Problem:
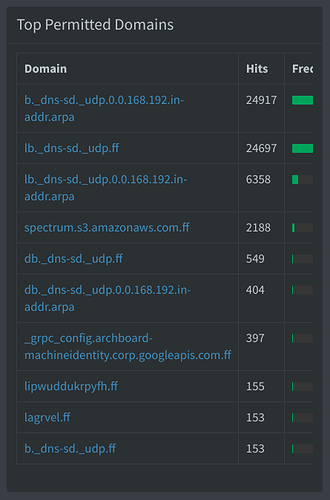
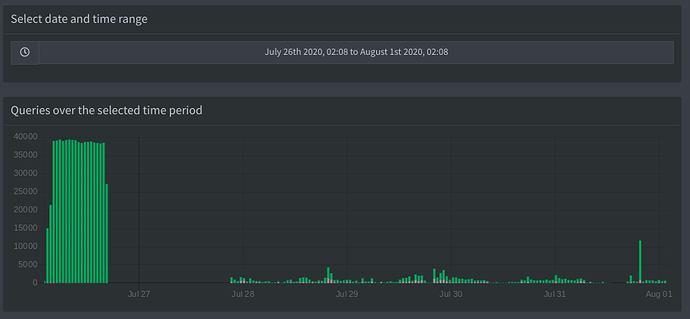
My Pi-hole has tons of random PTR queries that end in my LAN domain (.ff). This image shows the last half an hour:
I cannot figure out why something like "spectrum.s3.amazonaws.com" would be given my LAN domain --> " spectrum.s3.amazonaws.com.ff"
Current setup:
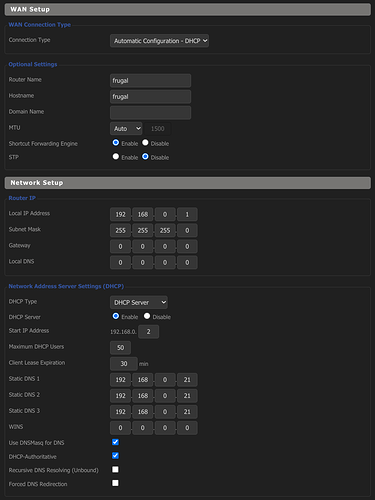
I have Pi-hole running on a Raspberry Pi 2 with the Pi-hole set to serve as my DNS provider to my Linksys WRT1900ACSv2 router running DD-WRT and serving as my DHCP server. I would like to keep it this way.
My router IP is 192.168.0.1. My Pi-hole is 192.168.0.21. I have a lot of static IPs I don't want to migrate to the Pi-hole as I add new devices frequently.
Pi-hole setup:
I have "Conditional forwarding" currently turned on but I have "Never forward non-FQDNs" and "Never forward reverse lookups for private IP ranges" turned off.
I have specified a domain of "ff" on the pihole.
DD-WRT setup:
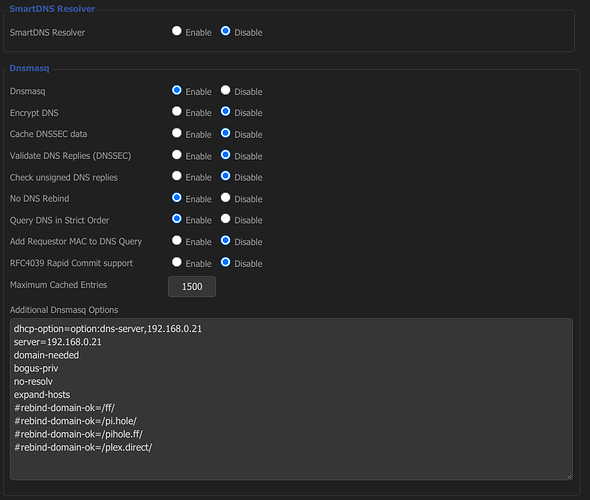
DNSMasq is turned on but is using Pi-hole as its DNS server.
Additional Dnsmasq Options: (I could use some help with these if they look wrong)
Current firewall rules (I am bypassing 192.168.0.2 as it is a second router for other purposes).
####PIHOLE####
#####Keep network on pi-hole
iptables --table nat --insert PREROUTING --in-interface br0 --protocol tcp --source ! 192.168.0.2,192.168.0.21 --destination-port 53 --jump DNAT --to-destination 192.168.0.21:53
iptables --table nat --insert PREROUTING --in-interface br0 --protocol udp --source ! 192.168.0.2,192.168.0.21 --destination-port 53 --jump DNAT --to-destination 192.168.0.21:53
#####Punch DNS hole for pi-hole
iptables --table nat --insert PREROUTING --in-interface br0 --protocol tcp --source 192.168.0.2,192.168.0.21 --destination-port 53 --jump ACCEPT
iptables --table nat --insert PREROUTING --in-interface br0 --protocol udp --source 192.168.0.2,192.168.0.21 --destination-port 53 --jump ACCEPT
Could anyone tell me how to fix this ?