To be sincere idk, I mean, I did check the log but I couldn't find anything other than the usual requests, some requests with empty response, some fail, but I just couldn't figure things out.
I should have paid more attention with Pi-Hole telling me who could be behind all of that tho instead of waiting for the second time to happen.
Those graphics are from my OPNSense router which is also running Ntopng and Zenarmor (IDS/IDP).
I have a firewall rule to force everybody requesting DNS to be redirected to Pi-Hole and only Pi-Hole can go out, also, block any device with hard-coded DNS, DNS-over-TLS and DNS-over-HTTPS to bypass Pi-Hole, drop everything.
That is why the client is shown as Pi-Hole on Ntopng.
You will understand this bit in a second.
I have this Pi-Hole + Unbound Recursive + Firewall setup running for years, it is beautiful how everything just works with crazy fast internet even via WireGuard VPN sending all traffic via it (0.0.0.0/0)
I have primary and secondary so one can go down and the other will assume, not in this case of course. So I was not ready to deal with this problem twice haha
Since I knew my laptop was the one causing this thanks to Pi-Hole ( 192.168.1.20 )
I started looking around, checking my laptop network activities and I have been trying Brave browser over Firefox for a month now, well, it turns out that Brave like Chrome has a built-in mDNS which under the right circumstances could be the one flooding Pi-Hole with DNS requests.
Because of that firewall rule sending everything to Pi-Hole, it just "f that" haha like I would have done.
To have the internet back online, I had to actually reboot the OPNSense router and the ONT
I have since created a firewall rule to block my laptop from accessing mDNS altogether ( 224.0.0.251:5353 ). Firewall is doing its thing blocking everything so I hope that will solve the problem.
But again, this is guess atm, I am still monitoring my laptop which is running Linux so this isn't Windows doing Windows things.
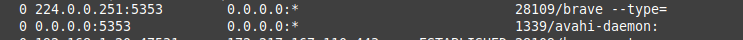
Network isn't my strongest so I wonder if there is anything really Pi-Hole could have pointed out like an isolated historic of the device causing the problem so I could investigate other than the usual clients requests, idk.
To be clear, I am not pointing fingers at Pi-Hole + Unbound Recursive DNS, cannot live without it anymore, it is just a humble question while I am trying to find ways to better monitor my home network.
Token: https://tricorder.pi-hole.net/8zFseCjI/
Thank you for the help Bucking.







