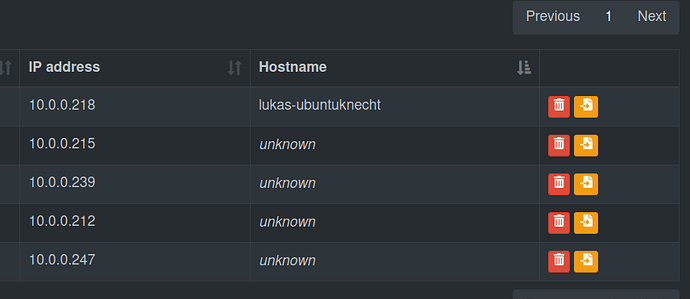
The issue I am facing:
The issue looks like a standard problem, but still, I cant figure out what to do. I moved in to a new place with new router. I have a PiHole which is also used as DHCP-server.
The addressing scheme is 10.0.0.0/24, the routers IP address is x.138. The Pi hole is 10.0.0.1.
It seems to work for some devices, but it does not resolve all of my devices by its name, just showing "unknown" for all of them. (all but one are unknown) Interestingly, it seems like the "unknown" devices don't receive blocking, while the one device which blocks correctly (a Wifi connected Ubuntu notebook) is also resolved.
However, if I look into the settings of "unknown" devices, the seem to know that they rely on the Pi hole for DNS server, since it shows its IP-address.
Details about my system:
In the router, I set the DHCP to the IP-address of my Pi. I did not change the DNS settings.
The /etc/dhcpcd.conf looks like this:
# A sample configuration for dhcpcd.
# See dhcpcd.conf(5) for details.
# Allow users of this group to interact with dhcpcd via the control socket.
#controlgroup wheel
# Inform the DHCP server of our hostname for DDNS.
hostname
# Use the hardware address of the interface for the Client ID.
clientid
# or
# Use the same DUID + IAID as set in DHCPv6 for DHCPv4 ClientID as per RFC4361.
# Some non-RFC compliant DHCP servers do not reply with this set.
# In this case, comment out duid and enable clientid above.
#duid
# Persist interface configuration when dhcpcd exits.
persistent
# Rapid commit support.
# Safe to enable by default because it requires the equivalent option set
# on the server to actually work.
option rapid_commit
# A list of options to request from the DHCP server.
option domain_name_servers, domain_name, domain_search, host_name
option classless_static_routes
# Respect the network MTU. This is applied to DHCP routes.
option interface_mtu
# Most distributions have NTP support.
#option ntp_servers
# A ServerID is required by RFC2131.
require dhcp_server_identifier
# Generate SLAAC address using the Hardware Address of the interface
#slaac hwaddr
# OR generate Stable Private IPv6 Addresses based from the DUID
slaac private
# Example static IP configuration:
#interface eth0
#static ip_address=192.168.0.10/24
#static ip6_address=fd51:42f8:caae:d92e::ff/64
#static routers=192.168.0.1
#static domain_name_servers=192.168.0.1 8.8.8.8 fd51:42f8:caae:d92e::1
# It is possible to fall back to a static IP if DHCP fails:
# define static profile
#profile static_eth0
#static ip_address=192.168.1.23/24
#static routers=192.168.1.1
#static domain_name_servers=192.168.1.1
# fallback to static profile on eth0
#interface eth0
#fallback static_eth0
interface eth0
static ip_address=10.0.0.1/24
static routers=10.0.0.138
static domain_name_servers=9.9.9.9
The /etc/pihole/setupVars.conf looks like this:
PIHOLE_INTERFACE=eth0
QUERY_LOGGING=true
INSTALL_WEB_SERVER=true
INSTALL_WEB_INTERFACE=true
LIGHTTPD_ENABLED=true
CACHE_SIZE=10000
DNS_FQDN_REQUIRED=true
DNS_BOGUS_PRIV=true
DNSMASQ_LISTENING=local
WEBPASSWORD=
BLOCKING_ENABLED=true
DHCP_ACTIVE=true
DHCP_START=10.0.0.201
DHCP_END=10.0.0.251
DHCP_ROUTER=10.0.0.138
DHCP_LEASETIME=24
PIHOLE_DOMAIN=lan
DHCP_IPv6=false
DHCP_rapid_commit=false
PIHOLE_DNS_1=9.9.9.9
PIHOLE_DNS_2=149.112.112.112
PIHOLE_DNS_3=2620:fe::fe
PIHOLE_DNS_4=2620:fe::9
DNSSEC=false
REV_SERVER=false
So I activated the DHCP settings in the Pi Hole, as seen above. I did not actively change something about the IPv6 settings, since I am not sure if I need that (which would be a second, more irrelevant question)
What I have changed since installing Pi-hole:
Nothing but the settings I explained above.