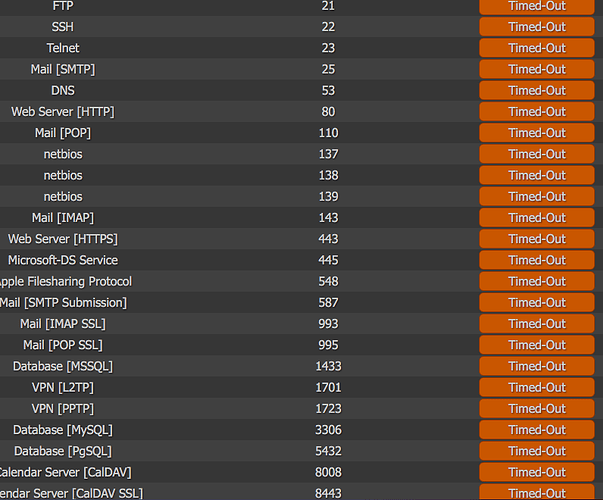
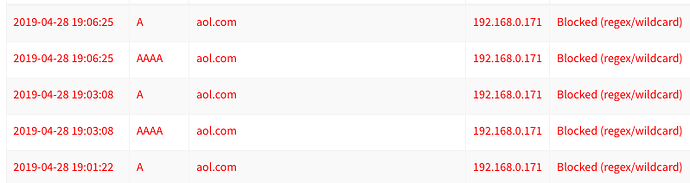
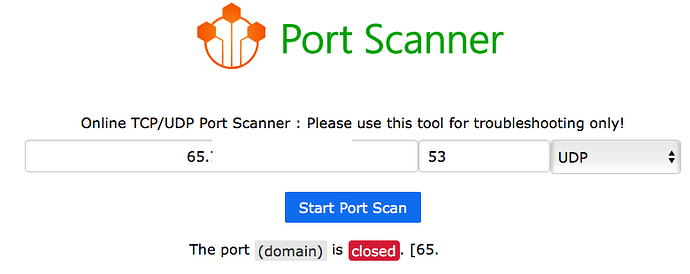
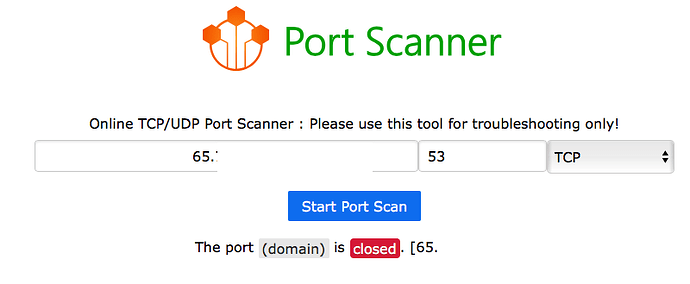
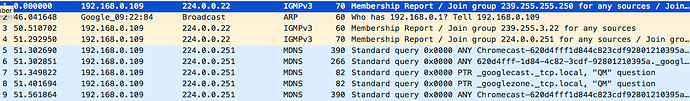
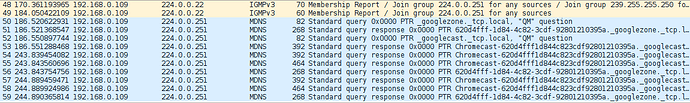
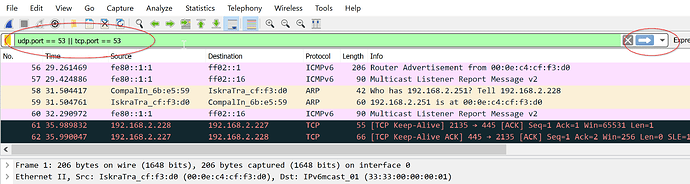
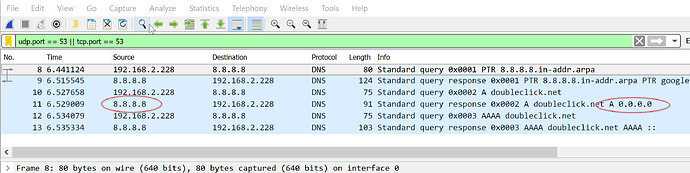
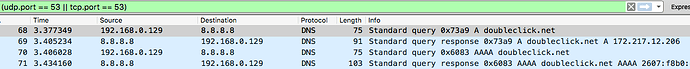
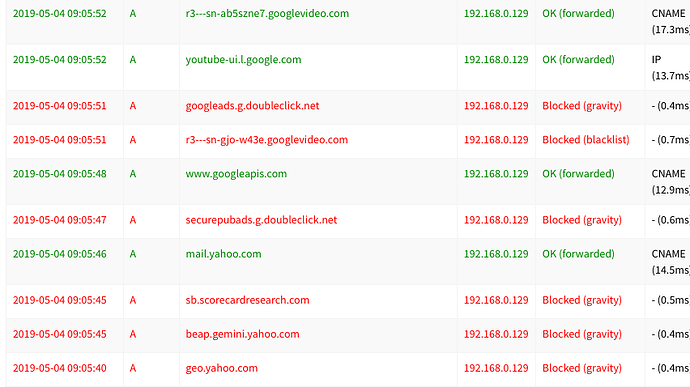
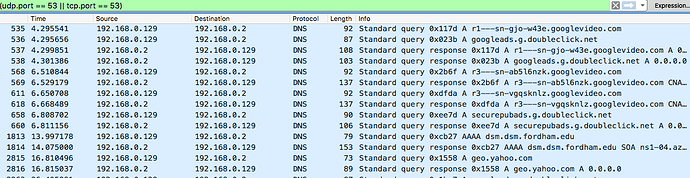
I've posted results from a few minutes of the suggested command sudo tcpdump -npi eth0 -vvv host 192.168.0.2 and port 53 on my Pi.
