Beatiful job on v6.
Runs great on rpi4.
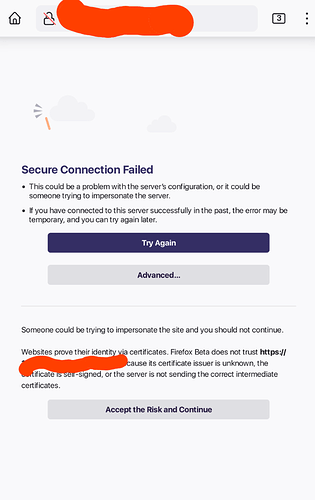
just one nag from firefox android.
I fried all these in about:config disabling etc
security.ssl.enable_ocsp_stapling
security.tls.insecure_fallback_hosts = piholes ip and + admin + login link
security.insecure_field_warning.contextual.enabled
security.ssl3.dhe_rsa_aes_128_sha
security.ssl3.dhe_rsa_aes_256_sha
Everytime iust click proceed. I like and want https but firefox for android is a nag about this.
any suggeations? ty.
DL6ER
January 15, 2024, 7:40pm
2
This is expected. In the end, Firefox is right: You are using a self-signed certificate here which has not been added to the trusted certificates of your device (so there is no "trust" on it), hence, this is not "secure" as you would not really notice when someone MITM s you.
If other browser you have tried do not say this, they are taking less care of your safety.
Thank you, how would i get the certificate from pihole?
DL6ER
January 16, 2024, 8:48pm
4
It is stored in /etc/pihole, look out for tls.crt
The PEM file in the same directory has both the certificate as well as the private TLS key, this is not needed on the phone and should only be stored on the server.
DL6ER
January 19, 2024, 5:39pm
5
While trying to create a walk-through for you, I realized that this isn't actually possible with Firefox (mobile) because it won't accept self-signed certificates. I, hence, proposed a change how Pi-hole generates its own SSL/TLS certificate (proposal not yet accepted!) and wrote a guide here:
https://deploy-preview-980--pihole-docs.netlify.app/api/tls/
Note that this needs a special version of FTL, too:
pi-hole:development-v6 ← pi-hole:tweak/x509_ca
opened 02:42PM - 17 Jan 24 UTC
# What does this implement/fix?
Currently, Pi-hole's mechanism to create a se… lf-signed certificate, well, creates a self-signed certificate. Recent user questions have, however, revealed that there is software (most worth mentioning is Firefox) not liking (as in: explicitly discouraging, sometimes even preventing) the usage of such self-signed certificates. Adding the certificate to said browsers (so the web interface page is considered "safe") is not possible in this case.
This PR changes the way Pi-hole generates the TLS certificate for itself. We go a more traditional way by first creating a (self-signed) root certificate authority (CA) and then using this CA to sign a second certificate we specifically create for the TLS web server. The generated CA is exported to a file and can then be imported into Firefox, Chrome, etc.
If you are using `curl` or friends, nothing changes - you can still use the certificate PEM file as you were used before.
> [!NOTE]
> Pi-hole will not recreate already existing self-signed certificates. If you want to use this new certificates, you will have to run
> ```
> sudo pihole-FTL --gen-x509 /etc/pihole/tls.pem
> ```
> to force recreation of the certificate. Possibly with a domain if you want to use a domain different from `pi.hole`, e.g.
> ```
> sudo pihole-FTL --gen-x509 /etc/pihole/tls.pem pihole.lan
> ```
---
**Related issue or feature (if applicable):** N/A
**Pull request in [docs](https://github.com/pi-hole/docs) with documentation (if applicable):** https://github.com/pi-hole/docs/pull/980
---
**By submitting this pull request, I confirm the following:**
1. I have read and understood the [contributors guide](https://docs.pi-hole.net/guides/github/contributing/), as well as this entire template. I understand which branch to base my commits and Pull Requests against.
2. I have commented my proposed changes within the code.
3. I am willing to help maintain this change if there are issues with it later.
4. It is compatible with the [EUPL 1.2 license](https://opensource.org/licenses/EUPL-1.1)
5. I have squashed any insignificant commits. ([`git rebase`](http://gitready.com/advanced/2009/02/10/squashing-commits-with-rebase.html))
## Checklist:
- [x] The code change is tested and works locally.
- [x] I based my code and PRs against the repositories `developmental` branch.
- [x] I [signed off](https://docs.pi-hole.net/guides/github/how-to-signoff/) all commits. Pi-hole enforces the [DCO](https://docs.pi-hole.net/guides/github/dco/) for all contributions
- [x] I [signed](https://docs.github.com/en/authentication/managing-commit-signature-verification/signing-commits) all my commits. Pi-hole requires signatures to verify authorship
- [x] I have read the above and my PR is ready for review.
5 Likes
Wow, thank for that hard work. I'm not sure if I should do the guide, Very thorough.
nero355
February 15, 2025, 7:30pm
7