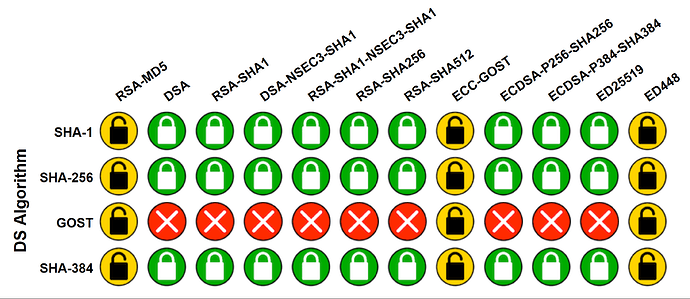
I just had a conversation with @DL6ER about DNSSEC, after finding this website, that allows you to run some test. On the right side of the page, there is a box ‘further connection testing’ with the ‘DNSSEC resolver algorithm test’.
Running the test, with dnsmasq as the DNSSEC evaluator gives this result:
If you run your system with only dnsmasq (or FTLDNS), so no unbound, dnscrypt-proxy or stubby, you should at least get this result, otherwise you're using resolvers that handle DNSSEC incorrect.
It turns out, implementing this unbound solution, and having the DNSSEC evaluation performed by unbound, delivers a far better (more green) result. This implies you need to turn off the DNSSEC evaluation for dnsmasq, using settings.
Of course, you no longer have DNSSEC information in the pihole query page.
DL6ER has indicated future versions of pihole, when using unbound+DNSSEC and FTLDNS without DNSSEC will show SERVFAIL on the query page.
Further more, there is a bug (dnsmasq does check unsigned replies even without that flag set) in the dnsmasq versions 2.77 .. 2.79 (also in FTLDNS - uses 2.79) that causes dnsmasq to ignore an unsigned (and thus BAD) DNSSEC record. This wan't be solved until dnsmasq2.80 is released (and FTLDNS has adopted this version. This bug causes evaluations to be SECURE, where they should in fact fail.