I've been using PiHole for years. I've recently installed PiHole on a new Raspberry Pi 4 server, using docker compose. I'm seeing advertising in Chrome on my work Windows 11 computer, which I didn't see with the old server. I've temporarily disabled IPv6 during diagnostics to check that's not the problem.
The behavior I'm seeing makes it look like some queries are going to PiHole, some are going to another DNS server. I've done my best to configure Chrome / Firefox to use the OS DNS, disabling secure DNS, as far as I can see everything should be using PiHole. I've checked the OS and it seems to be using PiHole - details below.
My network is using PiHole DHCP, so the machines get the PiHole DNS IP automatically.
I'd appreciate any help to work through this. I've spent many hours over the past couple of weeks trying to diagnose the problem myself, and haven't solved it yet.
Expected Behaviour:
I expect advertising images served from domains on my block lists to be blocked in my web browser. I also expect the DNS lookup to be shown in the PiHole logs.
Additionally, when I issue an nslookup for a domain on one of my block lists I expect to receive 0.0.0.0
Actual Behaviour:
As an example, when I open stuff.co.nz in the web browser using Chrome I can see advertising. An image from this URL is being displayed at the moment.
https://s0.2mdn.net/simgad/14473468899493315525?sqp=uqWu0g0ICNgEEKABQGQ&rs=AOga4qnsGl144LpdWIYxzFitZy2LkorISw
Searching the PiHole blocklist I can see that domain is on the block list.
Exact match for **s0.2mdn.net** found in: - https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
I can't see the DNS query for stuff.co.nz in pi hole logs. I have "use secure DNS" turned off in Chrome, and disabled the built in Chrome DNS server.
Chrome Not Using PiHole?
I wondered if the stuff.co.nz DNS was cached. To check that I tried visiting a random domain that I've probably never been to before - I randomly tried happybirds.com. I can't see any reference to that domain in the GUI query logs or the PiHole log.
> /var/log/pihole# grep happybirds *
(no results)
I can see that the computer I'm using is sending some queries to PiHole (PC is 192.168.1.38). PiHole is 192.168.1.12.
pihole.log:Sep 15 13:51:05 dnsmasq[13534]: query[TXT] debug.opendns.com from 192.168.1.38
pihole.log:Sep 15 13:51:40 dnsmasq[13534]: query[TXT] debug.opendns.com from 192.168.1.38
pihole.log:Sep 15 13:52:03 dnsmasq[13534]: query[A] wpad.home.arpa from 192.168.1.38
pihole.log:Sep 15 13:52:15 dnsmasq[13534]: query[TXT] debug.opendns.com from 192.168.1.38
pihole.log:Sep 15 13:52:32 dnsmasq[13534]: query[A] metadata.google.internal from 192.168.1.38
When I open up a dozen tabs and open a bunch of websites, including some I don't use regularly, I see practically nothing in the PiHole log from this computer / IP.
Checking DNS
The first thing I checked was that PiHole is being used as the DNS server (parts removed for brevity)
>ipconfig /all
Ethernet adapter Ethernet 2:
Connection-specific DNS Suffix . : home.arpa
Description . . . . . . . . . . . : Realtek USB GbE Family Controller #2
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 192.168.1.38(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Friday, 15 September 2023 9:49:47 am
Lease Expires . . . . . . . . . . : Friday, 15 September 2023 3:34:56 pm
Default Gateway . . . . . . . . . : 192.168.1.1
DHCP Server . . . . . . . . . . . : 192.168.1.12
DNS Servers . . . . . . . . . . . : 192.168.1.12
NetBIOS over Tcpip. . . . . . . . : Enabled
> netsh int ipv4 show dnsservers
Configuration for interface "Ethernet 2"
DNS servers configured through DHCP: 192.168.1.12
Register with which suffix: Primary only
It looks to me like DNS is set up to point to 192.168.1.12 / PiHole.
Next I opened MS Edge and checked that Secure DNS is enabled. I then opened about ten different websites with random names in tabs - this.com, that.com, fred.com, george.com, etc. Of those ten websites I saw two DNS queries hit PiHole. I am seeing a lot of queries for debug.opendns.com coming from this machine, I assume it's one of the many services running in the background.
