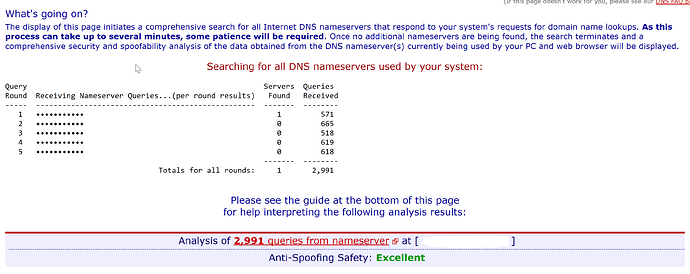
I run pihole + unbound + redis on my pi, was very interested in the result of the spoof test. My firewall is a pfsense, with a NAT rule, redirecting all DNS requests, NOT originating from the pi, to pihole. The result:
Therefore, I assume there is something wrong with your config, pihole and unbound are NOT the cause.
edit
in a discussion on a dutch forum, some people listed the required openwrt rules, required to achieve redirection:
I don't use openwrt, so I'm NOT able to verify this!
#keep network on pi-hole
iptables -t nat -I PREROUTING -i br-lan -p tcp --dport 53 -j DNAT --to 10.0.0.xx:53
iptables -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.0.0.xx:53
#punch DNS hole for pi-hole
iptables -t nat -I PREROUTING -i br-lan -p tcp -s 10.0.0.xx --dport 53 -j ACCEPT
iptables -t nat -I PREROUTING -i br-lan -p udp -s 10.0.0.xx --dport 53 -j ACCEPT
OR, consolidated version:
iptables -t nat -I PREROUTING -i br-lan -p tcp --dport 53 -s ! 10.0.0.xx -j DNAT --to 10.0.0.xx:53
iptables -t nat -I PREROUTING -i br-lan -p udp --dport 53 -s ! 10.0.0.xx -j DNAT --to 10.0.0.xx:53
/edit