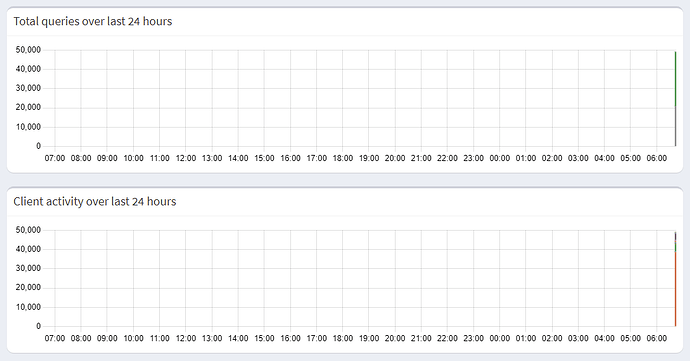
Your initial graph seems to show a sudden spike of about 50,000 DNS requests, potentially dwarfing smaller numbers to not be visible in that graph.
Those API results would have been most useful if run directly after such a spike, as they may not reflect the situation at the time of your post anymore.
A sudden spike may be caused by DNS loops, and you may indeed have closed such a loop in two places if your router would use Pi-hole as its upstream DNS server (in addition to distributing it as local DNS server via DHCP, which your DHCP server does).
*** [ DIAGNOSING ]: contents of /etc/dnsmasq.d
-rw-r--r-- 1 root root 1.6K Nov 18 08:33 /etc/dnsmasq.d/01-pihole.conf
server=208.67.222.222
server=208.67.220.220
server=192.168.1.1
rev-server=192.168.1.0/24,192.168.1.1
For once, you are using your router as one of Pi-hole's upstreams, which would fully close a loop if it's used. This may well trigger a sudden surge on a restart, when Pi-hole is probing all its upstreams for the fastest responding one.
You should remove 192.168.1.1 from your Pi-hole's upstreams via Settings | DNS.
You have also enabled Pi-hole's Conditional Forwarding, which may close a partial DNS loop for local names neither known by Pi-hole nor your router.
This may happen if a client would be in the habit of sending such a request, which makes it a lot less likely to occur than a full loop.
Bur your debug log shows also some peculiar networking I probably need help to understand - your Pi-hole host carries two IPv4 addresses for the same eth0 interface:
*** [ DIAGNOSING ]: Networking
[✓] IPv4 address(es) bound to the eth0 interface:
192.168.1.196/24
192.168.1.2/24
Your DHCP server is distributing both of those, but also two public OpenDNS ones, for a total of 4 different DNS servers:
*** [ DIAGNOSING ]: Discovering active DHCP servers (takes 10 seconds)
Scanning all your interfaces for DHCP servers
* Received 315 bytes from eth0:192.168.1.1
Offered IP address: 192.168.1.196
DHCP options:
Message type: DHCPOFFER (2)
dns-server: 192.168.1.2
dns-server: 208.67.222.222
dns-server: 192.168.1.196
dns-server: 208.67.220.220
router: 192.168.1.1
--- end of options ---
Stating two private range IP addresses for the very same interface of the same machine in the same subnet seems somehow redundant?
And stating those public resolvers would allow your clients to by-pass your Pi-hole via OpenDNS.
I also notice that your Pi-hole host system seems to be using only those OpenDNS resolvers:
*** [ DIAGNOSING ]: contents of /etc
lrwxrwxrwx 1 root root 39 Aug 1 2020 /etc/resolv.conf -> ../run/systemd/resolve/stub-resolv.conf
nameserver 208.67.222.222
nameserver 208.67.220.220
That's a sensible configuration, as it would allow your host system to run updates and repairs, even if Pi-hole's DNS service would be inoperational at times.
This is accompanied by some interesting routing - your routing table has a remarkable count of single target entries:
*** [ DIAGNOSING ]: Network routing table
default via 192.168.1.1 dev eth0 proto dhcp src 192.168.1.196 metric 100
default via 192.168.1.1 dev eth0 src 192.168.1.2 metric 202
192.168.1.0/24 dev eth0 proto dhcp scope link src 192.168.1.2 metric 202
192.168.1.1 dev eth0 proto dhcp scope link src 192.168.1.196 metric 100
192.168.1.2 dev eth0 proto dhcp scope link src 192.168.1.196 metric 100
192.168.1.196 dev eth0 proto dhcp scope host src 192.168.1.196 metric 100
208.67.220.220 via 192.168.1.1 dev eth0 proto dhcp src 192.168.1.196 metric 100
208.67.222.222 via 192.168.1.1 dev eth0 proto dhcp src 192.168.1.196 metric 100
I'm specifically wondering about the last two, routing the same public OpenDNS resolvers through 192.168.1.1. But they would have been routed through the default gateway anyway?
Are you perhaps redirecting DNS traffic to your Pi-hole somewhere in your network (e.g. via a dedicated firewall or your router)?