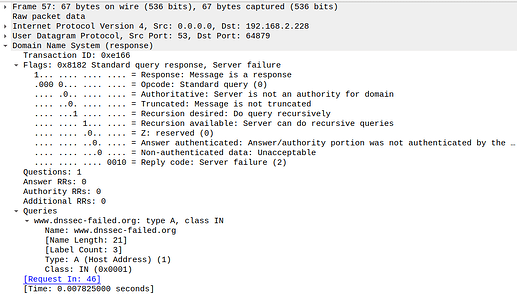
So I was playing around a bit (the below is with the standard Pi-Hole cache size of 10000).
Now, this happens when I dig for dnssec-deployment.org: first time, 'ad' flag is there, subsequent goes show a response without the flag... I know these are served from the Pi-Hole cache as I checked the Pi-Hole webinterface immediately after
(172.16.0.2 is the Pi-Hole address)
pi@Firewalla:~/.firewalla/run/docker/pi-hole/etc-dnsmasq (Purple 2.0) $ dig dnssec-deployment.org @172.16.0.2
; <<>> DiG 9.16.1-Ubuntu <<>> dnssec-deployment.org @172.16.0.2
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12278
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; OPT=15: 00 03 ("..")
;; QUESTION SECTION:
;dnssec-deployment.org. IN A
;; ANSWER SECTION:
dnssec-deployment.org. 30 IN A 104.18.25.160
dnssec-deployment.org. 30 IN A 104.18.24.160
;; Query time: 4 msec
;; SERVER: 172.16.0.2#53(172.16.0.2)
;; WHEN: Thu Apr 13 14:15:02 CEST 2023
;; MSG SIZE rcvd: 88
pi@Firewalla:~/.firewalla/run/docker/pi-hole/etc-dnsmasq (Purple 2.0) $ dig dnssec-deployment.org @172.16.0.2
; <<>> DiG 9.16.1-Ubuntu <<>> dnssec-deployment.org @172.16.0.2
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9864
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;dnssec-deployment.org. IN A
;; ANSWER SECTION:
dnssec-deployment.org. 27 IN A 104.18.25.160
dnssec-deployment.org. 27 IN A 104.18.24.160
;; Query time: 4 msec
;; SERVER: 172.16.0.2#53(172.16.0.2)
;; WHEN: Thu Apr 13 14:15:05 CEST 2023
;; MSG SIZE rcvd: 82
pi@Firewalla:~/.firewalla/run/docker/pi-hole/etc-dnsmasq (Purple 2.0) $ dig dnssec-deployment.org @172.16.0.2
; <<>> DiG 9.16.1-Ubuntu <<>> dnssec-deployment.org @172.16.0.2
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46244
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;dnssec-deployment.org. IN A
;; ANSWER SECTION:
dnssec-deployment.org. 14 IN A 104.18.24.160
dnssec-deployment.org. 14 IN A 104.18.25.160
;; Query time: 0 msec
;; SERVER: 172.16.0.2#53(172.16.0.2)
;; WHEN: Thu Apr 13 14:15:18 CEST 2023
;; MSG SIZE rcvd: 82
Trying to upload the Pi-Hole webinterface Query Log screenshot but it's not working.
2023-04-13 14:15:18 A dnssec-deployment.org 172.16.0.1 OK (cache)
INSECURE IP (0.2ms)
2023-04-13 14:15:05 A dnssec-deployment.org 172.16.0.1 OK (cache)
INSECURE IP (1.3ms)
2023-04-13 14:15:02 A dnssec-deployment.org 172.16.0.1 OK (answered by unbound#53)
SECURE (stale answer) IP (3.2ms)
Now, if I change Pi-Hole cache size to 0, all dig results have the 'ad' flag.
Next test: dane.sys4.de
If I now use Firefox to go to the 'website', Pi-Hole shows 'INSECURE' in the log. If I perform dig for the same address afterwards, I get the 'ad' flag every time and on top of that, when looking into the Pi-Hole logs after, these indeed are identified as 'SECURE'.