I followed all of your instructions and I think I'm close to the root of the problem.
I did 2 tests capturing port 53 and 80, the first test has IPv6 disabled on my computer while the second has it enabled.
I'll only paste a small piece of the log as it's really big and the source/destination are the same in the entire log.
Test 1 (IPv6 disabled):
No. Time Source Destination Protocol Length Info
1 0.000000 192.168.1.8 192.168.1.236 DNS 143 Standard query response 0x14a4 No such name A wpad.lan SOA a.root-servers.net
Frame 1: 143 bytes on wire (1144 bits), 143 bytes captured (1144 bits) on interface 0
Ethernet II, Src: Raspberr_0a:ef:7c (b8:27:eb:0a:ef:7c), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 4, Src: 192.168.1.8, Dst: 192.168.1.236
User Datagram Protocol, Src Port: 53, Dst Port: 60727
Domain Name System (response)
No. Time Source Destination Protocol Length Info
2 0.000784 192.168.1.8 192.168.1.236 DNS 93 Standard query response 0xd4ae A api.protonmail.ch A 185.70.40.185
Frame 2: 93 bytes on wire (744 bits), 93 bytes captured (744 bits) on interface 0
Ethernet II, Src: Raspberr_0a:ef:7c (b8:27:eb:0a:ef:7c), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 4, Src: 192.168.1.8, Dst: 192.168.1.236
User Datagram Protocol, Src Port: 53, Dst Port: 55875
Domain Name System (response)
No. Time Source Destination Protocol Length Info
3 0.008977 192.168.1.8 192.168.1.236 DNS 89 Standard query response 0xa6eb A www.google.hr A 216.58.214.67
Frame 3: 89 bytes on wire (712 bits), 89 bytes captured (712 bits) on interface 0
Ethernet II, Src: Raspberr_0a:ef:7c (b8:27:eb:0a:ef:7c), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 4, Src: 192.168.1.8, Dst: 192.168.1.236
User Datagram Protocol, Src Port: 53, Dst Port: 62270
Domain Name System (response)
No. Time Source Destination Protocol Length Info
4 0.014546 192.168.1.8 192.168.1.236 DNS 184 Standard query response 0xa4f0 A raw.githubusercontent.com CNAME github.map.fastly.net A 151.101.0.133 A 151.101.64.133 A 151.101.128.133 A 151.101.192.133
Frame 4: 184 bytes on wire (1472 bits), 184 bytes captured (1472 bits) on interface 0
Ethernet II, Src: Raspberr_0a:ef:7c (b8:27:eb:0a:ef:7c), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 4, Src: 192.168.1.8, Dst: 192.168.1.236
User Datagram Protocol, Src Port: 53, Dst Port: 64336
Domain Name System (response)
No. Time Source Destination Protocol Length Info
15 0.188951 192.168.1.236 192.168.1.8 DNS 75 Standard query 0x0620 A ssl.gstatic.com
Frame 15: 75 bytes on wire (600 bits), 75 bytes captured (600 bits) on interface 0
Ethernet II, Src: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34), Dst: Raspberr_0a:ef:7c (b8:27:eb:0a:ef:7c)
Internet Protocol Version 4, Src: 192.168.1.236, Dst: 192.168.1.8
User Datagram Protocol, Src Port: 52189, Dst Port: 53
Domain Name System (query)
No. Time Source Destination Protocol Length Info
16 0.250948 192.168.1.8 192.168.1.236 DNS 91 Standard query response 0x0620 A ssl.gstatic.com A 172.217.21.227
Frame 16: 91 bytes on wire (728 bits), 91 bytes captured (728 bits) on interface 0
Ethernet II, Src: Raspberr_0a:ef:7c (b8:27:eb:0a:ef:7c), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 4, Src: 192.168.1.8, Dst: 192.168.1.236
User Datagram Protocol, Src Port: 53, Dst Port: 52189
Test 2 (IPv6 enabled):
No. Time Source Destination Protocol Length Info
13 0.072925 fe80::31ae:df62:fee2:90b0 fe80::1 DNS 97 Standard query 0x7591 A www.speedtest.net
Frame 13: 97 bytes on wire (776 bits), 97 bytes captured (776 bits) on interface 0
Ethernet II, Src: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34), Dst: Zte_3d:58:ff (9c:6f:52:3d:58:ff)
