Expected Behaviour:
When I whitelist a domain, it will allow me to get that value in DNS.
I installed Pi-Hole through TrueNAS (not TrueCharts). It runs as a Docker container on their Kubernetes app infrastructure.
It's not machine-dependent either. My PC with two NICs and my phone on Wi-Fi both experience the same issue.
Actual Behaviour:
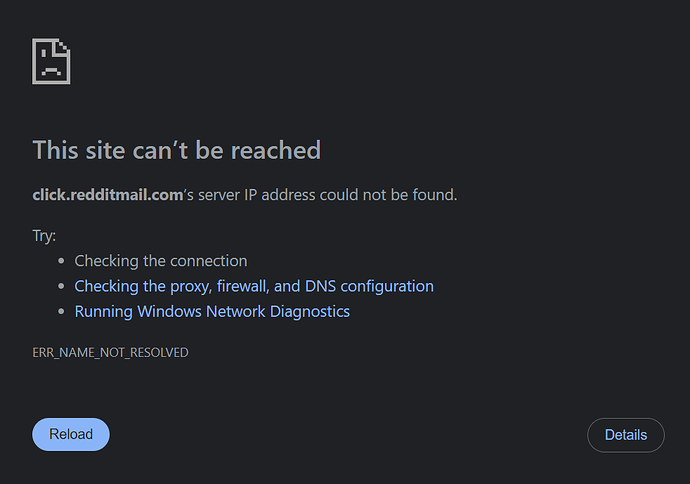
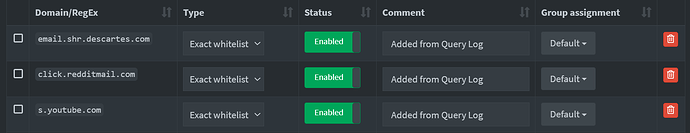
Pi-Hole allows me to whitelist domains, but for some reason, they still show up as blocked even in the Query Log where I whitelisted the domain.
Even if I disable the blocklists in Pi-Hole, I still can't get to those domains.
I'm also making sure to run ipconfig /flushdns each time before I try. Is there anything special I need to do when running it?
When I do an nslookup using 1.1.1.1, I'm also seeing 0.0.0.0 as the response, but that shouldn't be correct. So it's like all DNS queries are going through Pi-Hole from my NICs.
If I query from my PC to my phone's mobile hotspot to its LTE connection, then I can get IPs back in my DNS query.