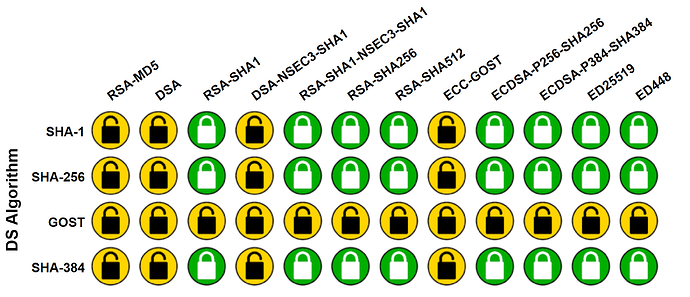
This has been discussed in 2018, see here. You need to run the test, described in the topic), as you can see, in the topic (screenshot), ED448 wasn't really supported at that time.
Things have changed, the current situation, on my system, using pihole-FTL version dnsmasq vDev-14cffae (on request of DL6ER) + compiled unbound (see github), is:
It looks like the domain has a perfect score, see here, so if you can't resolve the domain, either dnsmasq (= piholeFTL) or your upstream resolver doesn't handle the DNSSEC records as expected. Note that I use DNSSEC on unbound (disabled on pihole)
I get
dig ed448.no
; <<>> DiG 9.16.33-Raspbian <<>> ed448.no
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27031
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;ed448.no. IN A
;; ANSWER SECTION:
ed448.no. 3369 IN A 194.63.248.47
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Wed Nov 02 16:55:13 CET 2022
;; MSG SIZE rcvd: 53