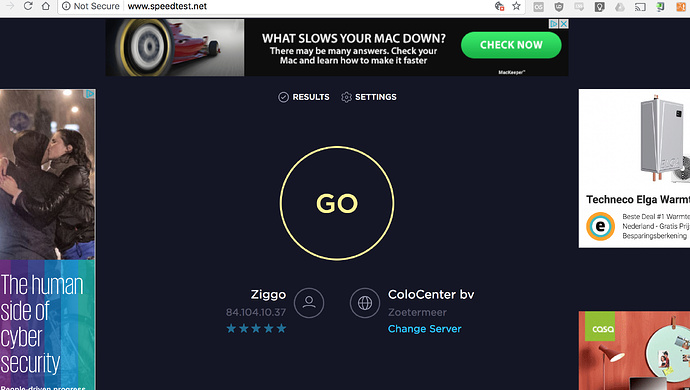
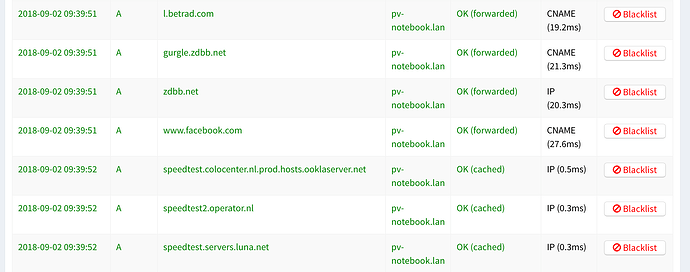
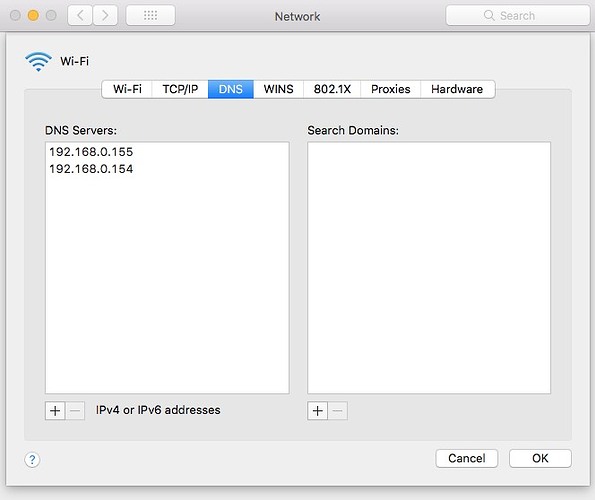
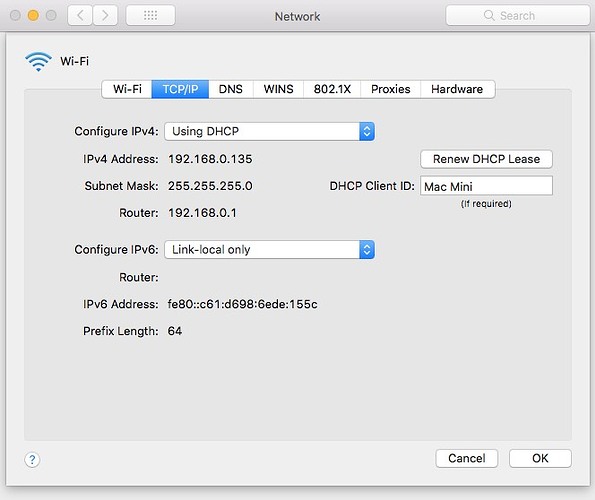
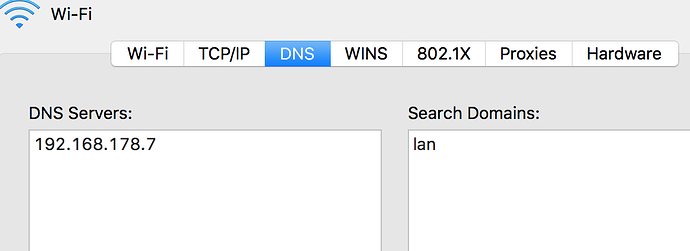
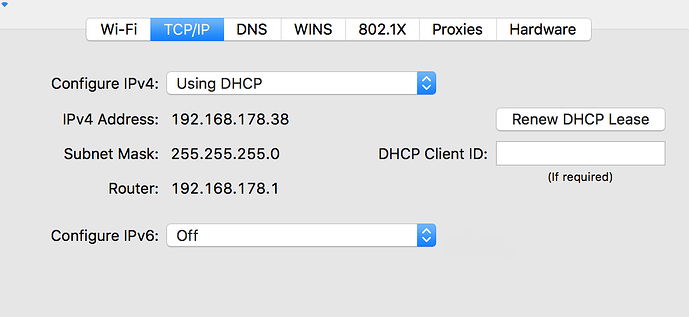
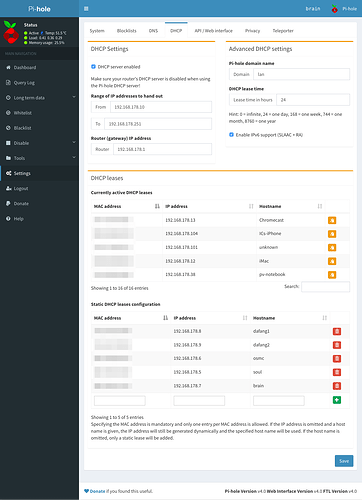
When started creating the post, I decide to investigate other machines connected and it's all different. So I've put some more information to see if it helps identifying the problem.
