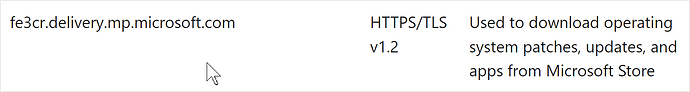
from this (v.1909) document:
the domain (fe3cr.delivery.mp.microsoft.com) doesn't appear anymore in this (v.21H1) document, but the wildcard does (*.delivery.mp.microsoft.com)
forcing a windows update causes a bypass attempt -> packet capture:
23 280.265594 192.168.2.228 162.159.36.2 DNS 91 Standard query 0x92a4 A fe3cr.delivery.mp.microsoft.com
24 280.266415 192.168.2.228 162.159.36.2 DNS 91 Standard query 0x02d3 AAAA fe3cr.delivery.mp.microsoft.com
25 280.271603 162.159.36.2 192.168.2.228 DNS 179 Standard query response 0x92a4 A fe3cr.delivery.mp.microsoft.com CNAME fe3.delivery.mp.microsoft.com CNAME glb.cws.prod.dcat.dsp.trafficmanager.net A 40.125.122.151
26 280.272082 162.159.36.2 192.168.2.228 DNS 191 Standard query response 0x02d3 AAAA fe3cr.delivery.mp.microsoft.com CNAME fe3.delivery.mp.microsoft.com CNAME glb.cws.prod.dcat.dsp.trafficmanager.net AAAA 2603:1020:2:3::67
dig -x 162.159.36.2 -> NXDOMAIN
host 162.159.36.2 -> Host 2.36.159.162.in-addr.arpa. not found: 3(NXDOMAIN)
ping 162.159.36.2 -> reply
not really getting much information here (NS server name)
any ideas?