The issue I am facing:
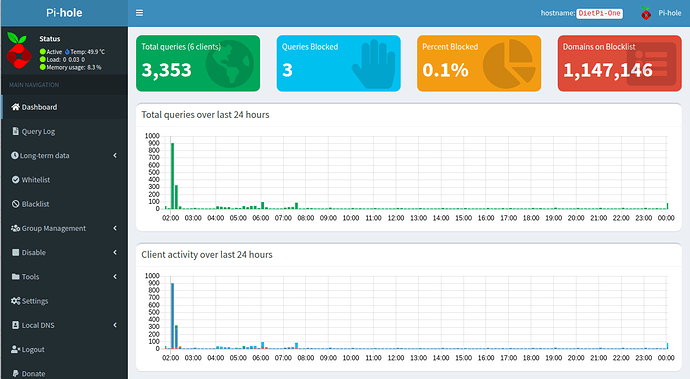
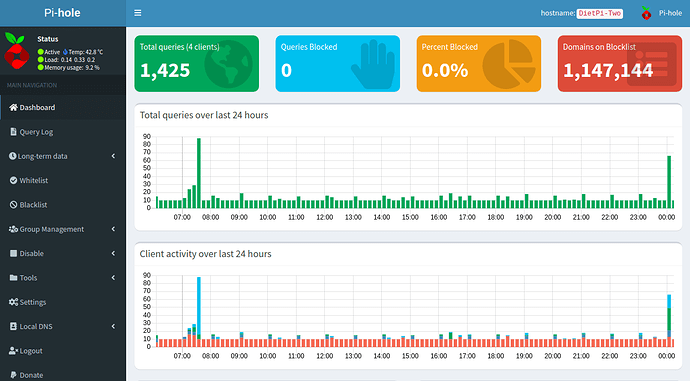
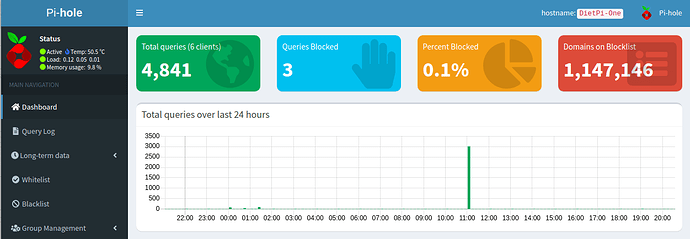
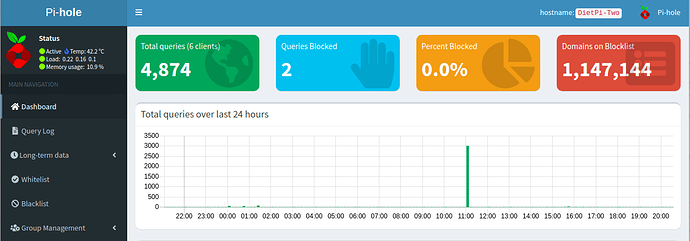
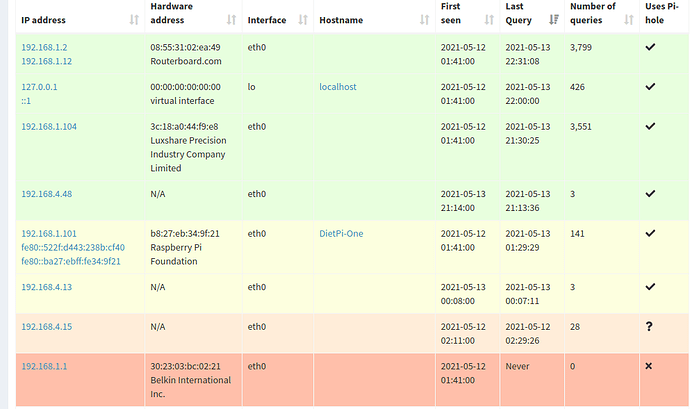
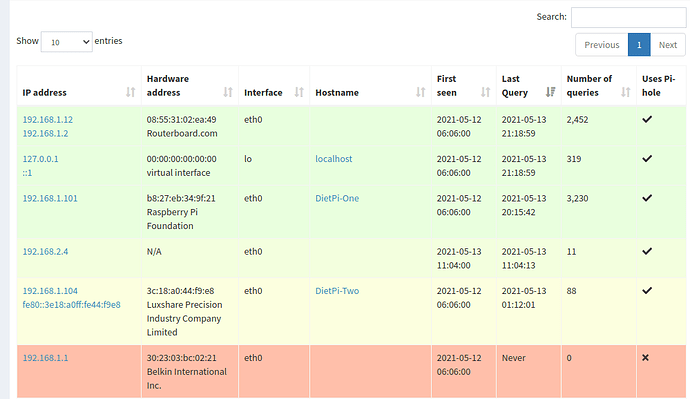
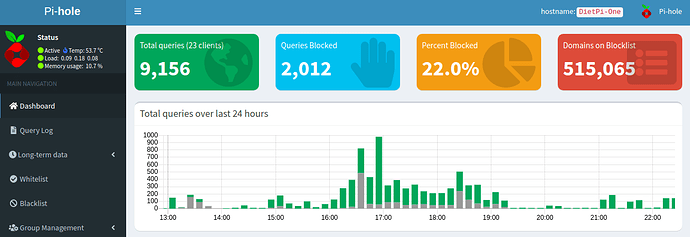
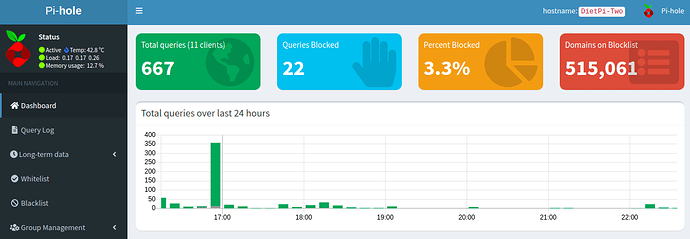
Pihole is not blocking ads properly despite reinstalling multiple times. It will only block ads on the pi itself. The query statistics are also wrong as I have a 35+ client network that is all routing through pihole via my router, so I should be getting at least 50,000-100,000+ queries a day but it only shows queries for my Network Switch as well as my Secondary Pihole(Backup/Load Balancing) server. Network so far works fine in terms of internet connection but both Piholes are not blocking ads whatsoever(Unless the requests are coming from the pihole itself). I have tested both pi devices with Both Raspbian and DietPi and have gotten the same results unfortunately.
Debug Token for 3B+(DietPi-One): 3b0pedmbvl
Debug Token for Zero W(DietPi-Two): zptjczsg1g
Details about my system:
Dietpi-One is a Raspberry Pi 3b+ connected to ethernet also with wifi disabled.
Dietpi-Two is a Raspberry Pi Zero W with wifi disabled and connected to ethernet cable via a dongle.
These are STRICTLY Pihole devices only.
What I have changed since installing Pi-hole:
The only other things I have installed are stubby, and UFW.
From what I understand, according to my pihole debug logs, I have properly opened the ports necessary for Pihole to function. Stubby(For sending my dns over tls, DoT) is also listening on a different port than Pihole. Also Avahi-daemon is installed so I can easily ssh into the piholes as well.(Also Software installs mentioned above are mirrored on both Piholes.) This is also on a clean new install thats about a day old on both devices. Other than that, that is it for my setup.