- In my NAT network 10.141.165.191 is the Chromecast
- 10.141.165.247 is the Pi Hole.
- The Arris router provides Wifi and is the gateway at 10.141.165.1
- On the Pi Home I have OpenDNS (ECS) and Cloudflare selected.
- On the Arris, under Parental Control > Managed Services, I have DNS (UDP port 53) as a Blocked Service
- Under Auto-Learned Devices, I have the Chromecast set to No under Trusted

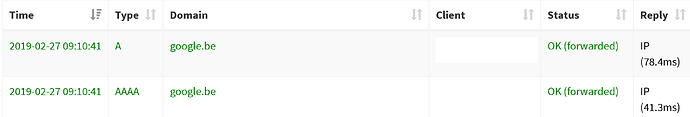
Here are the logs when I start a YouTube video from my Android phone (IP 10.141.165.167), also set to Untrusted so the Pi Hole is forced to be the DNS.
Feb 26 21:56:19 dnsmasq[595]: query[A] clients3.google.com from 10.141.165.191
Feb 26 21:56:19 dnsmasq[595]: forwarded clients3.google.com to 1.0.0.1
Feb 26 21:56:19 dnsmasq[595]: reply clients3.google.com is <CNAME>
Feb 26 21:56:19 dnsmasq[595]: reply clients.l.google.com is 172.217.12.174
Feb 26 21:56:21 dnsmasq[595]: query[A] r3---sn-ab5l6ndy.googlevideo.com from 10.141.165.191
Feb 26 21:56:21 dnsmasq[595]: forwarded r3---sn-ab5l6ndy.googlevideo.com to 1.0.0.1
Feb 26 21:56:21 dnsmasq[595]: reply r3---sn-ab5l6ndy.googlevideo.com is <CNAME>
Feb 26 21:56:21 dnsmasq[595]: reply r3.sn-ab5l6ndy.googlevideo.com is 173.194.185.232
Feb 26 21:56:28 dnsmasq[595]: query[A] connectivitycheck.gstatic.com from 10.141.165.191
Feb 26 21:56:28 dnsmasq[595]: /etc/hosts connectivitycheck.gstatic.com is 10.141.165.247
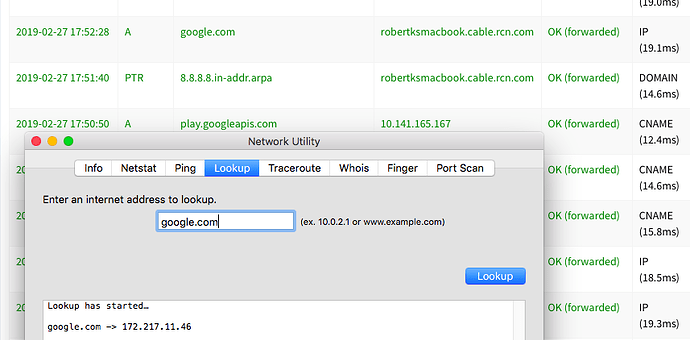
Feb 26 21:56:29 dnsmasq[595]: query[A] www.google.com from 10.141.165.191
Feb 26 21:56:29 dnsmasq[595]: cached www.google.com is 172.217.10.68
Feb 26 21:56:29 dnsmasq[595]: query[AAAA] www.google.com from 10.141.165.191
Feb 26 21:56:29 dnsmasq[595]: cached www.google.com is 2607:f8b0:4006:818::2004
Feb 26 21:56:44 dnsmasq[595]: query[A] www.google.com from 10.141.165.167
Feb 26 21:56:44 dnsmasq[595]: cached www.google.com is 172.217.10.68
Do those logs look like the Chromecast is forwarding DNS requests? I have these iptables rules in the Pi Hole:
iptables -L -n -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT udp -- 8.8.4.4 0.0.0.0/0 udp dpt:53 to:10.141.165.1
DNAT udp -- 8.8.8.8 0.0.0.0/0 udp dpt:53 to:10.141.165.1
DNAT tcp -- 192.168.1.100 0.0.0.0/0 tcp dpt:53 to:10.141.165.1
DNAT udp -- 0.0.0.0/0 8.8.8.8 udp dpt:53 to:10.141.165.1
DNAT udp -- 0.0.0.0/0 8.8.4.4 udp dpt:53 to:10.141.165.1
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0
But this route:
route -ne
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 10.141.165.1 0.0.0.0 UG 0 0 0 eth0
8.8.4.4 10.141.165.1 255.255.255.255 UGH 0 0 0 eth0
8.8.8.8 10.141.165.1 255.255.255.255 UGH 0 0 0 eth0
10.141.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth0
pi@raspberrypi:~ $ ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=122 time=13.2 ms
c64 bytes from 8.8.8.8: icmp_seq=2 ttl=122 time=11.9 ms
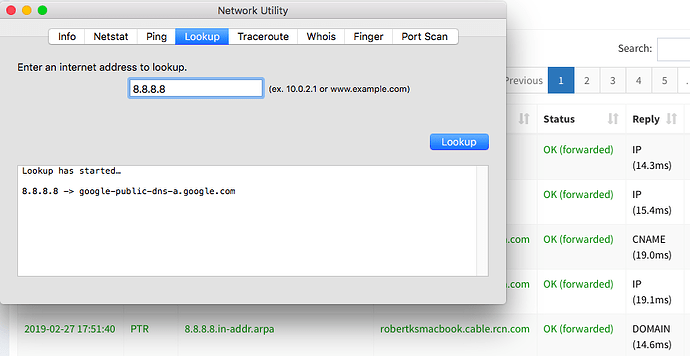
What else am I missing? I did get this tip to work, i.e., to block connectivitycheck.gstatic.com .