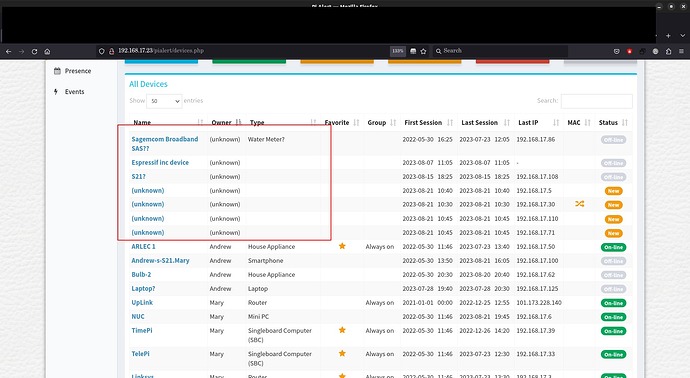
I am seeing these MAC addresses in/on my list often.
The top one I named. Searching their company name and what they make, I can believe/suspect that is what it is.
But what sort of concerns me is HOW ARE THEY GETTING CONNECTED?
My WiFi has a good password so I don't understand what this is telling me.
I have (now) taken extra steps and basically if those MAC addresses DO CONNECT, all/any packets from them are dropped.
But could someone help me understand why/how they are getting into my network's list?
Thanks in advance.
You may find more information by looking at Pi-hole's own overview in Tools > Network. That will also show the MAC addresses and identify the vendor where possible, as well as when a client was first seen, the last time it queried and how many queries it made.
Apple iPhones have a feature which will create a randomised MAC address and use that to present to the network. If enough time passes since it was last used, it creates a new randomised MAC next time it is on that network. This is for privacy, to prevent the phone's actual MAC leaving footprints on networks, especially guest networks.
I believe other smartphones and tablets adopt this same behaviour. It may be this behaviour which is triggering PiAlert and accounting for the "unknown" entries, since these MAC addresses are usually not linked to a vendor. It would be worth checking the settings for each such device and checking if they are indeed doing this, and if you can disable it on trusted networks such as home.
If you have a specific IP which is online right now, you can perform a scan of its common ports and this may help determine what it is. Eg,
nmap 192.168.17.5
If you saw, for example, port 80 is open, that implies it is running a web server on your network, possibly for admin. So you could go to http://192.168.17.5 in a browser and see what appears. It might be the the login page for your doorbell device, for example.
Your Pi-hole makes a good platform to run this from since it's already installed and up. If nmap is not installed you can install it with
sudo apt install nmap
Thanks.
I am not able to catch any of the devices when they are online.
Or, more correctly, I am not seeing the online notification when I am looking at the page.
Would it help if I removed the new device indicator to see if they are online?
As the status is occupied with new rather than online or offline.
Yes, I've been into Tools/Network and that's where I theorised the water meter for that MAC address.
I guess that isn't the right word at this point as it is more a hypothesis than a theory.
My mobile phone does have such a feature and I believe I've turned it off.
To test myself I looked at the page and connected to my network. Nothing indicated it was connected or had any activities on the unknown MAC address - but then there is the possible problem they are still flagged a new so that blocks the showing of online.
Another interesting question/observation is the one with the squiggly = sign which is indicative of a random MAC when I open the tools/network page.
How is that determined?
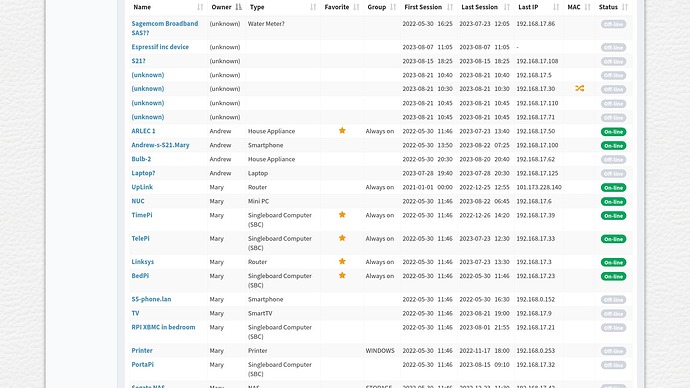
For the sake of trying to help, I've cleared all the new devices so they aren't new anymore.
I connected my smart phone to my network.
This is what I see.
You can see the phone listed.
No new/listed activity on any of the other unknown devices. Only the phone's.
Your observation is not related to Pi-hole in particular nor DNS in general.
Like your screenshots, they are about PiAlert, which seems to be a tool that specialises in WIFI / LAN intrusion detection.
You should ask your questions in the PiAlert forums.
I agree, but when I search for PiAlert forums, I get links to here.
Sorry.
Stuck with where to ask.
You describe un-identifiable devices on your network.
PiAlert should know how to tell whether your observation is something to worry about - especially since it is their tool that brought those potential intruders to your attention.
That's PiAlert's domain.
As Bucking_Horn has said, these are PiAlert related questions. I'm afraid I have no experience with it, having never used it.
You may find it easier to stick with Pi-hole's own interface in order to track down devices on your network.
The aforementioned Tools > Network view is very good and will identify vendors where it can, as well as show if they are active or not (see the background colours listed at the bottom). You can click hostnames or IP addresses in there and see their queries for the last 24 hours in the Query Log. This will give clues as to what the device is.
The Long-term Data > Query Log will let you search your long-term query database for IP addresses and hostnames for much longer – by default 365 days.
Using a combination of these – plus knowledge of any people who visited and joined your network, plus the domains the devices were querying, plus any open ports they might have if they are online now, as well as turning off MAC randomisation just for your own trusted devices – you will likely be able to identify all the devices on your network.
The more nuclear option is to take all devices offline except for your router, Pi-hole and the computer you are using to connect to Pi-hole's admin interface. Then go to Settings > Flush network table. This will clear the Network page, and a moment later you will see these three devices. If you see any more you have likely forgotten about something.
Now you can slowly, one by one, reconnect your other devices and observe them in the Network page (refresh the page to see new devices). This will let you see what they are calling themselves, as well as identify any MAC randomisation taking place from smartphones or tablets.
You can do all this using Pi-hole's own interface and tools. PiAlert looks interesting but there's a risk that normal, modern network activity is being presented as an "intrusion" and can cause panic, such as your concerned opening post. In practice I suspect these are normal devices trusted by you and it's just a matter of identifying them, which is a bit of detective work but worth doing.