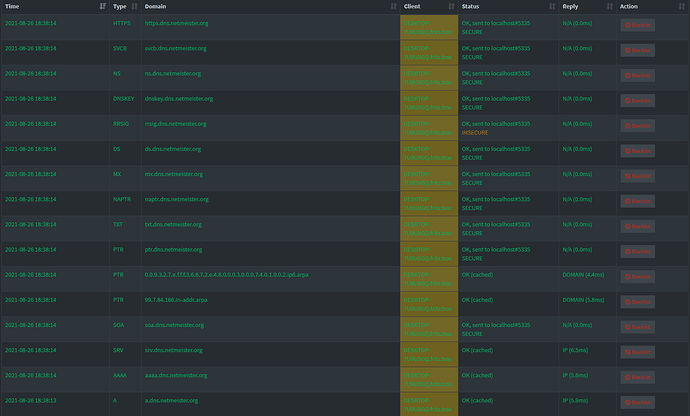
So I've been playing around with this a little and the problem extends to even the known query types. All queries are affected if the answer doesn't fit one of the predefined reply types.
But even the DS and DNSKEY queries don't have DNSSEC as a reply type here for some reason.
There aren't any reply types that would fit any of these queries here, so N/A is better than nothing I guess, but something more descriptive like DATA would be nice just to have any feedback about the result of the query. Also all affected queries were forwarded again instead of being answered from cache. The screenshot doesn't show this but this is the second round of queries (testscript below). The response time is again always 0.0 ms even though the queries were forwarded.
# Test script to quickly test for arbitrary resource records
pihole="192.168.178.15"
for i in a aaaa srv soa ptr txt naptr mx ds rrsig dnskey ns svcb https
do
if [ "$i" = ptr ]; then
ip4="$(dig +short a netmeister.org)"
ip6="$(dig +short aaaa netmeister.org)"
echo "$(dig +noall +answer @${pihole} -x ${ip4})"
echo "$(dig +noall +answer @${pihole} -x ${ip6})"
fi
if [ "$i" = svcb ]; then
j="TYPE64"
elif [ "$i" = https ]; then
j="TYPE65"
else
j="$i"
fi
echo "$(dig +noall +answer @${pihole} ${j} ${i}.dns.netmeister.org)"
done
# Output of above script
a.dns.netmeister.org. 1158 IN A 166.84.7.99
aaaa.dns.netmeister.org. 1168 IN AAAA 2001:470:30:84:e276:63ff:fe72:3900
srv.dns.netmeister.org. 1246 IN SRV 0 1 80 panix.netmeister.org.
soa.dns.netmeister.org. 1254 IN SOA panix.netmeister.org. jschauma.netmeister.org. 2021072312 3600 300 3600000 3600
99.7.84.166.in-addr.arpa. 1255 IN PTR panix.netmeister.org.
0.0.9.3.2.7.e.f.f.f.3.6.6.7.2.e.4.8.0.0.0.3.0.0.0.7.4.0.1.0.0.2.ip6.arpa. 1254 IN PTR panix.netmeister.org.
ptr.dns.netmeister.org. 1265 IN PTR ptr.dns.netmeister.org.
txt.dns.netmeister.org. 592 IN TXT "Format: <text>"
txt.dns.netmeister.org. 592 IN TXT "Descriptive text. Completely overloaded for all sorts of things. RFC1035 (1987)"
naptr.dns.netmeister.org. 1284 IN NAPTR 20 10 "s" "http+N2L+N2C+N2R" "" www.netmeister.org.
naptr.dns.netmeister.org. 1284 IN NAPTR 10 10 "u" "smtp+E2U" "!.*([^.]+[^.]+)$!mailto:postmaster@$1!i" .
mx.dns.netmeister.org. 1292 IN MX 50 panix.netmeister.org.
ds.dns.netmeister.org. 1299 IN DS 56393 13 2 BD36DD608262A026083721FA19E2F7B474F531BB3179CC00A0C38FF0 0CA11657
rrsig.dns.netmeister.org. 1308 IN RRSIG TXT 13 4 3600 20210902104320 20210819095136 56039 dns.netmeister.org. 6VhgJLJXR8f8VUPyC0v5EcS17Z/TfDIdVF7f8L9SceRvSfqz5NMzVD3E aMGN7DaEezXdBhqGaf/KFZxKufmIvA==
rrsig.dns.netmeister.org. 1308 IN RRSIG NSEC 13 4 3600 20210908211756 20210825205219 56039 dns.netmeister.org. 59eCCJ//Y1O69REgNOry9WB+XKNGMATN6EJ6mqtSqj8H31gKI8Dm2+pj FKHVfj5dJV62LVI9tPQHYSJVb/evdA==
dnskey.dns.netmeister.org. 1317 IN DNSKEY 257 3 13 XEn4q8CbG2a4Hw47Ih244BDkwY1tOuprXWKEzMyLPtjO9iIRVt4HLLbx 9YaeaYzRcH91mvCstP8I5liQ0Mn1bA==
ns.dns.netmeister.org. 1324 IN NS panix.netmeister.org.
svcb.dns.netmeister.org. 1343 IN TYPE64 \# 85 2D6E20312070616E69782E6E65746D6569737465722E6F72672E2069 70763668696E743D22323030313A3437303A33303A38343A65323736 3A363366663A666537323A333930302220706F72743D223838383822 0A
https.dns.netmeister.org. 1351 IN TYPE65 \# 25 2D6E2030207777772E6E65746D6569737465722E6F72672E0A
https.dns.netmeister.org. 1351 IN TYPE65 \# 123 2D6E2031202E20616C706E3D2268332C683222206970763668696E74 3D22323030313A3437303A33303A38343A653237363A363366663A66 6537323A333930302220706F72743D22383038302220656368636F6E 6669673D225A57356A636E6C776447566B49474E7361575675644342 6F5A57787362776F3D220A