- Dell OptiPlex 7040 Micro - Intel i5 6500T 2.50GHz; 16GB DDR4 RAM; 500GB PCIe 3rd Gen SSD
- Ubuntu running Pi-hole [v5.15.5] | FTL [v5.21] | Web Interface [v5.18.4]
- Setup as follows Ethernet Broadband Connection --> TP Link Router Archer VR500v --> Tenda Nova MW3 Mesh
- Dell Optiplex 7040 running pihole is connected to the TP Link Router
- Tenda Nova Mesh is broadcasting a separate wifi network to which most devices on the home network are connected.
Expected Behaviour:
Expecting to be getting around 8-25% queries blocked based on what people have on youtube/google images
Actual Behaviour:
Getting 0.1% of queries blocked (was getting around 10% yesterday)
Debug Token:
https://tricorder.pi-hole.net/zeqLQ4lF/
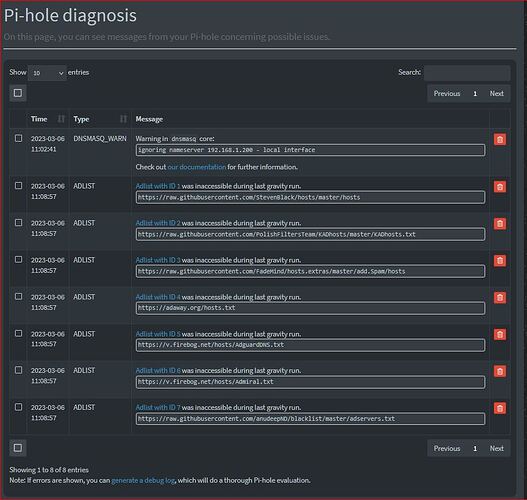
Some Adlists are giving Adlist with ID X was inaccessible during last gravity run. Not sure if this is affecting the percentage - however this has only been in the last 1-2hrs and I am under the impression the stats shown are for the last 24hrs.
edit: I have noticed now that when I go to speedtest.net the ads are not being blocked - these were being blocked before
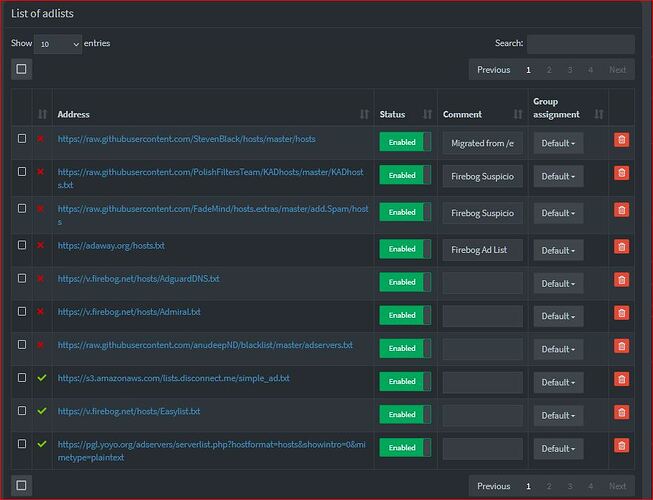
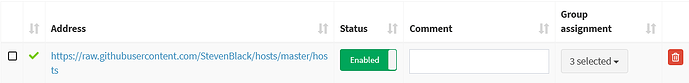
**EDIT: based on the help received below - the problem was that I had created custom groups but not assigned any of these custom groups to my adlists. Once assigning all my devices back to default group the blocking was working.
The "adlist with ID X was inaccessible during last gravity run" problem was resolved by going to tools > gravity update as per chrislph advice.
Many thanks to jfb, rdwebdesign and chrislph for their quick responses and helping me address the issues!!!**