I use Pi-Hole for a very long time now. Currently on pihole 6 development.
I have about 16 devices served by pihole, but one Samsung phone has a strange dhcp issue. My Leasetime is set to 4 hours. That one phone get a new lease for only 2 minutes.
It request every minute for a renew of the IP adres.
This is the the complete dhcp request from pihole.log and see the lease-time of 2m.
DHCP Request from pihole.log:
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 available DHCP range: 192.168.2.50 -- 192.168.2.109
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 vendor class: android-dhcp-14
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 client provides name: Android-Phone-1
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 tags: known, eth0
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 DHCPACK(eth0) 192.168.2.64 xy:yx:a2:30:89:23 android-phone-1
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 requested options: 1:netmask, 3:router, 6:dns-server, 15:domain-name,
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 requested options: 26:mtu, 28:broadcast, 51:lease-time, 58:T1,
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 requested options: 59:T2, 43:vendor-encap, 114, 108:ipv6-only
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 next server: 192.168.2.253
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 1 option: 53 message-type 5
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 54 server-identifier 192.168.2.253
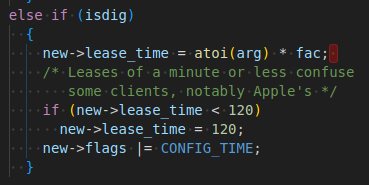
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 51 lease-time 2m
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 58 T1 53s
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 59 T2 1m38s
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 1 netmask 255.255.255.0
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 28 broadcast 192.168.2.255
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 6 dns-server 192.168.2.253
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 3 option: 15 domain-name lan
Sep 21 16:00:18 dnsmasq-dhcp[67639]: 1543505873 sent size: 4 option: 3 router 192.168.2.254
See above option 51: lease-time 2m
Is that comming from pihole of or from somthing else?
Pihole leasetime is set to 4 hours.
Leasetime in pihole.toml is set to 4 hours:
ubuntu@odroid:/etc/pihole$ grep 4h pihole.toml
leaseTime = "4h" ### CHANGED, default = ""
ubuntu@odroid:/etc/pihole$
The DHCPREQUEST for the phone looks like this in pihole.log:
Part of grep output for DHCPREQUEST in pihole.log:
Sep 21 18:22:31 dnsmasq-dhcp[3894]: 3913809830 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:23:31 dnsmasq-dhcp[3894]: 2070630034 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:30:89:23
Sep 21 18:24:32 dnsmasq-dhcp[3894]: 3572629892 DHCPREQUEST(eth0) 192.168.2.64 xy:YX:a2:30:89:23
Sep 21 18:25:33 dnsmasq-dhcp[3894]: 2567706771 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:26:34 dnsmasq-dhcp[3894]: 1003353362 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:27:35 dnsmasq-dhcp[3894]: 3716788428 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:28:35 dnsmasq-dhcp[3894]: 387466275 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:29:36 dnsmasq-dhcp[3894]: 3203616886 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:30:37 dnsmasq-dhcp[3894]: 3517785719 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:31:38 dnsmasq-dhcp[3894]: 2026294367 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Sep 21 18:32:39 dnsmasq-dhcp[3894]: 3077729820 DHCPREQUEST(eth0) 192.168.2.64 xy:yx:a2:30:89:23
Why every minute a new DHCPREQUEST from only one Samsung android phone!
Another but older Samsung phone has not this problem. Both phones are running Android 14.
Pihole version:
ubuntu@odroid:/var/log/pihole$ pihole -v
Core
Version is v5.18.3-479-ge3dc067 (Latest: null)
Branch is development
Hash is e3dc0670 (Latest: e3dc0670)
Web
Version is v5.21-951-g32f89861 (Latest: null)
Branch is development
Hash is 32f89861 (Latest: 32f89861)
FTL
Version is vDev-23e614c (Latest: null)
Branch is development
Hash is 23e614cc (Latest: 23e614cc)
The pihole-server is used for dhcp and dns and is running ubuntu 2404 on a odroid-c4 with all updates.
I can upload a debug log to tricorder if requested.
I want to know if this is a pihole problem or bug, or is it a phone issue.
Gerrit.