lonkelo
November 15, 2023, 9:56pm
1
The issue I am facing:
Details about my system:
What I have changed since installing Pi-hole: How do I configure my devices to use Pi-hole as their DNS server? ) I went the route of the first method defined there: Define Pi-hole's IP address as the only DNS entry in the route.
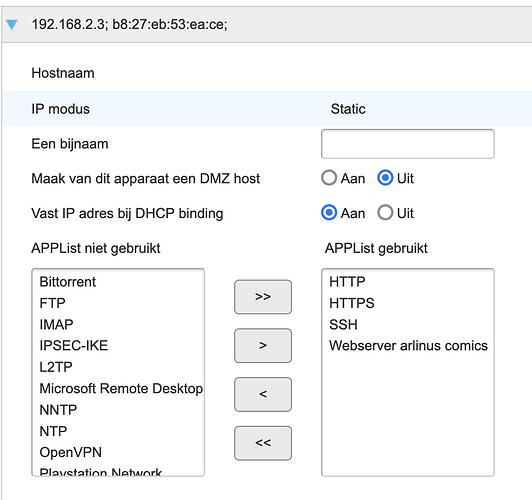
I already had a website running on my Pi from port 80. So I set lighttpd to use port 8888 instead. Because of the existing website I had already used DHCP binding to set my Raspberry Pi to a static address. Other than that I have allowed port 53/tcp and 53/udp in ufw.
I have uploaded a debug token here: https://tricorder.pi-hole.net/wb56r002/
Please let me know if you require any other information. Thanks in advance!
You said you followed method 1, but your router is advertising itself as DNS server:
router: 192.168.2.254
dns-server: 192.168.2.254
Where did you set the DNS?
The tutorial explicitly says:
Note: make sure you adjust this setting under your LAN settings and not the WAN.
(This config name can differ from router to router: LAN, LAN/DHCP, Internal Nework. Sometimes it's hidden under an Advanced tab or button.)
If your router does not allow to change the DNS on the LAN/DHCP settings, then you will need to keep the config as it is, but you won't be able to see individual devices in Pi-hole query log.
lonkelo
November 16, 2023, 6:45am
3
This is the info screen under LAN
Under settings itself (it doesn't say LAN explicitly, but there is WAN stated in a different screen)
Hope this clarifies something
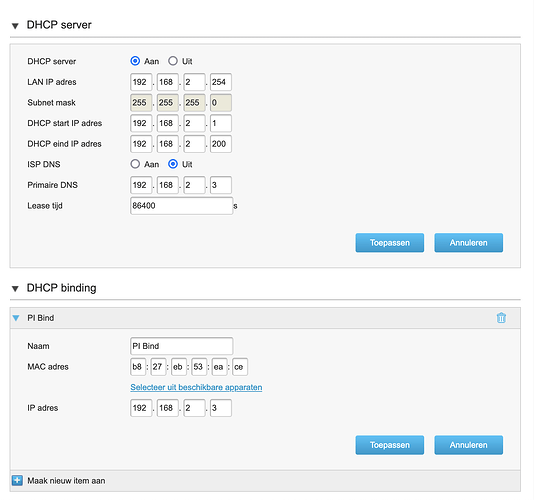
Default all other changes that you've made on the router and only enter the Pi-hole IP for "Primaire DNS" in the "DHCP server" section from the screenshot.
sudo pihole-FTL dhcp-discover
If still run into issues, post output for above one here pls?
lonkelo
November 17, 2023, 12:00pm
5
Okay. I've reset the router to factory settings and then set the PI-hole IP for "Primaire DNS" as per your suggestion. The Pi-hole dashboard now does show that my various devices are using the PI-hole, except for the Raspberry Pi itself (which is interestingly also in the list?). I've run the command you supplied, which yielded the following:
Scanning all your interfaces for DHCP servers
Timeout: 10 seconds
* Received 548 bytes from eth0:192.168.2.254
Offered IP address: 192.168.2.2
Server IP address: N/A
Relay-agent IP address: N/A
BOOTP server: Experiabox-V10
BOOTP file: (empty)
DHCP options:
Message type: DHCPOFFER (2)
netmask: 255.255.255.0
router: 192.168.2.254
dns-server: 192.168.2.3
dns-server: 192.168.2.254
domain-name: "home"
server-identifier: 192.168.2.254
lease-time: 86400 ( 1d )
broadcast: 192.168.2.255
--- end of options ---
DHCP packets received on interface eth0: 1
EDIT:
Your router with IP 192.168.2.254 is advertising its own IP for DNS to the clients alongside the Pi-hole IP 192.168.2.3 .
