Tracking a client's DNS requests is possible if that client is using Pi-hole for DNS, regardless where the service announcing Pi-hole resides.
Offering a public wifi may also require you to monitor client activities under some legislations, and to strike the balance, prior consent could be key (e.g. by showing a banner that informs a client that their activities are to be tracked if they use your service).
But don't take my word for it, those are just hints - really, as a business, you want to seek professional legal advice on proper precautions for your country.
In the event of a real crash, Pi-hole would log that to /var/log/FTL.log.
So far, you have not shared any evidence of an actual crash.
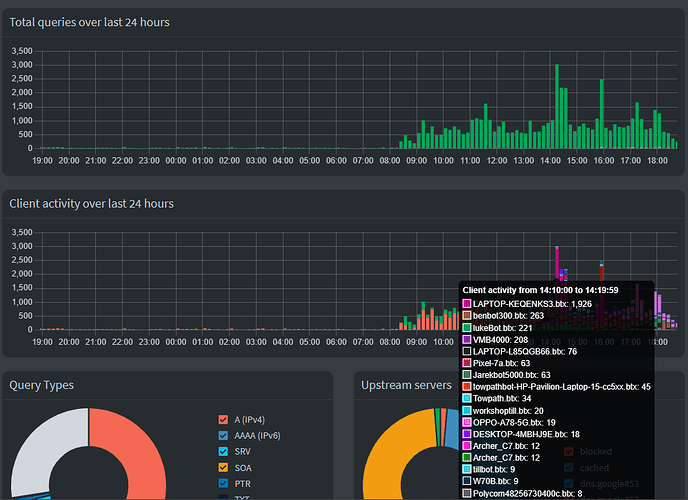
On the contrary, your screenshots demonstrate Pi-hole's DNS server to have been operational all the time, handling requests before, during and after your peaks.
It is thus unclear what your issue is.
How did you achieve that?
Pi-hole's own rate limit operates on the overall number of DNS requests per time interval, i.e. you can't rate limit individual clients.
In case your issue would be with excessive DNS requests, blocking a client completely may have an adverse effect, as that may prompt even more (misbehaving) client software to excessively repeat DNS requests for blocked domains.
Or could your issue perhaps be with client DHCP broadcasts rather than DNS?
E.g. you mention
Above does not disclose which requests you'd be referring to (DHCP, DNS, HTTP, ...)?
Please try to explain your actual issue, and provide additional relevant details.
Answering my previous question could also help.