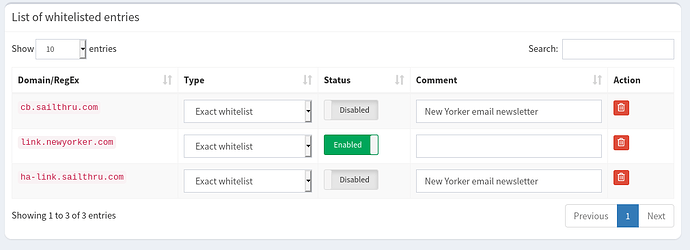
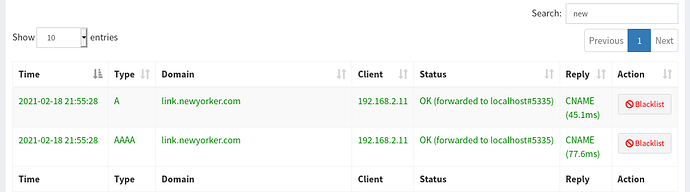
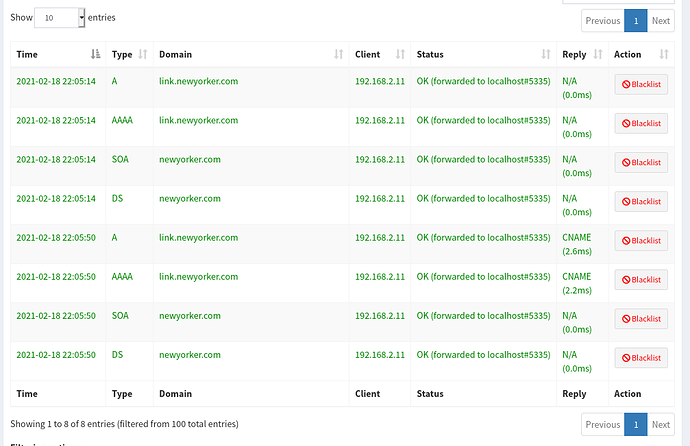
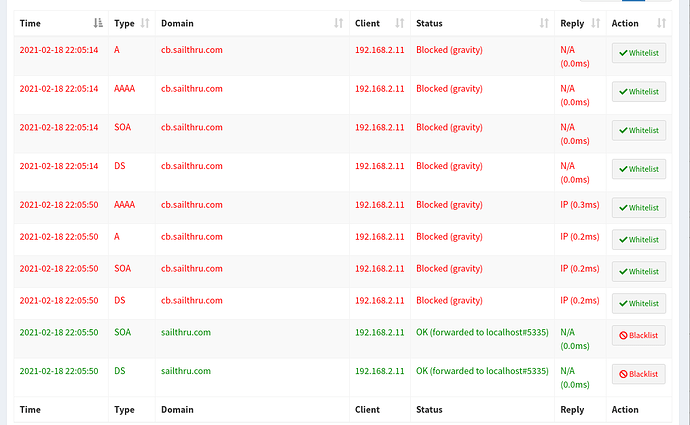
I'm trying to whitelist a domain that comes from clicking a link through an email (link.newyorker.com), but it gets blocked because it's actually a CNAME to some other links on the standard blocklists.
There seems to be other topics similar to this one, but I wasn't able to solve my problem by reading them. If I understand it correctly, I should be able to whiltelist link.newyorker.com alone and reach the other CNAME domains without a problem. I only want to allow the underlying CNAME records when they originate from queries in my whitelist
<snip>
Feb 18 21:49:25 dnsmasq[29782]: query[A] link.newyorker.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: forwarded link.newyorker.com to 127.0.0.1
Feb 18 21:49:25 dnsmasq[29782]: query[AAAA] link.newyorker.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: forwarded link.newyorker.com to 127.0.0.1
Feb 18 21:49:25 dnsmasq[29782]: reply link.newyorker.com is <CNAME>
Feb 18 21:49:25 dnsmasq[29782]: reply cb.sailthru.com is <CNAME>
Feb 18 21:49:25 dnsmasq[29782]: reply ha-link.sailthru.com is NODATA-IPv6
Feb 18 21:49:25 dnsmasq[29782]: query[SOA] newyorker.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: forwarded newyorker.com to 127.0.0.1
Feb 18 21:49:25 dnsmasq[29782]: reply link.newyorker.com is <CNAME>
Feb 18 21:49:25 dnsmasq[29782]: reply cb.sailthru.com is <CNAME>
Feb 18 21:49:25 dnsmasq[29782]: reply ha-link.sailthru.com is 3.226.166.212
Feb 18 21:49:25 dnsmasq[29782]: reply ha-link.sailthru.com is 162.208.117.53
Feb 18 21:49:25 dnsmasq[29782]: query[DS] newyorker.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: forwarded newyorker.com to 127.0.0.1
Feb 18 21:49:25 dnsmasq[29782]: query[AAAA] cb.sailthru.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: gravity blocked cb.sailthru.com is ::
Feb 18 21:49:25 dnsmasq[29782]: query[A] cb.sailthru.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: gravity blocked cb.sailthru.com is 0.0.0.0
Feb 18 21:49:25 dnsmasq[29782]: query[SOA] cb.sailthru.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: gravity blocked cb.sailthru.com is 0.0.0.0
Feb 18 21:49:25 dnsmasq[29782]: query[DS] cb.sailthru.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: gravity blocked cb.sailthru.com is 0.0.0.0
Feb 18 21:49:25 dnsmasq[29782]: query[SOA] sailthru.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: forwarded sailthru.com to 127.0.0.1
Feb 18 21:49:25 dnsmasq[29782]: query[DS] sailthru.com from 192.168.2.11
Feb 18 21:49:25 dnsmasq[29782]: forwarded sailthru.com to 127.0.0.1
<snip>
$ dig link.newyorker.com @8.8.8.8
; <<>> DiG 9.16.11 <<>> link.newyorker.com @8.8.8.8
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10430
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;link.newyorker.com. IN A
;; ANSWER SECTION:
link.newyorker.com. 229 IN CNAME cb.sailthru.com.
cb.sailthru.com. 59 IN CNAME ha-link.sailthru.com.
ha-link.sailthru.com. 59 IN A 3.226.166.212
ha-link.sailthru.com. 59 IN A 162.208.117.53
;; Query time: 27 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: do feb 18 21:51:39 CET 2021
;; MSG SIZE rcvd: 127
If I whitelist all the domains that link.newyorker.com resolves to I am able to get through, but I want to selectively whitelist sailthru for just queries that originate from link.newyorker.com.
Via the UI it looks like the queries are successful (to newyorker.com) but my browser still shows a black screen, and dig shows that the CNAME record for sailthru is blocked.
$ dig link.newyorker.com
; <<>> DiG 9.16.11 <<>> link.newyorker.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48475
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;link.newyorker.com. IN A
;; ANSWER SECTION:
link.newyorker.com. 59 IN CNAME cb.sailthru.com.
cb.sailthru.com. 2 IN A 0.0.0.0
;; Query time: 7 msec
;; SERVER: 127.0.0.53#53(127.0.0.53)
;; WHEN: do feb 18 21:59:29 CET 2021
;; MSG SIZE rcvd: 89
How do I whitelist link.newyorker.com without whitelisting the other sailthru links? Is this possible?