The Pi IP address is 192.168.0.2. The Chromecast is 192.168.0.250. I have this
route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.0.1 0.0.0.0 UG 202 0 0 eth0
8.8.4.4 192.168.0.2 255.255.255.255 UGH 0 0 0 eth0
8.8.8.8 192.168.0.2 255.255.255.255 UGH 0 0 0 eth0
192.168.0.0 0.0.0.0 255.255.255.0 U 202 0 0 eth0
But the Chromecast IP, 192.168.0.250, is not showing in the tcpdump.
I also have the suggestions from the Chromecast (Don’t) Phone Home thread, so I have <?php header("HTTP/1.0 204 No Content"); ?> and the entry in /etc/hosts.
I don't see any traffic going to 8.8.8.8 nor 8.8.4.4. I have an Arris cable modem so I had to configure DNS to point to the Pi, and I enabled Port Forwarding so UDP port 53 goes to the Pi IP which is 192.168.0.2.
Pings from the Pi to the Google Public DNS addresses timeout:pi@raspberrypi:~ $ ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
From 192.168.0.2 icmp_seq=1 Destination Host Unreachable
From 192.168.0.2 icmp_seq=2 Destination Host Unreachable
pi@raspberrypi:~ $ ping 8.8.4.4
PING 8.8.4.4 (8.8.4.4) 56(84) bytes of data.
From 192.168.0.2 icmp_seq=1 Destination Host Unreachable
A nslookup via my Mac's Network Utility to 8.8.8.8 results in:
Lookup has started…
8.8.4.4 -> google-public-dns-b.google.com
Cloudflare and Comodo are the selected DNS options in pi-hole. I have this iptables rule too:
iptables -L -n -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT udp -- 8.8.4.4 0.0.0.0/0 udp dpt:53 to:10.141.165.1
DNAT udp -- 8.8.8.8 0.0.0.0/0 udp dpt:53 to:10.141.165.1
DNAT tcp -- 192.168.1.100 0.0.0.0/0 tcp dpt:53 to:10.141.165.1
DNAT udp -- 0.0.0.0/0 8.8.8.8 udp dpt:53 to:10.141.165.1
DNAT udp -- 0.0.0.0/0 8.8.4.4 udp dpt:53 to:10.141.165.1
And some more nslookup's from my Mac:
nslookup
> server 8.8.8.8
Default server: 8.8.8.8
Address: 8.8.8.8#53
> ping google.com
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
Name: google.com
Address: 172.217.3.110
Name: google.com
Address: 2607:f8b0:4006:818::200e
When visiting google.com from my Mac, IP 192.168.0.171 I see these logs:
Apr 26 00:29:07 dnsmasq[2168]: query[A] www.gstatic.com from 192.168.0.171
Apr 26 00:29:07 dnsmasq[2168]: forwarded www.gstatic.com to 1.0.0.1
Apr 26 00:29:07 dnsmasq[2168]: reply www.gstatic.com is 172.217.10.227
Apr 26 00:29:07 dnsmasq[2168]: query[A] adservice.google.com from 192.168.0.171
Apr 26 00:29:07 dnsmasq[2168]: /etc/pihole/gravity.list adservice.google.com is 0.0.0.0
Apr 26 00:29:07 dnsmasq[2168]: query[A] apis.google.com from 192.168.0.171
Apr 26 00:29:07 dnsmasq[2168]: forwarded apis.google.com to 1.0.0.1
Apr 26 00:29:07 dnsmasq[2168]: reply apis.google.com is <CNAME>
Apr 26 00:29:07 dnsmasq[2168]: reply plus.l.google.com is 172.217.7.14
Apr 26 00:29:08 dnsmasq[2168]: query[A] a1507.b.akamai.net from 192.168.0.171
Apr 26 00:29:08 dnsmasq[2168]: forwarded a1507.b.akamai.net to 1.0.0.1
Apr 26 00:29:08 dnsmasq[2168]: reply a1507.b.akamai.net is 104.70.178.115
Apr 26 00:29:08 dnsmasq[2168]: reply a1507.b.akamai.net is 104.70.178.104
Apr 26 00:29:08 dnsmasq[2168]: query[A] pancake.cdn-apple.com.akadns.net from 192.168.0.171
Apr 26 00:29:08 dnsmasq[2168]: forwarded pancake.cdn-apple.com.akadns.net to 1.0.0.1
Apr 26 00:29:08 dnsmasq[2168]: reply pancake.cdn-apple.com.akadns.net is <CNAME>
Apr 26 00:29:08 dnsmasq[2168]: reply pancake.g.aaplimg.com is 17.253.97.202
Apr 26 00:29:08 dnsmasq[2168]: reply pancake.g.aaplimg.com is 17.253.97.204
Is there anything else I can check to see this is working as desired? How can I use dig and/or nslookup to test this and what should I look for in the Query Logs?