I am trying to run a recursive DNS server via Pi-Hole on a Raspberry Pi 4B.
The server itself seems to be running fine, as I am able to access the server's admin page I have ensured the only upstream DNS is 127.0.0.1#5335, so everything appears to be properly configured in that regard. I am also able to ping the server from my desktop.
However, it does not seem to be actually resolving DNS requests. When trying to set the server as my DNS on my desktop it fails to resolve and seemingly defaults back to the DNS provided by my ISP.
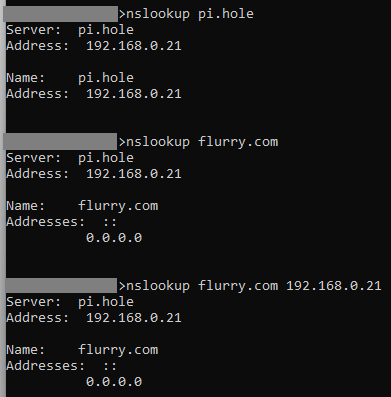
I tried using nslookup example.com 192.168.0.26 (my Pi-hole's IP) to manually force it to use Pi-hole, and it did recognize the server as pi.hole, but the DNS requests ultimately always time out.
nslookup works for any other DNS server I tried, like Cloudflare or Google.
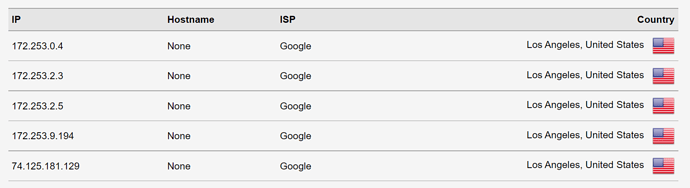
Interestingly enough, I can still see these requests (among some others, likely from when I tried setting Pi-hole as my actual DNS) coming through from my desktop's IP on the Query Log for Pi-hole.
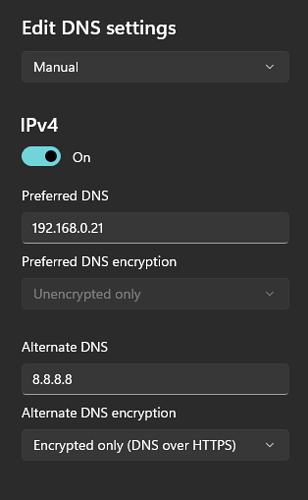
My router is set to use DNS servers provided by my ISP, and I am unable to change them. However, if I manually change my DNS to any major DNS provider (say 1.1.1.1 or 8.8.8.8) through my desktop's network settings, it appears to actually use that DNS and override what my ISP provides. In other words, I can get other DNS providers to work but not Pi-hole.