If you cant get the routers DHCP service to only advertise the single Pi-hole IP for DNS, you could opt to let Pi-hole take over DHCP services for your LAN:
EDIT:
lonkelo:
but not adds on Youtube
Oh Youtube ads cant be blocked as the ads are coming from the same domains as where the content is coming from.
1 Like
lonkelo
November 19, 2023, 11:20am
7
First of all, thanks for all the effort you're putting into helping me: much appreciated!
Secondly, as for getting the router to only advertise the Pi-hole IP for DNS: I've now set the Pi-hole to take over the DHCP services. This seems to work. I've re-run sudo pihole-FTL dhcp-discover by the way and this produced the following output:
Scanning all your interfaces for DHCP servers
Timeout: 10 seconds
DHCP packets received on interface eth0: 0
Is that correct?
As for youtube, pity, but I'll try one of your suggestions
1 Like
lonkelo:
Is that correct?
No its not.
grep DHCP_ACTIVE= /etc/pihole/setupVars.conf
sudo ss -nlup sport = 67
sudo nft list ruleset
grep '^ *interface' -A6 /etc/dhcpcd.conf
nmcli -f ipv4.method con show $(nmcli -t -f name con show --active)
sudo grep dnsmasq-dhcp /var/log/pihole.log | tail -10 | sed 's/:..:..:.. .*$//'
lonkelo
November 24, 2023, 11:47am
9
I've run it a couple of times: always get
Scanning all your interfaces for DHCP servers
Timeout: 10 seconds
DHCP packets received on interface eth0: 0
As for the output of the suggested six statements to run:
DHCP_ACTIVE=true
UNCONN 0 0 0.0.0.0:67 0.0.0.0:* users:(("pihole-FTL",pid=25637,fd=4))
table ip filter {
chain INPUT {
type filter hook input priority filter; policy drop;
counter packets 478315 bytes 61829138 jump ufw-before-logging-input
counter packets 478315 bytes 61829138 jump ufw-before-input
counter packets 6252 bytes 413359 jump ufw-after-input
counter packets 4844 bytes 155008 jump ufw-after-logging-input
counter packets 4844 bytes 155008 jump ufw-reject-input
counter packets 4844 bytes 155008 jump ufw-track-input
}
chain FORWARD {
type filter hook forward priority filter; policy drop;
counter packets 0 bytes 0 jump ufw-before-logging-forward
counter packets 0 bytes 0 jump ufw-before-forward
counter packets 0 bytes 0 jump ufw-after-forward
counter packets 0 bytes 0 jump ufw-after-logging-forward
counter packets 0 bytes 0 jump ufw-reject-forward
counter packets 0 bytes 0 jump ufw-track-forward
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
counter packets 397839 bytes 44953035 jump ufw-before-logging-output
counter packets 397839 bytes 44953035 jump ufw-before-output
counter packets 7636 bytes 525603 jump ufw-after-output
counter packets 7636 bytes 525603 jump ufw-after-logging-output
counter packets 7636 bytes 525603 jump ufw-reject-output
counter packets 7636 bytes 525603 jump ufw-track-output
}
chain ufw-before-logging-input {
}
chain ufw-before-logging-output {
}
chain ufw-before-logging-forward {
}
chain ufw-before-input {
iifname "lo" counter packets 356028 bytes 24600033 accept
ct state related,established counter packets 35210 bytes 16810122 accept
ct state invalid counter packets 123 bytes 6180 jump ufw-logging-deny
ct state invalid counter packets 123 bytes 6180 drop
meta l4proto icmp icmp type destination-unreachable counter packets 0 bytes 0 accept
meta l4proto icmp icmp type time-exceeded counter packets 0 bytes 0 accept
meta l4proto icmp icmp type parameter-problem counter packets 0 bytes 0 accept
meta l4proto icmp icmp type echo-request counter packets 0 bytes 0 accept
meta l4proto udp udp sport 67 udp dport 68 counter packets 3 bytes 1728 accept
counter packets 86951 bytes 20411075 jump ufw-not-local
meta l4proto udp ip daddr 224.0.0.251 udp dport 5353 counter packets 69468 bytes 18964496 accept
meta l4proto udp ip daddr 239.255.255.250 udp dport 1900 counter packets 0 bytes 0 accept
counter packets 17483 bytes 1446579 jump ufw-user-input
}
chain ufw-before-output {
oifname "lo" counter packets 356030 bytes 24600113 accept
ct state related,established counter packets 34173 bytes 19827319 accept
counter packets 7636 bytes 525603 jump ufw-user-output
}
chain ufw-before-forward {
ct state related,established counter packets 0 bytes 0 accept