Sep 15 13:57:52 dnsmasq[14170]: query[A] www.newshub.co.nz from 192.168.1.38
Sep 15 13:58:06 dnsmasq[13534]: query[TXT] debug.opendns.com from 192.168.1.38
Sep 15 13:58:16 dnsmasq[13534]: query[TXT] debug.opendns.com from 192.168.1.38
Sep 15 13:58:41 dnsmasq[13534]: query[TXT] debug.opendns.com from 192.168.1.38
Sep 15 13:58:41 dnsmasq[13534]: query[AAAA] api-ipv4.opendns.com from 192.168.1.38
Sep 15 13:58:47 dnsmasq[13534]: query[A] bob.com from 192.168.1.38
That shows that at least some traffic is going to PiHole.
nslookup testing
I did some testing with nslookup. When I issue an nslookup for a domain without a trailing dot (noting nslookup unwanted behaviour) I can see the query for the domain with the local connection specific suffix (see ipconfig above) in my pihole logs, which returns nothing. nslookup then queries the primary domain without a suffix but I can't see that in PiHole logs. Again, it looks like another DNS server is being used for some portion of the queries, or PiHole isn't logging some queries.
(nslookup output summarized for brevity, AAAA queries removed as they're essentially a duplicate of the A query)
> nslookup
Default Server: pi.hole
Address: 192.168.1.12
> set debug
> uy054eprsdoz.appspot.com
uy054eprsdoz.appspot.com.home.arpa, type = A, class = IN (no answers)
uy054eprsdoz.appspot.com, type = A, class = IN
ANSWERS:
-> uy054eprsdoz.appspot.com
internet address = 146.112.61.107
ttl = 0 (0 secs)
Here's the pihole log. I can see the query for uy054eprsdoz.appspot.com.home.arpa but there's no query for the base domain uy054eprsdoz.appspot.com
pihole.log:Sep 15 08:06:03 dnsmasq[316]: query[A] uy054eprsdoz.appspot.com.home.arpa from 192.168.1.38
pihole.log:Sep 15 08:06:03 dnsmasq[316]: config uy054eprsdoz.appspot.com.home.arpa is NXDOMAIN
pihole.log:Sep 15 08:06:03 dnsmasq[316]: query[AAAA] uy054eprsdoz.appspot.com.home.arpa from 192.168.1.38
pihole.log:Sep 15 08:06:03 dnsmasq[316]: config uy054eprsdoz.appspot.com.home.arpa is NXDOMAIN
Confirming that domain is in my block list
Exact match for **uy054eprsdoz.appspot.com** found in: - https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
When I issue an nslookup for another domain on my blacklist including a trailing dot it sometimes seems to work as expected.
> nslookup
Default Server: pi.hole
Address: 192.168.1.12
> set debug
> armantark.com
Sep 15 08:14:08 dnsmasq[316]: query[A] armantark.com from 192.168.1.38
Sep 15 08:14:08 dnsmasq[316]: gravity blocked armantark.com is 0.0.0.0
Sep 15 08:14:09 dnsmasq[316]: query[AAAA] armantark.com from 192.168.1.38
Sep 15 08:14:09 dnsmasq[316]: gravity blocked armantark.com is ::
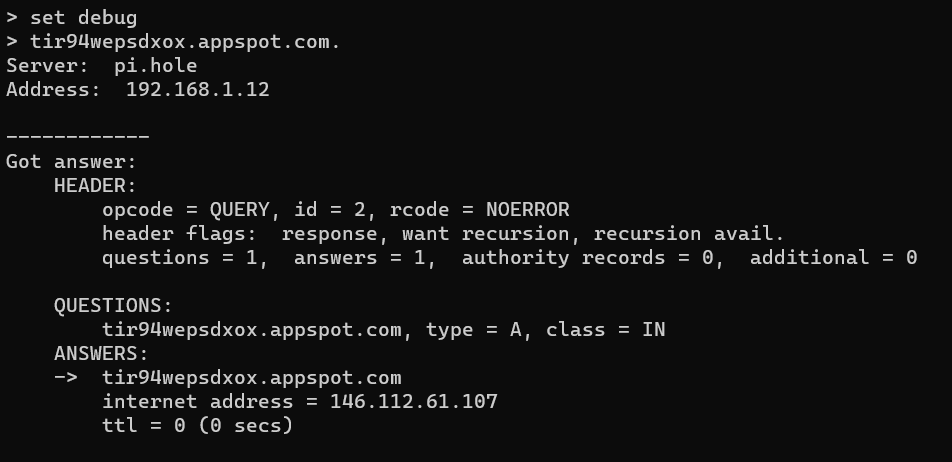
> tir94wepsdxox.appspot.com
QUESTIONS:
tir94wepsdxox.appspot.com, type = A, class = IN
ANSWERS:
-> tir94wepsdxox.appspot.com
internet address = 146.112.61.107
tir94wepsdxox doesn't show in the PiHole logs at all.