Internet Protocol Version 6, Src: fe80::31ae:df62:fee2:90b0, Dst: fe80::1
User Datagram Protocol, Src Port: 65230, Dst Port: 53
Domain Name System (query)
No. Time Source Destination Protocol Length Info
15 0.132411 fe80::1 fe80::31ae:df62:fee2:90b0 DNS 558 Standard query response 0x7591 A www.speedtest.net CNAME zd.map.fastly.net A 151.101.194.219 A 151.101.2.219 A 151.101.66.219 A 151.101.130.219 NS d.gtld-servers.net NS j.gtld-servers.net NS f.gtld-servers.net NS i.gtld-servers.net NS m.gtld-servers.net NS k.gtld-servers.net NS e.gtld-servers.net NS b.gtld-servers.net NS c.gtld-servers.net NS h.gtld-servers.net NS a.gtld-servers.net NS l.gtld-servers.net NS g.gtld-servers.net A 192.35.51.30 AAAA 2001:503:d414::30 A 192.42.93.30 AAAA 2001:503:eea3::30 A 192.54.112.30 AAAA 2001:502:8cc::30 A 192.33.14.30
Frame 15: 558 bytes on wire (4464 bits), 558 bytes captured (4464 bits) on interface 0
Ethernet II, Src: Zte_3d:58:ff (9c:6f:52:3d:58:ff), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 6, Src: fe80::1, Dst: fe80::31ae:df62:fee2:90b0
User Datagram Protocol, Src Port: 53, Dst Port: 65230
Domain Name System (response)
No. Time Source Destination Protocol Length Info
37 0.567905 fe80::31ae:df62:fee2:90b0 fe80::1 DNS 102 Standard query 0xc1d6 A zdstatic.speedtest.net
Frame 37: 102 bytes on wire (816 bits), 102 bytes captured (816 bits) on interface 0
Ethernet II, Src: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34), Dst: Zte_3d:58:ff (9c:6f:52:3d:58:ff)
Internet Protocol Version 6, Src: fe80::31ae:df62:fee2:90b0, Dst: fe80::1
User Datagram Protocol, Src Port: 54869, Dst Port: 53
Domain Name System (query)
No. Time Source Destination Protocol Length Info
40 0.572238 fe80::31ae:df62:fee2:90b0 fe80::1 DNS 91 Standard query 0xdb84 A b.cdnst.net
Frame 40: 91 bytes on wire (728 bits), 91 bytes captured (728 bits) on interface 0
Ethernet II, Src: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34), Dst: Zte_3d:58:ff (9c:6f:52:3d:58:ff)
Internet Protocol Version 6, Src: fe80::31ae:df62:fee2:90b0, Dst: fe80::1
User Datagram Protocol, Src Port: 56785, Dst Port: 53
Domain Name System (query)
No. Time Source Destination Protocol Length Info
53 0.629636 fe80::1 fe80::31ae:df62:fee2:90b0 DNS 552 Standard query response 0xdb84 A b.cdnst.net CNAME zd.map.fastly.net A 151.101.2.219 A 151.101.66.219 A 151.101.130.219 A 151.101.194.219 NS f.gtld-servers.net NS c.gtld-servers.net NS l.gtld-servers.net NS e.gtld-servers.net NS i.gtld-servers.net NS j.gtld-servers.net NS g.gtld-servers.net NS a.gtld-servers.net NS h.gtld-servers.net NS b.gtld-servers.net NS k.gtld-servers.net NS d.gtld-servers.net NS m.gtld-servers.net A 192.35.51.30 AAAA 2001:503:d414::30 A 192.42.93.30 AAAA 2001:503:eea3::30 A 192.54.112.30 AAAA 2001:502:8cc::30 A 192.33.14.30
Frame 53: 552 bytes on wire (4416 bits), 552 bytes captured (4416 bits) on interface 0
Ethernet II, Src: Zte_3d:58:ff (9c:6f:52:3d:58:ff), Dst: Giga-Byt_10:ad:34 (74:d4:35:10:ad:34)
Internet Protocol Version 6, Src: fe80::1, Dst: fe80::31ae:df62:fee2:90b0
User Datagram Protocol, Src Port: 53, Dst Port: 56785
Domain Name System (response)
If I disable IPv6, all of the DNS queries go to my pi-hole and back to me, and the ads are blocked.
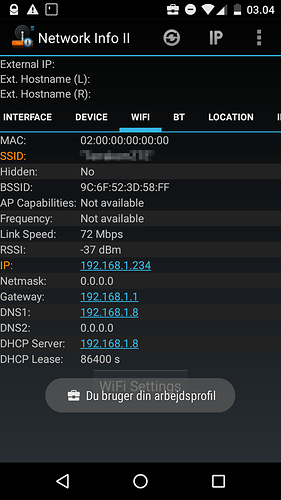
But if I enable IPv6, it looks like all my DNS queries go to my router (I don't know how IPv6 works, I'm guessing fe80::1 is the router.) instead of the Pi.
I've been browsing for a little bit with IPv6 disabled on my Windows machine and it looks like everything works as it should now, but what about the other devices?