meta l4proto icmp icmp type destination-unreachable counter packets 0 bytes 0 accept
meta l4proto icmp icmp type time-exceeded counter packets 0 bytes 0 accept
meta l4proto icmp icmp type parameter-problem counter packets 0 bytes 0 accept
meta l4proto icmp icmp type echo-request counter packets 0 bytes 0 accept
counter packets 0 bytes 0 jump ufw-user-forward
}
chain ufw-after-input {
meta l4proto udp udp dport 137 counter packets 888 bytes 79560 jump ufw-skip-to-policy-input
meta l4proto udp udp dport 138 counter packets 10 bytes 2287 jump ufw-skip-to-policy-input
meta l4proto tcp tcp dport 139 counter packets 0 bytes 0 jump ufw-skip-to-policy-input
meta l4proto tcp tcp dport 445 counter packets 0 bytes 0 jump ufw-skip-to-policy-input
meta l4proto udp udp dport 67 counter packets 412 bytes 137424 jump ufw-skip-to-policy-input
meta l4proto udp udp dport 68 counter packets 0 bytes 0 jump ufw-skip-to-policy-input
fib daddr type broadcast counter packets 98 bytes 39080 jump ufw-skip-to-policy-input
}
chain ufw-after-output {
}
chain ufw-after-forward {
}
chain ufw-after-logging-input {
limit rate 3/minute burst 10 packets counter packets 4844 bytes 155008 log prefix "[UFW BLOCK] "
}
chain ufw-after-logging-output {
}
chain ufw-after-logging-forward {
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 log prefix "[UFW BLOCK] "
}
chain ufw-reject-input {
}
chain ufw-reject-output {
}
chain ufw-reject-forward {
}
chain ufw-track-input {
}
chain ufw-track-output {
meta l4proto tcp ct state new counter packets 187 bytes 11668 accept
meta l4proto udp ct state new counter packets 7414 bytes 512271 accept
}
chain ufw-track-forward {
}
chain ufw-logging-deny {
ct state invalid limit rate 3/minute burst 10 packets counter packets 112 bytes 5608 return
limit rate 3/minute burst 10 packets counter packets 11 bytes 572 log prefix "[UFW BLOCK] "
}
chain ufw-logging-allow {
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 log prefix "[UFW ALLOW] "
}
chain ufw-skip-to-policy-input {
counter packets 1408 bytes 258351 drop
}
chain ufw-skip-to-policy-output {
counter packets 0 bytes 0 accept
}
chain ufw-skip-to-policy-forward {
counter packets 0 bytes 0 drop
}
chain ufw-not-local {
fib daddr type local counter packets 11231 bytes 1033220 return
fib daddr type multicast counter packets 74312 bytes 19119504 return
fib daddr type broadcast counter packets 1408 bytes 258351 return
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 jump ufw-logging-deny
counter packets 0 bytes 0 drop
}
chain ufw-user-input {
meta l4proto tcp tcp dport 36613 counter packets 11 bytes 588 accept
meta l4proto udp udp dport 36613 counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport { 80,443} counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport 8080 counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport 8888 counter packets 2371 bytes 441649 accept
meta l4proto udp udp dport 8888 counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport 53 counter packets 113 bytes 7232 accept
meta l4proto udp udp dport 53 counter packets 8736 bytes 583751 accept
}
chain ufw-user-output {
}
chain ufw-user-forward {
}
chain ufw-user-logging-input {
}
chain ufw-user-logging-output {
}
chain ufw-user-logging-forward {
}
chain ufw-user-limit {
limit rate 3/minute counter packets 0 bytes 0 log prefix "[UFW LIMIT BLOCK] "
counter packets 0 bytes 0 reject
}
chain ufw-user-limit-accept {
counter packets 0 bytes 0 accept
}
}
table ip6 filter {
chain INPUT {
type filter hook input priority filter; policy drop;
counter packets 85500 bytes 50843352 jump ufw6-before-logging-input
counter packets 85500 bytes 50843352 jump ufw6-before-input
counter packets 189 bytes 21168 jump ufw6-after-input
counter packets 0 bytes 0 jump ufw6-after-logging-input
counter packets 0 bytes 0 jump ufw6-reject-input
counter packets 0 bytes 0 jump ufw6-track-input
}
chain FORWARD {
type filter hook forward priority filter; policy drop;
counter packets 0 bytes 0 jump ufw6-before-logging-forward
counter packets 0 bytes 0 jump ufw6-before-forward
counter packets 0 bytes 0 jump ufw6-after-forward
counter packets 0 bytes 0 jump ufw6-after-logging-forward
counter packets 0 bytes 0 jump ufw6-reject-forward
