Expected Behaviour:
RPi 5 with pi-hole 5.18.2 and unbound 1.17.1-2+deb12u2 on new dietpi system
Unbound and pi-hole were installed using the dietpi installer.
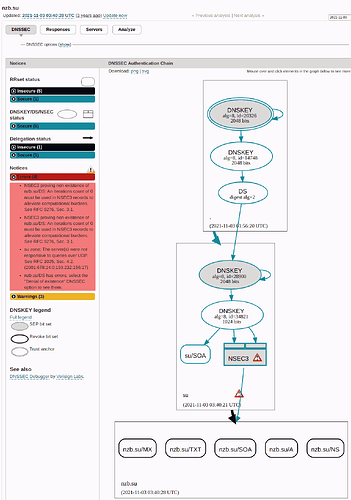
Most queries seem to be working, and nzb.su should resolve.
Actual Behaviour:
nzb.su returns a SERVFAIL
dig @localhost -p 5335 a nzb.su
;; communications error to ::1#5335: connection refused
;; communications error to ::1#5335: connection refused
;; communications error to ::1#5335: connection refused
;; communications error to 127.0.0.1#5335: timed out
; <<>> DiG 9.18.24-1-Debian <<>> @localhost -p 5335 a nzb.su
; (2 servers found)
;; global options: +cmd
;; no servers could be reached
Based on many other threads I've read, I tried running sudo /usr/sbin/unbound -ddd -vvv -c /etc/unbound/unbound.conf while the following dig query was executed:
dig dietpi.com @127.0.0.1 -p 5335 a nzb.su
The dig output is the same:
dietpi@DietPi:/etc/systemd$ dig @127.0.0.1 -p 5335 a nzb.su ;; communications error to 127.0.0.1#5335: timed out
;; communications error to 127.0.0.1#5335: timed out
;; communications error to 127.0.0.1#5335: timed out
; <<>> DiG 9.18.24-1-Debian <<>> @127.0.0.1 -p 5335 a nzb.su
; (1 server found)
;; global options: +cmd
;; no servers could be reached
However, the same command with instagram.com works:
dig @127.0.0.1 -p 5335 a instagram.com
; <<>> DiG 9.18.24-1-Debian <<>> @127.0.0.1 -p 5335 a instagram.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10622
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;instagram.com. IN A
;; ANSWER SECTION:
instagram.com. 300 IN A 31.13.65.174
;; Query time: 72 msec
;; SERVER: 127.0.0.1#5335(127.0.0.1) (UDP)
;; WHEN: Sat Jun 01 18:14:36 EDT 2024
;; MSG SIZE rcvd: 58
Output of /etc/unbound/unbound.conf.d/dietpi.conf:
# https://nlnetlabs.nl/documentation/unbound/unbound.conf/
server:
# Do not daemonize, to allow proper systemd service control and status estimation.
do-daemonize: no
# A single thread is pretty sufficient for home or small office instances.
num-threads: 1
# Logging: For the sake of privacy and performance, keep logging at a minimum!
# - Verbosity 2 and up practically contains query and reply logs.
verbosity: 0
log-queries: no
log-replies: no
# - If required, uncomment to log to a file, else logs are available via "journalctl -u unbound".
#logfile: "/var/log/unbound.log"
# Set interface to "0.0.0.0" to make Unbound listen on all network interfaces.
# Set it to "127.0.0.1" to listen on requests from the same machine only, useful in combination with Pi-hole.
interface: 127.0.0.1
# Default DNS port is "53". When used with Pi-hole, set this to e.g. "5335", since "5353" is used by mDNS already.
port: 5335
# Control IP ranges which should be able to use this Unbound instance.
# The DietPi defaults permit access from official local network IP ranges only, hence requests from www are denied.
access-control: 0.0.0.0/0 refuse
access-control: 10.0.0.0/8 allow
access-control: 127.0.0.1/8 allow
access-control: 172.16.0.0/12 allow
access-control: 192.168.0.0/16 allow
access-control: ::/0 refuse
access-control: ::1/128 allow
access-control: fd00::/8 allow
access-control: fe80::/10 allow
# Private IP ranges, which shall never be returned or forwarded as public DNS response.
# NB: 127.0.0.1/8 is sometimes used by adblock lists, hence DietPi by default allows those as response.
private-address: 10.0.0.0/8
private-address: 172.16.0.0/12
private-address: 192.168.0.0/16
private-address: 169.254.0.0/16
private-address: fd00::/8
private-address: fe80::/10
# Define protocols for connections to and from Unbound.
# NB: Disabling IPv6 does not disable IPv6 IP resolving, which depends on the clients request.
do-udp: yes
do-tcp: yes
do-ip4: yes
do-ip6: no
# DNS root server information file. Updated monthly via cron job: /etc/cron.monthly/dietpi-unbound
root-hints: "/var/lib/unbound/root.hints"
# Maximum number of queries per second
ratelimit: 1000
# Defend against and print warning when reaching unwanted reply limit.
unwanted-reply-threshold: 10000
# Set EDNS reassembly buffer size to match new upstream default, as of DNS Flag Day 2020 recommendation.
edns-buffer-size: 1232
# Increase incoming and outgoing query buffer size to cover traffic peaks.
so-rcvbuf: 4m
so-sndbuf: 4m
# Hardening
harden-glue: yes
harden-dnssec-stripped: yes
harden-algo-downgrade: yes
harden-large-queries: yes
harden-short-bufsize: yes
# Privacy
use-caps-for-id: yes # Spoof protection by randomising capitalisation
rrset-roundrobin: yes
qname-minimisation: yes
minimal-responses: yes
hide-identity: yes
identity: "Server" # Purposefully a dummy identity name
hide-version: yes
# Caching
cache-min-ttl: 300
cache-max-ttl: 86400
serve-expired: yes
neg-cache-size: 4M
prefetch: yes
prefetch-key: yes
msg-cache-size: 50m
rrset-cache-size: 100m
The output of my verbose unbound window while running the dig command to nzb.su is here: dietpi@DietPi:~$ sudo /usr/sbin/unbound -ddd -vvv -c /etc/unbound/unbound.conf - Pastebin.com
Any ideas what else I can try? I tried asking on the DietPi Forums but didn't have any success.