Please follow the below template, it will help us to help you!
*If you are Experiencing issues with a Pi-hole install that has non-standard elements
Device is operational.
Reaching out for guidance and best methods to attempt to verify and confirm status if unbound on Pihole v6 is operational
Expected Behaviour:
UNBOUND STATUS on Pihole Version 6
$ sudo systemctl status unbound
● unbound.service - Unbound DNS server
Loaded: loaded (/lib/systemd/system/unbound.service; enabled; preset: enabled)
Active: active (running) since Sat 2025-02-22 20:11:31 EST; 42min ago
Docs: man:unbound(8)
Process: 2651 ExecStartPre=/usr/libexec/unbound-helper chroot_setup (code=exited, status=0/SUCCESS)
Process: 2653 ExecStartPre=/usr/libexec/unbound-helper root_trust_anchor_update (code=exited, status=0/SUCCESS)
Main PID: 2655 (unbound)
Tasks: 1 (limit: 767)
CPU: 357ms
CGroup: /system.slice/unbound.service
└─2655 /usr/sbin/unbound -d -p
Feb 22 20:11:31 pihole1 systemd[1]: Starting unbound.service - Unbound DNS server...
Feb 22 20:11:31 pihole1 unbound[2655]: [2655:0] warning: subnetcache: prefetch is set but not working for data originating from the subnet module cache.
Feb 22 20:11:31 pihole1 unbound[2655]: [2655:0] info: start of service (unbound 1.17.1).
Feb 22 20:11:31 pihole1 systemd[1]: Started unbound.service - Unbound DNS server.
UNBOUND VERSION
unbound -v
[1740275503] unbound[2919:0] notice: Start of unbound 1.17.1.
[1740275503] unbound[2919:0] error: can't bind socket: Address already in use for 127.0.0.1 port 5335
[1740275503] unbound[2919:0] fatal error: could not open ports
UNBOUND TESTS
TEST01
dig www.cnn.com @127.0.0.1 -p 5335
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> www.cnn.com @127.0.0.1 -p 5335
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 61431
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;www.cnn.com. IN A
;; ANSWER SECTION:
www.cnn.com. 300 IN CNAME cnn-tls.map.fastly.net.
cnn-tls.map.fastly.net. 60 IN A 151.101.127.5
;; Query time: 131 msec
;; SERVER: 127.0.0.1#5335(127.0.0.1) (UDP)
;; WHEN: Sat Feb 22 20:47:59 EST 2025
;; MSG SIZE rcvd: 92
TEST 02
dig sigok.verteiltesysteme.net @127.0.0.1 -p 5335
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> sigok.verteiltesysteme.net @127.0.0.1 -p 5335
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58893
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;sigok.verteiltesysteme.net. IN A
;; ANSWER SECTION:
sigok.verteiltesysteme.net. 1799 IN CNAME sigok.rsa2048-sha256.ippacket.stream.
sigok.rsa2048-sha256.ippacket.stream. 60 IN A 195.201.14.36
;; Query time: 539 msec
;; SERVER: 127.0.0.1#5335(127.0.0.1) (UDP)
;; WHEN: Sat Feb 22 20:51:09 EST 2025
;; MSG SIZE rcvd: 121
TEST 03
dig sigfail.verteiltesysteme.net @127.0.0.1 -p 5335
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> sigfail.verteiltesysteme.net @127.0.0.1 -p 5335
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 22
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;sigfail.verteiltesysteme.net. IN A
;; Query time: 2659 msec
;; SERVER: 127.0.0.1#5335(127.0.0.1) (UDP)
;; WHEN: Sat Feb 22 20:47:30 EST 2025
;; MSG SIZE rcvd: 57
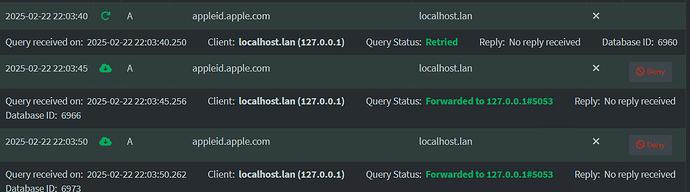
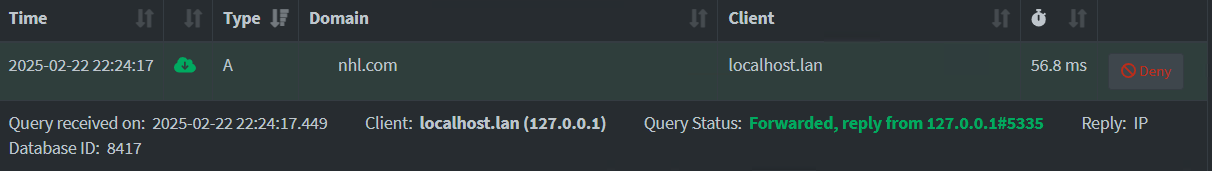
Actual Behaviour:
I am attempting to make sense or learn the best method to verify and confirm unbound is deployed and operational on Pihole v6
As unbound was previously operational on my Pihole v5 environment, due to the requirement to update to the current OS recommendation, it was required to rebuild out some feature sets.
I attempted to locate some direct information to wrap my head around testing, and wanted to post, seeking some some recommendations from the community to assist with this unbound deployment, so I can be assured everything is working as required.
I look forward to hearing back from the many experts in this community with some tips and guidance.
Thank you kindly.