As for dnssec don't turn it on in stubby.yml it won't work as stated above. You will have to make sure your upstream which can be set in the stubby.yml is doing it.
Ah ok, im not sure if I enabled it to be honest.
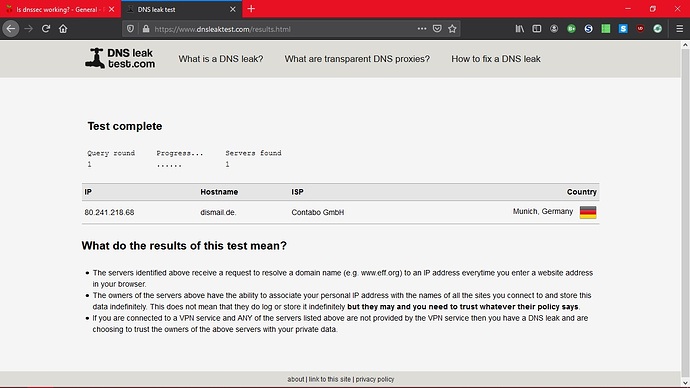
DNS leak test returns surfnet in the Netherlands
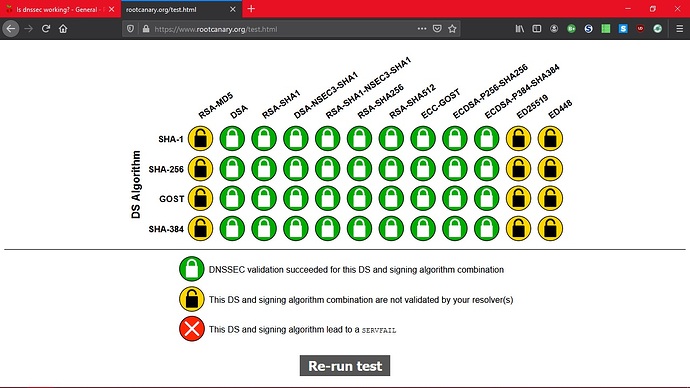
It's working!
I can walk you through picking a server later tonight if you need help with that stubby.yml
Seems to be almost there!
Thanks so much for your time and help!
Just cannot get dnssec to work.
Changed to cloudflared and still failing tests
Thanks man.
But it's getting late here in the UK and I need to sleep
Try that dismail.de it does dnssec you have to input the information from the website manually. It's not in the stubby.yml
Np I'm glad it's almost there!
I'll give them a try tomorrow and report back!
It's pretty impressive honestly. The ONE guy that runs it (plus a bunch of other privacy oriented services including email all for free too) does it so well.
@drewski would you mind sharing your stubby.yaml file please?
For some reason i cannot get dismail.de to resolve.
If i set it in my stubby.yaml nothing is resolved.
If i switch to any other upstream it works OK...
some examples with all the commented lines removed:
Not working
resolution_type: GETDNS_RESOLUTION_STUB
dns_transport_list:
- GETDNS_TRANSPORT_TLS
tls_authentication: GETDNS_AUTHENTICATION_REQUIRED
tls_query_padding_blocksize: 128
edns_client_subnet_private : 1
round_robin_upstreams: 0
idle_timeout: 7500
tls_connection_retries: 3
tls_backoff_time: 300
timeout: 2500
listen_addresses:
- 127.0.0.1@5454
- 0::1
upstream_recursive_servers:
- address_data: 80.241.281.68
tls_auth_name: "fdns1.dismail.de"
tls_pubkey_pinset:
- digest: "sha256"
value: MMi3E2HZr5A5GL+badqe3tzEPCB00+OmApZqJakbqUU=
Working
resolution_type: GETDNS_RESOLUTION_STUB
dns_transport_list:
- GETDNS_TRANSPORT_TLS
tls_authentication: GETDNS_AUTHENTICATION_REQUIRED
tls_query_padding_blocksize: 128
edns_client_subnet_private : 1
round_robin_upstreams: 0
idle_timeout: 7500
tls_connection_retries: 3
tls_backoff_time: 300
timeout: 2500
listen_addresses:
- 127.0.0.1@5454
- 0::1
upstream_recursive_servers:
- address_data: 1.1.1.1
tls_auth_name: "cloudflare-dns.com"
- address_data: 1.0.0.1
tls_auth_name: "cloudflare-dns.com"
Can i ask why you say this?
Having a quick play with the stubby.yaml file, if i enable dnssec it seems to work OK, when using cloudflare for example?
....
dnssec: GETDNS_EXTENSION_TRUE
dnssec_trust_anchors: "/var/lib/unbound/root.key"
...
Finally, just kind of thinking out loud....
Is there any reason to / benefit to running stubby behind unbound? I seem to rememeber reading it somewhere, but cant find where.
So pihole set to use unbound, which has stubby set as the forward-addr
e.g. Unbound running on 127.0.0.1@5353 and stubby running on 127.0.0.2@5454.
Pihole upstream set to 127.0.0.1#5353 and inside unbound config: forward-addr: 127.0.0.2@5454
This is what i have for upstream. I have two resolvers selected in my .yml for redundancy.
#Dismail.de
- address_data: 80.241.218.68
tls_auth_name: "fdns1.dismail.de"
tls_pubkey_pinset:
- digest: "sha256"
value: MMi3E2HZr5A5GL+badqe3tzEPCB00+OmApZqJakbqUU=
## Surfnet/Sinodun servers
- address_data: 145.100.185.15
tls_port: 443
tls_auth_name: "dnsovertls.sinodun.com"
tls_pubkey_pinset:
- digest: "sha256"
value: 62lKu9HsDVbyiPenApnc4sfmSYTHOVfFgL3pyB+cBL4=
#Dismail.de ipv6
- address_data: 2a02:c205:3001:4558::1
tls_auth_name: "fdns1.dismail.de"
tls_pubkey_pinset:
- digest: "sha256"
value: MMi3E2HZr5A5GL+badqe3tzEPCB00+OmApZqJakbqUU=
So your .yml matches mine...what could be causing mine to not resolve?
I'm not to sure other than try to literally copy+paste my lines. As for dnssec if it is working in stubby thats awesome yay for that. I think the advantage with unbound+stubby may lie with caching.
Ill try a direct copy and paste thanks.
But the caching is handled by Pi-hole FTLDNS is it not?
So in terms of privacy theres no gain to using unbound + stubby?
No privacy gain. It could be dnssec breaking dismail.de that particular resolver is already doing dnssec so you doing it also could break it
Ive actually just disabled dnssec and still not able to resolve, even with a copy and paste (and checking whitespace) of your code
Well that is strange. I'm lost on that one sorry
No problem.
I'll create a new stubby yaml file later when im home and try again.
Going back to using unbound + stubby...worth trying fo you think?
(Baring in mind what my ISP is doing, and i could not use unbound in recursive mode