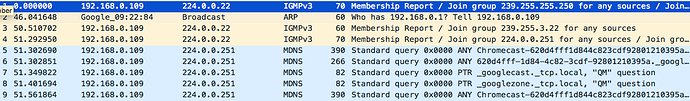
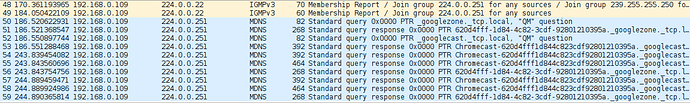
So I did that, and used host 192.168.0.109 (IP of the Chromecast) as a filter. I've uploaded the pcapng file to my Google Drive here. All I see are IGMP, ARP and multicast MDNS queries to IPs like 224.0.0.22 and 224.0.0.251.
I also did a dig:
dig google-public-dns-a.google.com
; <<>> DiG 9.12.3-P1 <<>> google-public-dns-a.google.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41565
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;google-public-dns-a.google.com. IN A
;; ANSWER SECTION:
google-public-dns-a.google.com. 3842 IN A 8.8.8.8
;; Query time: 5 msec
;; SERVER: 192.168.0.2#53(192.168.0.2)
;; WHEN: Tue Apr 30 22:47:25 EDT 2019
;; MSG SIZE rcvd: 75
But only see this the Pi Hole logs:
Apr 30 22:47:26 dnsmasq[26679]: query[A] google-public-dns-a.google.com from 192.168.0.129
Apr 30 22:47:26 dnsmasq[26679]: cached google-public-dns-a.google.com is 8.8.8.8
Apr 30 22:47:26 dnsmasq[26679]: query[A] 3.client-channel.google.com from 192.168.0.129
Apr 30 22:47:26 dnsmasq[26679]: forwarded 3.client-channel.google.com to 1.0.0.1
Apr 30 22:47:26 dnsmasq[26679]: reply 3.client-channel.google.com is 209.85.232.189
I see another user posted elsewhere about the MDNS queries.
Edit: capture from a Pi is very similar: