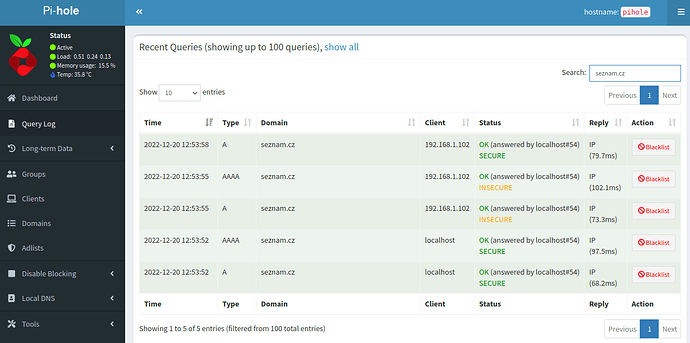
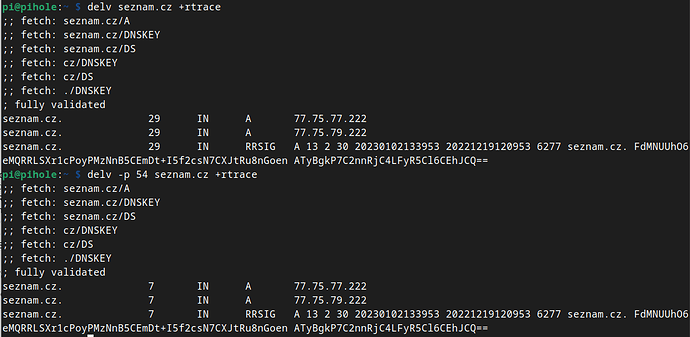
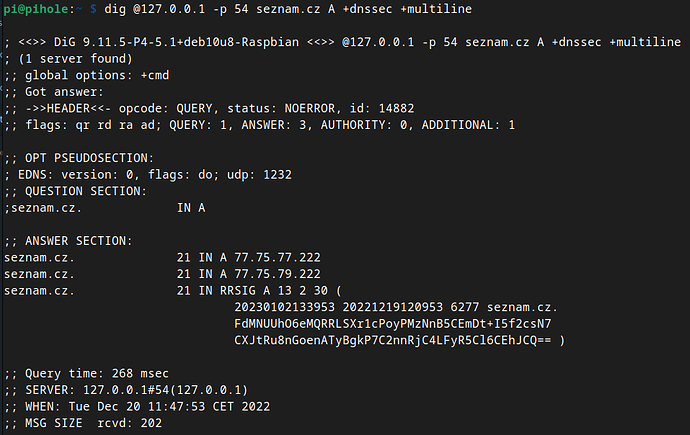
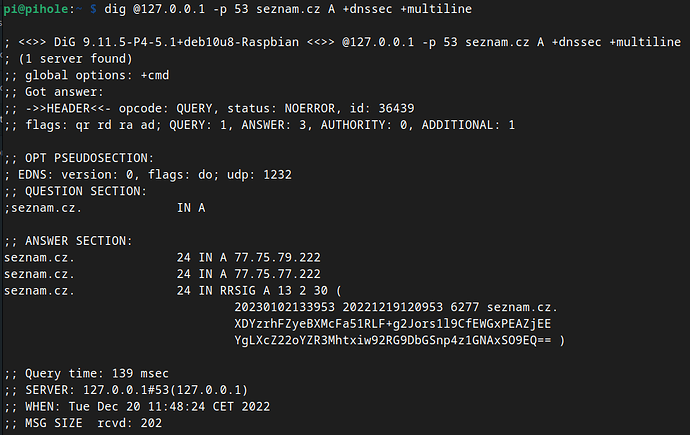
Ok, I've just done some testing.
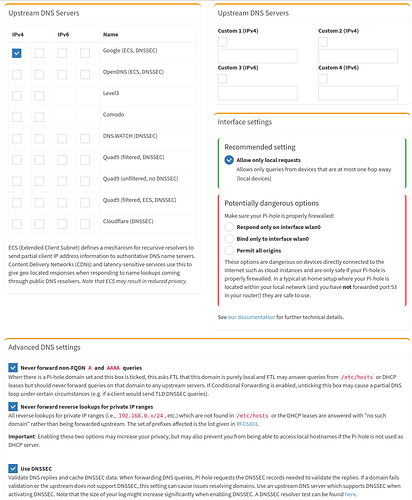
In the  first part, I kept my current configuration (with local stubby on port 54 as the only DNS configured in the Pi hole).
first part, I kept my current configuration (with local stubby on port 54 as the only DNS configured in the Pi hole).
In the  second part, I used the google DNS (as predefined in the Pi hole config).
second part, I used the google DNS (as predefined in the Pi hole config).
I did the testing with the Fedora 37 host (192.168.1.102) and with Android phone (192.168.1.114).
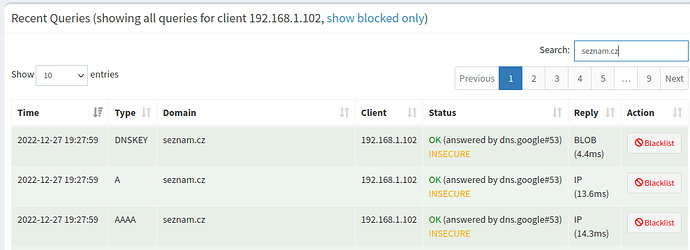
- On the Fedora 37 (192.168.1.102), I run these three commands - "ping -c1 seznam.cz; dig seznam.cz; dig seznam.cz +dnssec"
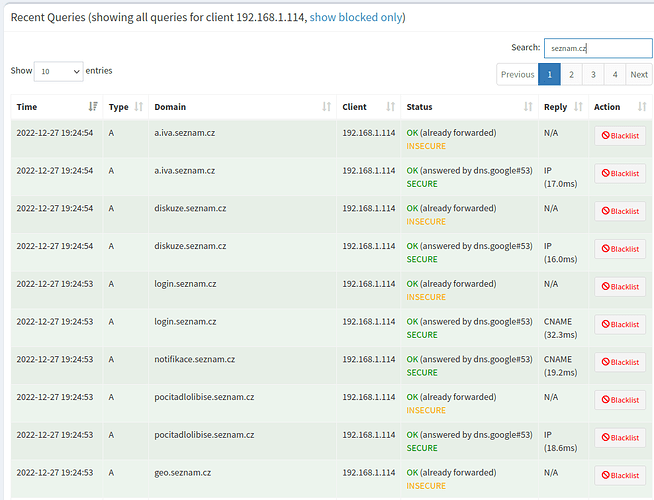
- On the Android phone (192.168.1.114), I was loading the seznam.cz homepage in web browser.
 [ORIGINAL CONFIG]
[ORIGINAL CONFIG]

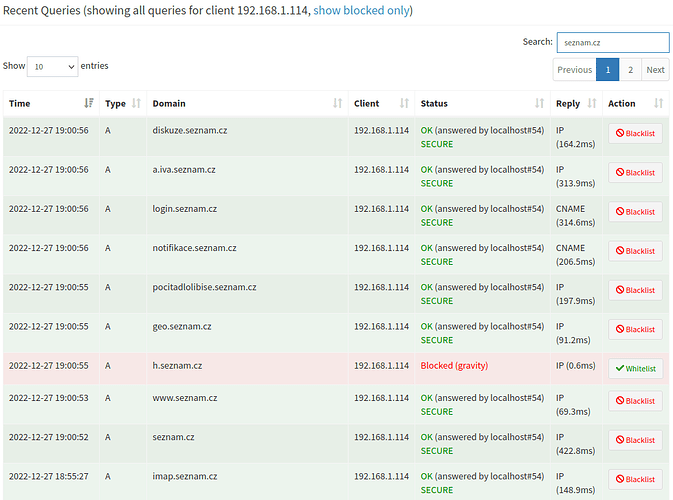
 [Original config] Android phone (192.168.1.114) - SECURE
[Original config] Android phone (192.168.1.114) - SECURE
Capture command:
pi@pihole:~/tcpdump $ sudo tcpdump -n -s 1500 udp and port 53 and host 192.168.1.114 -w dns-traffic-rpi-pi-hole-androidphone.pcap
tcpdump: listening on wlan0, link-type EN10MB (Ethernet), capture size 1500 bytes
^C32 packets captured
41 packets received by filter
0 packets dropped by kernel
PCAP file:
dns-traffic-rpi-pi-hole-androidphone.pcap (3.9 KB)

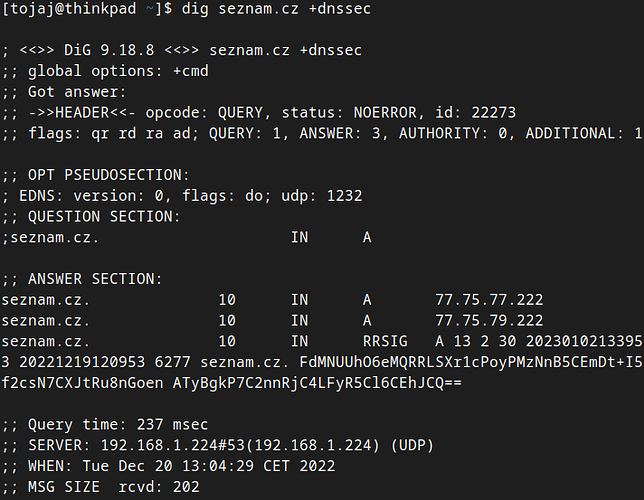
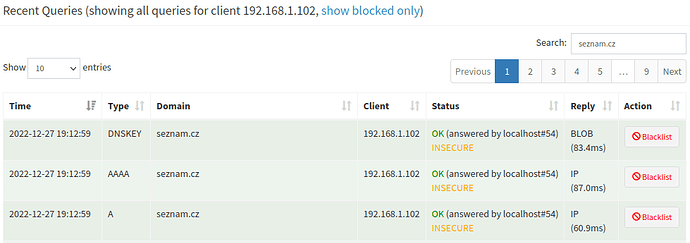
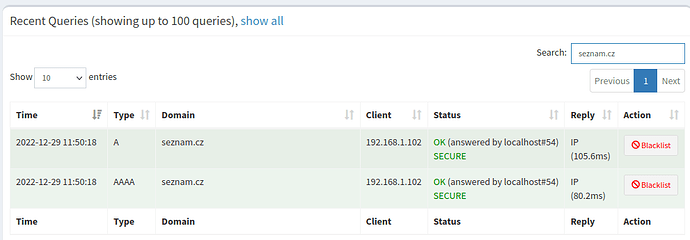
 [Original config] Fedora 37 (192.168.1.102) - INSECURE
[Original config] Fedora 37 (192.168.1.102) - INSECURE
[tojaj@thinkpad ~]$ ping -c1 seznam.cz; dig seznam.cz; dig seznam.cz +dnssec
PING seznam.cz (77.75.77.222) 56(84) bytes of data.
64 bytes from www.seznam.cz (77.75.77.222): icmp_seq=1 ttl=54 time=8.46 ms
--- seznam.cz ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 8.457/8.457/8.457/0.000 ms
; <<>> DiG 9.18.8 <<>> seznam.cz
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26911
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;seznam.cz. IN A
;; ANSWER SECTION:
seznam.cz. 28 IN A 77.75.77.222
seznam.cz. 28 IN A 77.75.79.222
;; Query time: 1 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Dec 27 19:13:00 CET 2022
;; MSG SIZE rcvd: 70
; <<>> DiG 9.18.8 <<>> seznam.cz +dnssec
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20214
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 65494
;; QUESTION SECTION:
;seznam.cz. IN A
;; ANSWER SECTION:
seznam.cz. 28 IN A 77.75.77.222
seznam.cz. 28 IN A 77.75.79.222
seznam.cz. 28 IN RRSIG A 13 2 30 20230108070320 20221225053320 6277 seznam.cz. PkqA7Ify4DsgWxSKp2kSCpmNILHSZm9s5tTZ+pKssrRif3/CgJw2onZv JFgauZ5Jr5ABmCtBlWFGjpnkl8KtWw==
;; Query time: 1 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Dec 27 19:13:00 CET 2022
;; MSG SIZE rcvd: 175
Note that for all three commands, there was only one DNS query (I believe this may be ok).
Capture command:
pi@pihole:~/tcpdump $ sudo tcpdump -n -s 1500 udp and port 53 and host 192.168.1.102 -w dns-traffic-rpi-pi-hole-fedora37.pcap
tcpdump: listening on wlan0, link-type EN10MB (Ethernet), capture size 1500 bytes
^C16 packets captured
23 packets received by filter
0 packets dropped by kernel
PCAP file:
dns-traffic-rpi-pi-hole-fedora37.pcap (3.5 KB)
 [GOOGLE DNS]
[GOOGLE DNS]

 [Google DNS] Android phone (192.168.1.114) - Mix od SECURE and INSECURE
[Google DNS] Android phone (192.168.1.114) - Mix od SECURE and INSECURE
Capture command:
pi@pihole:~/tcpdump $ sudo tcpdump -n -s 1500 udp and port 53 and host 192.168.1.114 -w dns-traffic-rpi-pi-hole-google-androidphone.pcap
tcpdump: listening on wlan0, link-type EN10MB (Ethernet), capture size 1500 bytes
^C78 packets captured
96 packets received by filter
0 packets dropped by kernel
PCAP file:
dns-traffic-rpi-pi-hole-google-androidphone.pcap (8.4 KB)

 [Google DNS] Fedora 37 (192.168.1.102) - INSECURE
[Google DNS] Fedora 37 (192.168.1.102) - INSECURE
[tojaj@thinkpad ~]$ ping -c1 seznam.cz; dig seznam.cz; dig seznam.cz +dnssec
PING seznam.cz (77.75.77.222) 56(84) bytes of data.
64 bytes from www.seznam.cz (77.75.77.222): icmp_seq=1 ttl=54 time=11.5 ms
--- seznam.cz ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 11.454/11.454/11.454/0.000 ms
; <<>> DiG 9.18.8 <<>> seznam.cz
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44420
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;seznam.cz. IN A
;; ANSWER SECTION:
seznam.cz. 6 IN A 77.75.77.222
seznam.cz. 6 IN A 77.75.79.222
;; Query time: 0 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Dec 27 19:28:23 CET 2022
;; MSG SIZE rcvd: 70
; <<>> DiG 9.18.8 <<>> seznam.cz +dnssec
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28824
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 65494
;; QUESTION SECTION:
;seznam.cz. IN A
;; ANSWER SECTION:
seznam.cz. 6 IN A 77.75.79.222
seznam.cz. 6 IN A 77.75.77.222
seznam.cz. 6 IN RRSIG A 13 2 30 20230108070320 20221225053320 6277 seznam.cz. PkqA7Ify4DsgWxSKp2kSCpmNILHSZm9s5tTZ+pKssrRif3/CgJw2onZv JFgauZ5Jr5ABmCtBlWFGjpnkl8KtWw==
;; Query time: 1 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Dec 27 19:28:23 CET 2022
;; MSG SIZE rcvd: 175
Note that for all three commands, there was again only one DNS query.
Capture command:
pi@pihole:~/tcpdump $ sudo tcpdump -n -s 1500 udp and port 53 and host 192.168.1.102 -w dns-traffic-rpi-pi-hole-google-fedora37.pcap
tcpdump: listening on wlan0, link-type EN10MB (Ethernet), capture size 1500 bytes
PCAP file:
dns-traffic-rpi-pi-hole-google-fedora37.pcap (2.5 KB)