Another PC
What's even more confusing is my personal PC works fine - it uses PiHole consistently and ads are blocked. When I turn it on for the day and visit stuff.co.nz I get a ton of entries in the PiHole logs. This makes me think the problem may be with my work Windows 11 laptop rather than PiHole or my network.
pihole.log:Sep 15 15:27:52 dnsmasq[624]: query[AAAA] www.stuff.co.nz from fd00::xxxx
pihole.log:Sep 15 15:27:52 dnsmasq[625]: query[A] www.stuff.co.nz from fd00::xxxx
pihole.log:Sep 15 15:27:52 dnsmasq[626]: query[HTTPS] www.stuff.co.nz from fd00::xxxx
pihole.log:Sep 15 15:27:53 dnsmasq[633]: query[AAAA] www.stuff.co.nz from fd00::xxxx
pihole.log:Sep 15 15:27:53 dnsmasq[634]: query[A] www.stuff.co.nz from 192.168.1.9
pihole.log:Sep 15 15:27:53 dnsmasq[635]: query[HTTPS] www.stuff.co.nz from 192.168.1.9
pihole.log:Sep 15 15:27:54 dnsmasq[645]: query[AAAA] www.stuff.co.nz from 192.168.1.9
pihole.log:Sep 15 15:27:54 dnsmasq[646]: query[A] www.stuff.co.nz from 2406:e001:a:a200:xxxx
pihole.log:Sep 15 15:27:54 dnsmasq[647]: query[HTTPS] www.stuff.co.nz from 2406:e001:a:a200:xxxx
(etc)
The main difference is I have IPv6 enabled on my home PC.
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . : home.arpa
Description . . . . . . . . . . . : Realtek Gaming 2.5GbE Family Controller
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : 2406:(removed)
IPv6 Address. . . . . . . . . . . : fd00::(removed)
Temporary IPv6 Address. . . . . . : 2406:(removed)
Temporary IPv6 Address. . . . . . : fd00::(removed)
Link-local IPv6 Address . . . . . : fe80::(removed)
IPv4 Address. . . . . . . . . . . : 192.168.1.9(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Friday, 15 September 2023 3:26:00 pm
Lease Expires . . . . . . . . . . : Friday, 15 September 2023 5:26:00 pm
Default Gateway . . . . . . . . . : fe80::2e3a:fdff:fed6:429c%5 (router)
fe80::5a3d:7449:3b6b:d1c7%5 (router)
192.168.1.1 (router)
DHCP Server . . . . . . . . . . . : 192.168.1.12 (PiHole)
DHCPv6 IAID . . . . . . . . . . . : 1022xxxxx
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-27-4F-(removed)
DNS Servers . . . . . . . . . . . : 192.168.1.12 (PiHole IPv4)
2406:e001:a:a200:48aa:f9ad:19de:2ee9 (PiHole IPv6)
fd00::6548:c3fd:7bb:98c5 (PiHole IPv6)
NetBIOS over Tcpip. . . . . . . . : Enabled
Summary
All in all I'm seeing really odd, inconsistent behavior in web browsers and nslookup on my work PC, which my home PC works fine. Even in nslookup which is saying it's using pihole I'm not seeing log entries for all queries, and blocking is sporadic.
Any suggestions how to look further into this would be appreciated.
Debug Token:
https://tricorder.pi-hole.net/FfrA7o2X/