Hello Community,
my new ISP gave my IPv6 Internet and I have some questions regarding Pi-Hole, IPv6 and Hostname display in Pi-Hole logs.
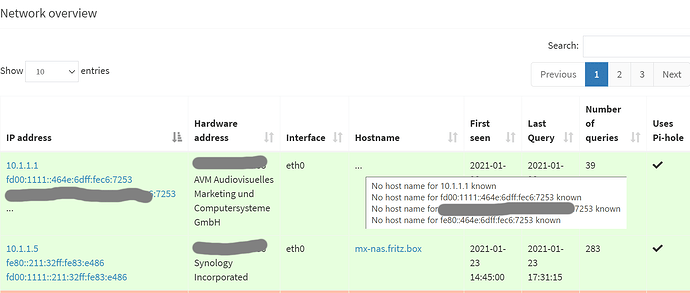
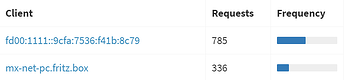
Please see Pi-Hole network info screenshot.
-
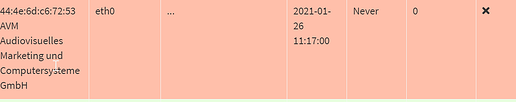
Like my router 10.1.1.1 is not getting a hostname at all. And that's the only device where I actually manually defined a hostname to use via the routers config.
-
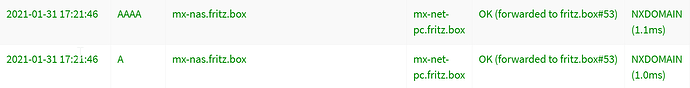
Some devices do get the IPv4 hostname displayed, but not the IPv6, like the NAS.
-
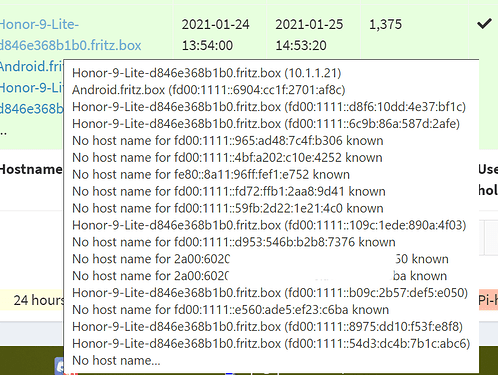
Yet other devices (not shown in screenshot) actually do get some hostname assigned to both IPv4 and IPv6.
-
This leads to 2 log entries for each device, one for IPv4 which usually also gets a hostname to show for easy client identification. And then there's the IPv6 where only the IP address is shown in the logfiles. This is making it quite hard to identify which device is sending queries, since IPv6 addresses ain't easy to memorize.
-
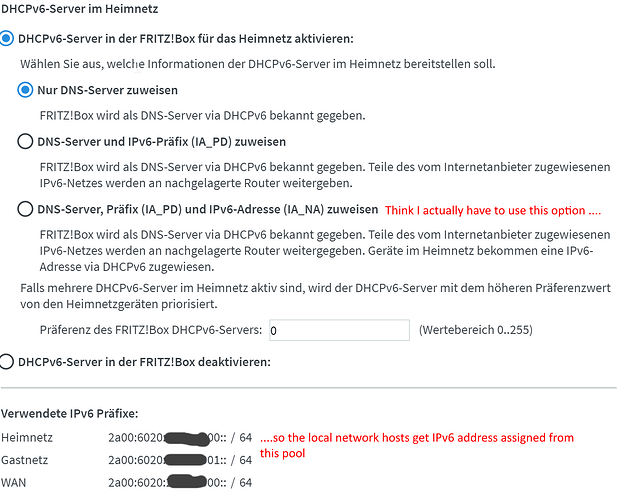
The router is acting as DHCP Server and Pi-Hole does DNS only.
The router provides Pi-Hole DNS Server IPv4 and IPv6 to its leases.
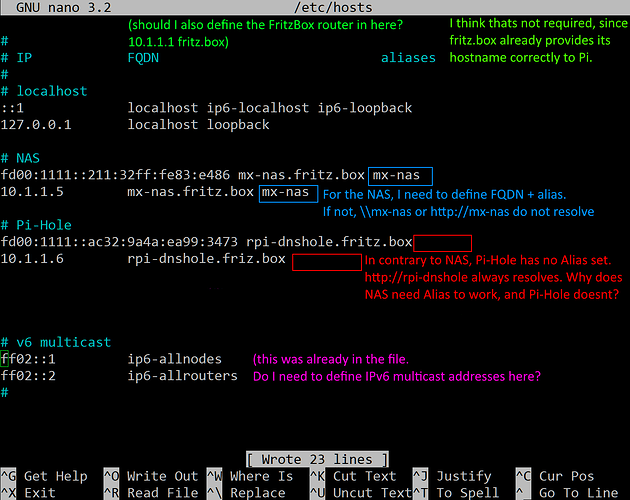
In Pi-Hole I use conditional forwarding to my router IP, so that name resolution for local devices works at all with my setup using separate DHCP server.
There is only one field for conditional forwarding in Pi-Hole config and I cannot seem to add conditional forwarding for IPv6 to the router's IPv6 address. Which would be the solution if I understood the involved networking principles correctly.
Questions:
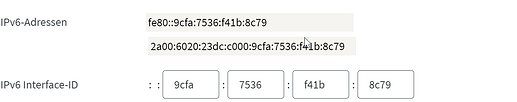
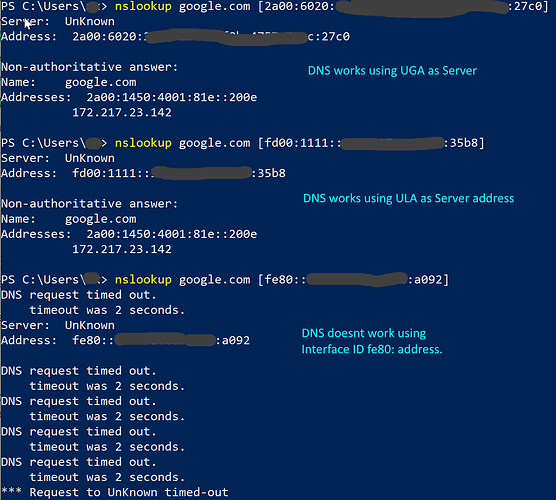
- How is determined which device gets a IPv6 hostname to show in Pi-Hole?
- How to configure so that all active IPv6 hosts get a hostname assigned to them
(so that in Pi-Hole logs a hostname is displayed as usual and not only the IPv6 address?
- Maybe there is a simple misconfiguration somewhere in my network. I really hope there is an easy way to make all IPv6 hostnames known to Pi-Hole with my current network setup.