Hi All,
First of all thanks for the reply.
DanSchaper : right I'm Italian and English is not my mother language , for IP I mean the node name of LAN device.
Test done with pi-hole offline:
Esecuzione di Ping tristano.fritz.box [192.168.2.61] con 32 byte di dati:
Risposta da 192.168.2.61: byte=32 durata<1ms TTL=64
.......
C:>nslookup tristano
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: fd78:1958:81bd:5f8c:xxxxxxxxxxxxxxxxxxxxxxxxx
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Tempo scaduto per la richiesta a UnKnown
Ping to PI-HOLE server
C:>ping pedragon
Esecuzione di Ping pedragon.fritz.box [192.168.2.8] con 32 byte di dati:
Risposta da 192.168.2.6: Host di destinazione non raggiungibile.
Statistiche Ping per 192.168.2.8:
Pacchetti: Trasmessi = 4, Ricevuti = 4,
Persi = 0 (0% persi),
Than I started the pi-hole server
C:\Windows\System32>ping tristano
Esecuzione di Ping tristano.fritz.box [192.168.2.61] con 32 byte di dati:
Risposta da 192.168.2.61: byte=32 durata<1ms TTL=64
After few minutes
C:>ping tristano
Esecuzione di Ping tristano.fritz.box [45.76.93.104] con 32 byte di dati:
Risposta da 45.76.93.104: byte=32 durata=16ms TTL=55
Richiesta scaduta.
Risposta da 45.76.93.104: byte=32 durata=106ms TTL=55
Risposta da 45.76.93.104: byte=32 durata=113ms TTL=55
C:>nslookup tristano
Server: pi.hole
Address: fd78:1958:81bd:5f8c:8aae:----------
Risposta da un server non autorevole:
Nome: tristano.fritz.box
Addresses: 2001:19f0:6c00:1b0e:5400:------------
45.76.93.104
Problem seems to be on IP6 class
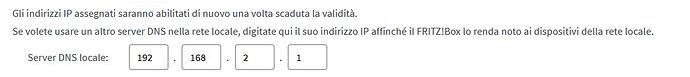
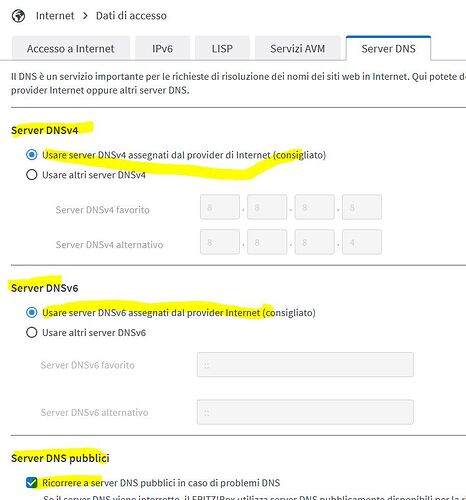
Currently router configuration on DNS session
IP6 DNS Disabled
Internet DNS server
Before the problem IP6 DNS was active , and all IP configurations were pointed to PI-hole server
Pi-hole DNS setting (previously IP6 was checked)
Bucking_Horn:
If I'm accessing to site hosted on vultr.com cloud infrastructure is not consciously
I'm not able to find the IP that is accessing to the site
_______@pedragon:~$ pihole-FTL sqlite3 /etc/pihole/pihole-FTL.db "select domain, client, count(domain) from queries where domain like '%ultr%' group by domain;"
ultrapunchneedle.com|192.168.2.24|5
www.cineultra.eu|192.168.2.14|5
CallMeCurious:
Dig command
______@pedragon:~$ sudo dig +trace vultrusercontent.com
[sudo] password for :
; <<>> DiG 9.16.48-Ubuntu <<>> +trace vultrusercontent.com
;; global options: +cmd
fritz.box. 9 IN SOA fritz.box. admin.fritz.box. 1711048060 21600 1800 43200 10
;; Received 68 bytes from 192.168.2.1#53(192.168.2.1) in 0 ms
For my low knowledge on networks matter still remain a mystery what is happening.
Tomorrow I'll try to setup the same DMS server of PI-hole on Fritz router to see what happens.
Edit : I forget to put the reason because I'm thinking on vultrusercontent.com
C:>tracert tristano
Traccia instradamento verso tristano.fritz.box [45.76.93.104]
su un massimo di 30 punti di passaggio:
1 <1 ms <1 ms <1 ms fritz.box [192.168.2.1]
2 3 ms 2 ms 2 ms 10g-gemelli.pretorio.uni.net [194.183.16.97]
3 3 ms 2 ms 2 ms 81.29.182.237
4 11 ms 11 ms 11 ms as57463.226.180.netix.net [185.1.226.180]
5 11 ms 12 ms 12 ms decix.fkt.vultr.com [80.81.196.21]
6 15 ms 12 ms 11 ms 10.75.2.42
7 11 ms 11 ms 11 ms 10.75.2.6
8 * * * Richiesta scaduta.
9 21 ms 11 ms 11 ms 45.76.93.104.vultrusercontent.com [45.76.93.104]
Traccia completata.
Thanks
Ciao
Luca