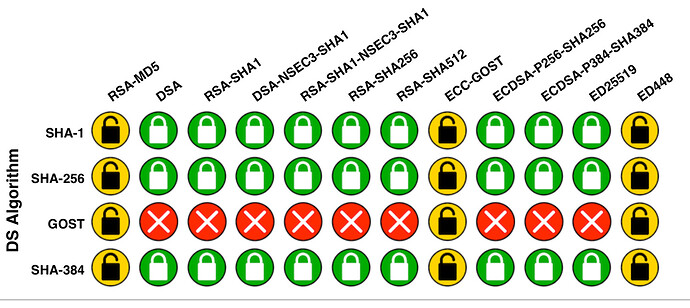
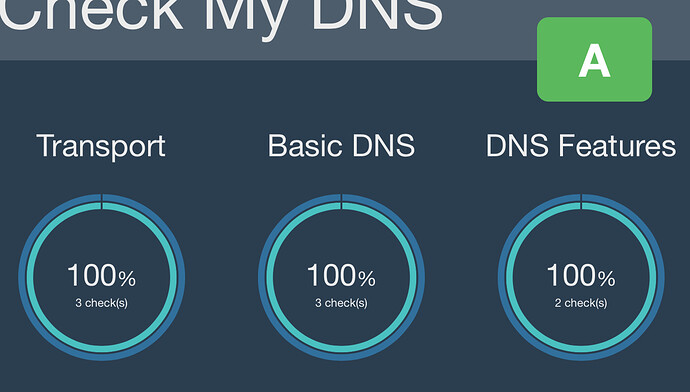
To test your used or own server, here are some sites (and the results of my server):
https://internet.nl/connection/
Nice! Where is it hosted? Are you using Unbound or something else? I tried Unbound on my older RPi 2 and it was pretty fast. Of course, a public DNS server would still be faster, but it wasn't that bad, honestly, still perfectly usable once the cache populates. My ISP DNS is 2-5ms away, so it kinda doesn't make sense for me to run my own DNS at home, but still if you want DNSSEC and more privacy is a fun project to do and you learn something new along the way.
I'm running Unbound (without forwarding to other DNS servers) on Debian, located in Germany hosted by Hetzner.
It was fun and interesting to set it up.
It's maybe slower compared to big and distributed server farms like Quad9 or Cloudflare, but as I definitively know that there is no tracking and logging on the own server  ...
...
So tell us more please : How does one start running a private DNS server ?!
I know about the available software like PowerDNS/BIND/etc. but the part that bugs me is where do you get your "source DNS records" from if you understand what I mean ?
I believe two IP's are also mandatory but I am guessing you got those from Hetzner ofcourse 
its easy: install unbound on Debian server (local or service provider)
- Unbound DNS Server Tutorial @ Calomel.org
- https://freedif.org/unbound-your-own-dns-server
- http://info.menandmice.com/blog/bid/40298/End-to-End-DNSSEC-using-Unbound-DNS
- Unbound - ArchWiki
- https://www.ukuug.org/events/spring2011/timetable/dnssec-unbound.pdf
You can implement unbound without any DNS-Forwarder using qname-minimisation: yes
At the first DNS-Stage you can also block DNS-requests using [dns_blocker.sh](https://github.com/sfeakes/ipfire-scripts)
unbound could answer with the faster status code NXDOMAIN
a final script setup could be:
/bin/dns_blocklist.sh -s 1,2,3,12,13,14 -b /etc/unbound_control/blacklist.hosts && sed -i 's/local-data/local-zone/g; s/[[:space:]]A 127.0.0.1"/" static/g' /etc/unbound/local.d/blocklist.conf && /etc/init.d/unbound restart
I personally run a few Unbound upstreams with DNSSEC enabled on a couple of small TinyKVM nodes ($15/yr). I run them off of Alpine for the small size, but Calomel is a great resource to start with. Thanks @MaDa for the additional sources and tips.
Sounds good! Read the first tutorial quickly and I see FreeBSD mentioned so looks like I will be building a new VM soon ![]()
I've stopped my server after a hint by an experienced user and some further reading. The general and urgent recommendation is: do not offer an open recursive resolver, do not run Unbound with 'access-control: 0.0.0.0/0 allow' and/or 'access-control: ::0/0 allow'.
As it's a cool project, I switched to DNSCrypt and set up a new public server in Germany. It's in the official resolver list now.
This server is the only one in my Pi-hole for some days, without problems so far.
Website: dnscrypt.me
See also
if you want to avoid upstream DNS servers.