Question and setup
How do I verify that DoH is actually being used?
I have stepped through the pihole install guide and set up cloudflared using the docs, and have enabled the custom 127.0.0.1#5053 DNS specified in the guide, but I'm not sure that it is set up to use DoH properly. I want to make sure things are configured to use DoH before forcing all devices on the network to use the pihole, so as of now only my Linux laptop is using the pihole as a DNS server by editing /etc/resolv.conf.
Equipment
I am running pihole on a Raspberry Pi 4 (Debian Bookworm)
sudo pihole -v
Core version is v6.0.3 (Latest: v6.0.3)
Web version is v6.0.1 (Latest: v6.0.1)
FTL version is v6.0.1 (Latest: v6.0.1)
Expected Behaviour:
On the pihole:
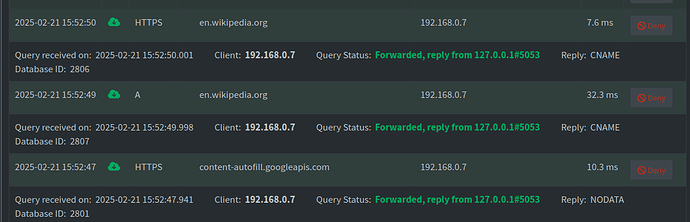
I expect dig example.com @127.0.0.1 would show SERVER: 127.0.0.1#5053, meaning the DNS is encrypted.
On my local laptop that is using the pihole for DNS, I expect dig example.com @<my_pihole_IP> would show SERVER: 127.0.0.1#5053, meaning the DNS is encrypted.
Actual Behaviour:
When I run dig on the pihole server or my laptop client, I see port 53 listed. Doesn't showing port 53 mean that DNS is not encrypted?
digging from the pihole:
user4@pihole:~ $ dig example.com @127.0.0.1
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> example.com @127.0.0.1
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 61912
;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; EDE: 3 (Stale Answer)
;; QUESTION SECTION:
;example.com. IN A
;; ANSWER SECTION:
example.com. 0 IN A 23.215.0.138
example.com. 0 IN A 23.192.228.84
example.com. 0 IN A 23.215.0.136
example.com. 0 IN A 23.192.228.80
example.com. 0 IN A 96.7.128.198
example.com. 0 IN A 96.7.128.175
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1) (UDP)
;; WHEN: Fri Feb 21 20:56:53 GMT 2025
;; MSG SIZE rcvd: 142
Digging from pihole but specifying port 5053:
user4@pihole:~ $ dig example.com @127.0.0.1 -p 5053
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> example.com @127.0.0.1 -p 5053
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 1327
;; flags: qr aa rd ra ad; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 42d7b4ca352c7397 (echoed)
;; QUESTION SECTION:
;example.com. IN A
;; ANSWER SECTION:
examPLE.CoM. 102 IN A 96.7.128.175
examPLE.CoM. 102 IN A 23.215.0.136
examPLE.CoM. 102 IN A 23.192.228.84
examPLE.CoM. 102 IN A 23.192.228.80
examPLE.CoM. 102 IN A 96.7.128.198
examPLE.CoM. 102 IN A 23.215.0.138
;; Query time: 0 msec
;; SERVER: 127.0.0.1#5053(127.0.0.1) (UDP)
;; WHEN: Fri Feb 21 20:56:59 GMT 2025
;; MSG SIZE rcvd: 214
Also, does anyone know why the answers above have StAggErEd CaSE?
Digging from my laptop pointed to the pihole for DNS:
user4@client_laptop:~$ dig example.com @192.168.0.222
; <<>> DiG 9.18.30-0ubuntu0.24.04.2-Ubuntu <<>> example.com @192.168.0.222
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39132
;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; EDE: 3 (Stale Answer)
;; QUESTION SECTION:
;example.com. IN A
;; ANSWER SECTION:
example.com. 0 IN A 23.215.0.136
example.com. 0 IN A 23.192.228.80
example.com. 0 IN A 23.215.0.138
example.com. 0 IN A 96.7.128.198
example.com. 0 IN A 23.192.228.84
example.com. 0 IN A 96.7.128.175
;; Query time: 6 msec
;; SERVER: 192.168.0.222#53(192.168.0.222) (UDP)
;; WHEN: Fri Feb 21 14:18:18 MST 2025
;; MSG SIZE rcvd: 142
Debug Token:
For some reason, I don't see an option to generate a debug log via the web interface under tools or settings, so I ran `pihole -d' instead.
https://tricorder.pi-hole.net/tK5AhNxW/