pv-notebook
On the mac laptop :
$ cat /etc/resolv.conf
#
# macOS Notice
#
# This file is not consulted for DNS hostname resolution, address
# resolution, or the DNS query routing mechanism used by most
# processes on this system.
#
# To view the DNS configuration used by this system, use:
# scutil --dns
#
# SEE ALSO
# dns-sd(1), scutil(8)
#
# This file is automatically generated.
#
domain lan
nameserver 192.168.178.7
brain
On the pi-hole, on 192.168.178.7
cat /etc/resolv.conf
# Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8)
# DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN
nameserver 127.0.0.1
But, on another raspi (192.168.178.5) I get different information. Is it relevant?
$ cat /etc/resolv.conf
# Generated by resolvconf
nameserver 192.168.178.1
nameserver 2001:b88:1002::10
nameserver 2001:b88:1202::10
nameserver 2001:730:3e42:1000::53
nameserver 2001:1c00:1f02:7f00:4c13:1ca3:efd2:a60c
# Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8)
# DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN
nameserver 127.0.0.1
soul
Well, here's the output of the other commands on the 192.168.178.5 (my seedbox), just in case
$ dig flurry.com
; <<>> DiG 9.10.3-P4-Raspbian <<>> flurry.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 49743
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;flurry.com. IN A
;; ANSWER SECTION:
flurry.com. 300 IN A 74.6.136.153
flurry.com. 300 IN A 98.136.103.26
flurry.com. 300 IN A 212.82.100.153
;; Query time: 42 msec
;; SERVER: 2001:b88:1002::10#53(2001:b88:1002::10)
;; WHEN: Sun Sep 02 21:52:33 CEST 2018
;; MSG SIZE rcvd: 87
And the one with the @1.1.1.1
dig flurry.com @1.1.1.1
; <<>> DiG 9.10.3-P4-Raspbian <<>> flurry.com @1.1.1.1
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48859
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1452
;; QUESTION SECTION:
;flurry.com. IN A
;; ANSWER SECTION:
flurry.com. 224 IN A 74.6.136.153
flurry.com. 224 IN A 98.136.103.26
flurry.com. 224 IN A 212.82.100.153
;; Query time: 16 msec
;; SERVER: 1.1.1.1#53(1.1.1.1)
;; WHEN: Sun Sep 02 21:54:13 CEST 2018
;; MSG SIZE rcvd: 87
osmc
Finally, on my OSMC raspi (192.168.178.6), I get yet different data
$ cat /etc/resolv.conf
# Generated by Connection Manager
nameserver 8.8.8.8
nameserver 84.116.46.20
So, here are the same commands as before (had to run sudo apt-get install dnsutils first)
$ dig flurry.com
; <<>> DiG 9.10.3-P4-Debian <<>> flurry.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48864
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;flurry.com. IN A
;; ANSWER SECTION:
flurry.com. 299 IN A 212.82.100.153
flurry.com. 299 IN A 74.6.136.153
flurry.com. 299 IN A 98.136.103.26
;; Query time: 24 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Sun Sep 02 22:13:01 CEST 2018
;; MSG SIZE rcvd: 87
And now with @1.1.1.1
$ dig flurry.com @1.1.1.1
; <<>> DiG 9.10.3-P4-Debian <<>> flurry.com @1.1.1.1
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51651
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1452
;; QUESTION SECTION:
;flurry.com. IN A
;; ANSWER SECTION:
flurry.com. 276 IN A 74.6.136.153
flurry.com. 276 IN A 98.136.103.26
flurry.com. 276 IN A 212.82.100.153
;; Query time: 15 msec
;; SERVER: 1.1.1.1#53(1.1.1.1)
;; WHEN: Sun Sep 02 22:13:34 CEST 2018
;; MSG SIZE rcvd: 87
dhcp configuration on pi-hole (soul)