counter packets 0 bytes 0 jump ufw6-track-forward
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
counter packets 19246 bytes 1591033 jump ufw6-before-logging-output
counter packets 19246 bytes 1591033 jump ufw6-before-output
counter packets 1591 bytes 163139 jump ufw6-after-output
counter packets 1591 bytes 163139 jump ufw6-after-logging-output
counter packets 1591 bytes 163139 jump ufw6-reject-output
counter packets 1591 bytes 163139 jump ufw6-track-output
}
chain ufw6-before-logging-input {
}
chain ufw6-before-logging-output {
}
chain ufw6-before-logging-forward {
}
chain ufw6-before-input {
iifname "lo" counter packets 6 bytes 615 accept
rt type 0 counter packets 0 bytes 0 drop
ct state related,established counter packets 16148 bytes 31544900 accept
meta l4proto ipv6-icmp icmpv6 type echo-reply counter packets 0 bytes 0 accept
ct state invalid counter packets 0 bytes 0 jump ufw6-logging-deny
ct state invalid counter packets 0 bytes 0 drop
meta l4proto ipv6-icmp icmpv6 type destination-unreachable counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type packet-too-big counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type time-exceeded counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type parameter-problem counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type echo-request counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type nd-router-solicit ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type nd-router-advert ip6 hoplimit 255 counter packets 1596 bytes 191456 accept
meta l4proto ipv6-icmp icmpv6 type nd-neighbor-solicit ip6 hoplimit 255 counter packets 663 bytes 47736 accept
meta l4proto ipv6-icmp icmpv6 type nd-neighbor-advert ip6 hoplimit 255 counter packets 4867 bytes 350304 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type ip6 hoplimit 1 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type ip6 hoplimit 1 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type ip6 hoplimit 1 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type counter packets 0 bytes 0 accept
meta l4proto udp ip6 saddr fe80::/10 ip6 daddr fe80::/10 udp sport 547 udp dport 546 counter packets 0 bytes 0 accept
meta l4proto udp ip6 daddr ff02::fb udp dport 5353 counter packets 62031 bytes 18687173 accept
meta l4proto udp ip6 daddr ff02::f udp dport 1900 counter packets 0 bytes 0 accept
counter packets 189 bytes 21168 jump ufw6-user-input
}
chain ufw6-before-output {
oifname "lo" counter packets 6 bytes 615 accept
rt type 0 counter packets 0 bytes 0 drop
ct state related,established counter packets 8973 bytes 662527 accept
meta l4proto ipv6-icmp icmpv6 type destination-unreachable counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type packet-too-big counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type time-exceeded counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type parameter-problem counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type echo-request counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type echo-reply counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type nd-router-solicit ip6 hoplimit 255 counter packets 6 bytes 336 accept
meta l4proto ipv6-icmp icmpv6 type nd-neighbor-advert ip6 hoplimit 255 counter packets 5445 bytes 391824 accept
meta l4proto ipv6-icmp icmpv6 type nd-neighbor-solicit ip6 hoplimit 255 counter packets 32 bytes 2304 accept
meta l4proto ipv6-icmp icmpv6 type nd-router-advert ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type counter packets 3193 bytes 370288 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type ip6 hoplimit 255 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type ip6 hoplimit 1 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type ip6 hoplimit 1 counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp ip6 saddr fe80::/10 icmpv6 type ip6 hoplimit 1 counter packets 0 bytes 0 accept
counter packets 1591 bytes 163139 jump ufw6-user-output
}
chain ufw6-before-forward {
rt type 0 counter packets 0 bytes 0 drop
