Don't know if I understand what you mean. I have 2 pi-hole's and 1 USG-pro
1.- I installed this script in the USG to have ad-block in a different way right inside my USG: https://community.ui.com/questions/HowTo-Ad-blocking-using-dnsmasq-d-instead-of-etc-hosts/1598a96d-28af-4f3f-ab96-97bccdb897b3 What I don't like about this script is that I don't have statistic and have to review the logs to have some control.
2.- I configure the USG:
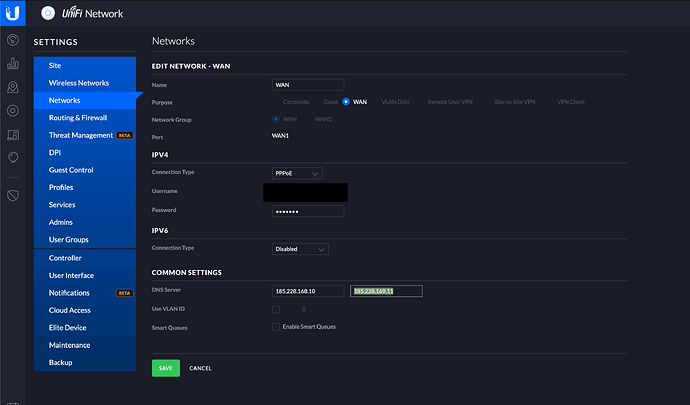
2.1.- Unifi Controller / Settings / Network / WAN --> Edit.
2.2.- In DNS Servers fill with the DNS servers that you will be using, Not the pi-holes IP, but the DNS forwarders you may need. I.E I'm using now the cleanBrowsing DNS servers: 185.228.168.10 and 185.228.169.11:
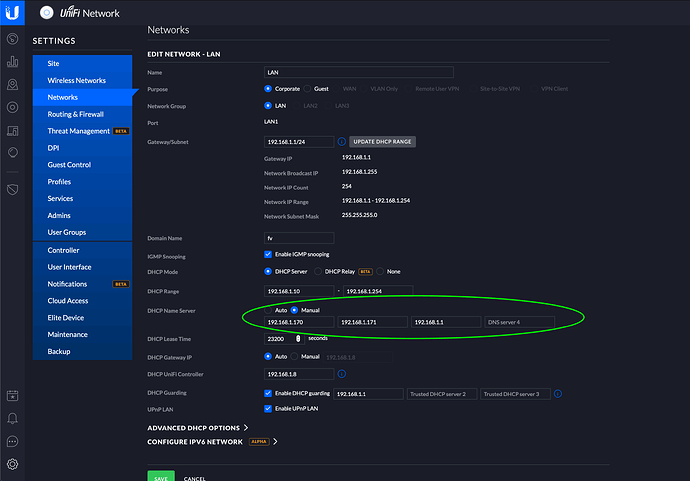
2.3.- Unifi Controller / Settings / Network / LAN --> Edit.
2.4.- Enable DHCP server and provide DHCP name server manual with the IP's of your PiHole's and your USG IP as secondary DNS or Tertiary if you are using 2 PiHole's:
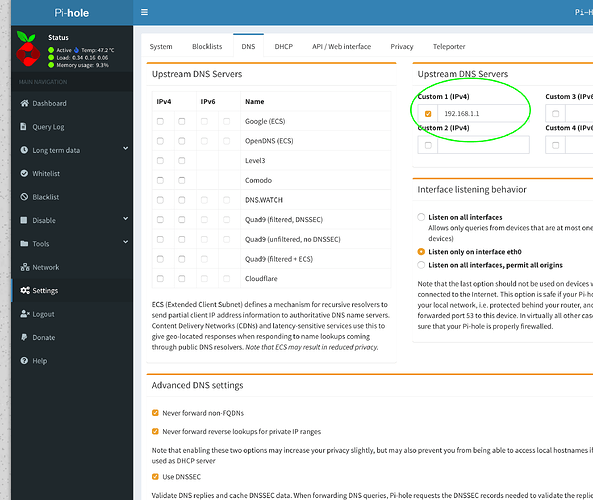
3.- Configure the PiHole via admin panel / Settings /DNS in every Pihole you own and configure as Custom IPV4 with the IP of your USG (in my case 192.168.1.1):
Now everything should work fine.
Despite this configuration, anyone in your network can bypass it (parental control speaking), by changing the DNS in the computer / phone or being hardcoded inside some devices (TV's and IOT's mostly). To avoid that, you can use the config.gateway.json file in the Unifi controller and then provision the USG:
{
"service": {
"nat": {
"rule": {
"1": {
"description": "Redirect DNS queries to USG",
"destination": {
"port": "53",
"address": ["!192.168.1.1"]
},
"source": {
"address": ["!192.168.1.1"]
},
"inside-address": {
"address": ["192.168.1.1"],
"port": "53"
},
"inbound-interface": ["eth0"],
"protocol": "tcp_udp",
"type": "destination"
},
"5001": {
"description": "Translate reply back",
"destination": {
"address": ["192.168.1.1"],
"port": "53"
},
"outbound-interface": ["eth0"],
"protocol": "tcp_udp",
"type": "masquerade"
}
}
}
}
}
With that code, if anyone tries to bypass the auto-assigned DNS, it will be redirected to the USG DNS.
With this configuration, you can have a PiHole and if it hangs, you can still have DNS resolution working with ad-blocking, but without statistics. Once you reboot the Pihole, you can have statistics back.
Hope this helps!