ct state related,established counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type destination-unreachable counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type packet-too-big counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type time-exceeded counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type parameter-problem counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type echo-request counter packets 0 bytes 0 accept
meta l4proto ipv6-icmp icmpv6 type echo-reply counter packets 0 bytes 0 accept
counter packets 0 bytes 0 jump ufw6-user-forward
}
chain ufw6-after-input {
meta l4proto udp udp dport 137 counter packets 0 bytes 0 jump ufw6-skip-to-policy-input
meta l4proto udp udp dport 138 counter packets 0 bytes 0 jump ufw6-skip-to-policy-input
meta l4proto tcp tcp dport 139 counter packets 0 bytes 0 jump ufw6-skip-to-policy-input
meta l4proto tcp tcp dport 445 counter packets 0 bytes 0 jump ufw6-skip-to-policy-input
meta l4proto udp udp dport 546 counter packets 189 bytes 21168 jump ufw6-skip-to-policy-input
meta l4proto udp udp dport 547 counter packets 0 bytes 0 jump ufw6-skip-to-policy-input
}
chain ufw6-after-output {
}
chain ufw6-after-forward {
}
chain ufw6-after-logging-input {
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 log prefix "[UFW BLOCK] "
}
chain ufw6-after-logging-output {
}
chain ufw6-after-logging-forward {
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 log prefix "[UFW BLOCK] "
}
chain ufw6-reject-input {
}
chain ufw6-reject-output {
}
chain ufw6-reject-forward {
}
chain ufw6-track-input {
}
chain ufw6-track-output {
meta l4proto tcp ct state new counter packets 26 bytes 2080 accept
meta l4proto udp ct state new counter packets 1555 bytes 160079 accept
}
chain ufw6-track-forward {
}
chain ufw6-logging-deny {
ct state invalid limit rate 3/minute burst 10 packets counter packets 0 bytes 0 return
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 log prefix "[UFW BLOCK] "
}
chain ufw6-logging-allow {
limit rate 3/minute burst 10 packets counter packets 0 bytes 0 log prefix "[UFW ALLOW] "
}
chain ufw6-skip-to-policy-input {
counter packets 189 bytes 21168 drop
}
chain ufw6-skip-to-policy-output {
counter packets 0 bytes 0 accept
}
chain ufw6-skip-to-policy-forward {
counter packets 0 bytes 0 drop
}
chain ufw6-user-input {
meta l4proto tcp tcp dport 36613 counter packets 0 bytes 0 accept
meta l4proto udp udp dport 36613 counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport { 80,443} counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport 8080 counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport 8888 counter packets 0 bytes 0 accept
meta l4proto udp udp dport 8888 counter packets 0 bytes 0 accept
meta l4proto tcp tcp dport 53 counter packets 0 bytes 0 accept
meta l4proto udp udp dport 53 counter packets 0 bytes 0 accept
}
chain ufw6-user-output {
}
chain ufw6-user-forward {
}
chain ufw6-user-logging-input {
}
chain ufw6-user-logging-output {
}
chain ufw6-user-logging-forward {
}
chain ufw6-user-limit {
limit rate 3/minute counter packets 0 bytes 0 log prefix "[UFW LIMIT BLOCK] "
counter packets 0 bytes 0 reject
}
chain ufw6-user-limit-accept {
counter packets 0 bytes 0 accept
}
}
interface eth0
static ip_address=192.168.2.3/24
static routers=192.168.2.254
static domain_name_servers=
Error: NetworkManager is not running.
Error: NetworkManager is not running.
Nov 24 12:40:59 dnsmasq-dhcp[25637]: DHCP, IP range 192.168.2.201 -- 192.168.2.251, lease time 1d
UFW is active.
sudo ufw disable
Flush the current rules:
sudo nft flush ruleset
And try again:
sudo pihole-FTL dhcp-discover
If that works, you'll have to look into your UFW firewall setup to get the pihole-FTL command to report properly:
To enable UFW and rules again:
sudo ufw enable
Did you restart/reboot Pi-hole just before running above command (maybe causing the logs to rotate)?
pi@ph5b:~ $ sudo grep dnsmasq-dhcp /var/log/pihole.log | tail -10 | sed 's/:..:..:.. .*$//'
Nov 24 17:31:20 dnsmasq-dhcp[13215]: DHCPINFORM(eth0) 10.0.0.11 00:1e:0b
Nov 24 17:31:20 dnsmasq-dhcp[13215]: DHCPACK(eth0) 10.0.0.11 00:1e:0b
[..]
Did it hand out any leases?
awk '{print $1,$3}' /etc/pihole/dhcp.leases
EDIT: I changed above awk a bit to include timestamp!
system
December 15, 2023, 4:58pm
11
This topic was automatically closed 21 days after the last reply. New replies are no longer allowed.