Originally published at: Compromised Donor Emails: A post-mortem – Pi-hole
What Information Was Exposed (and What Was Not)
The breach is limited to names and email addresses provided during the donation process.
It is important to mention that we don’t have access to or store any credit card numbers or verified names or addresses or phone numbers. Any PII is maintained directly by the card processors, Stripe or PayPal. We make it clear in the donation form that we don’t even require a valid name or email address, it’s purely for users to see and manage their donations.
What Happened
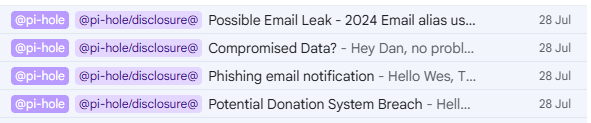
We first became aware of the issue on Monday 28th July, when we started to receive emails suggesting that we were facing a possible data breach
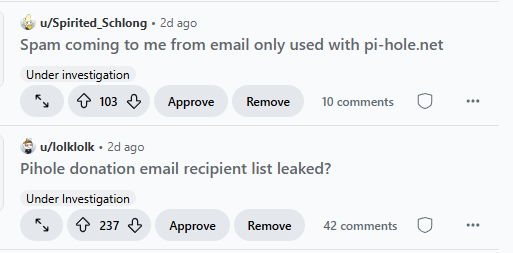
And a couple of Reddit posts let us know about the same thing.
And a post on our Discourse forum….
The email addresses that people were receiving these emails to were emails that had been used exclusively when leaving us a donation.
How could this be? Had someone gotten access to the admin page of our WordPress site? Were we running some out of date plugin that had a known vulnerability against it? Had the payment providers suffered a breach?
One of many threads we pulled at was checking the user account list. Our hypothesis leaning toward an integration with a plugin creating user accounts, as Dan commented on Reddit. (Spoiler alert… the post has been edited with the actual reason)
Checking with the plugin authors
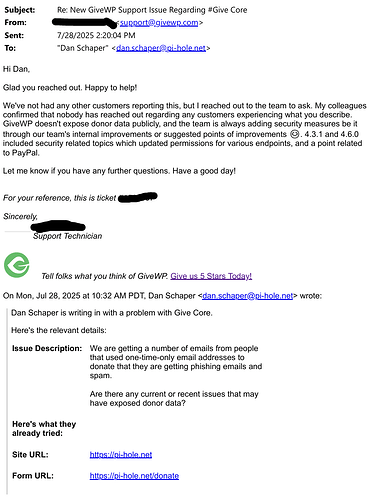
So, we reached out to the authors of the plugin we use for our donations page (GiveWP) to see if they knew of anything that might be the cause of this. Nobody else had reported anything similar
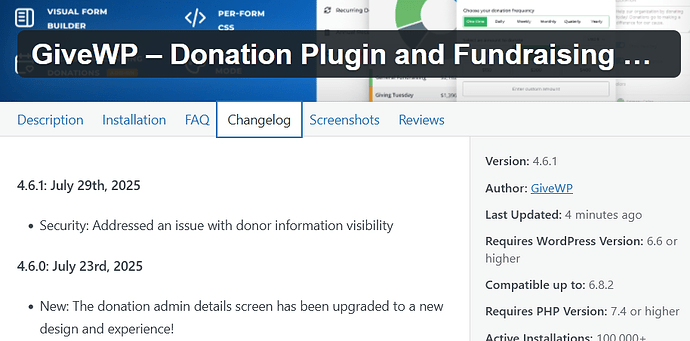
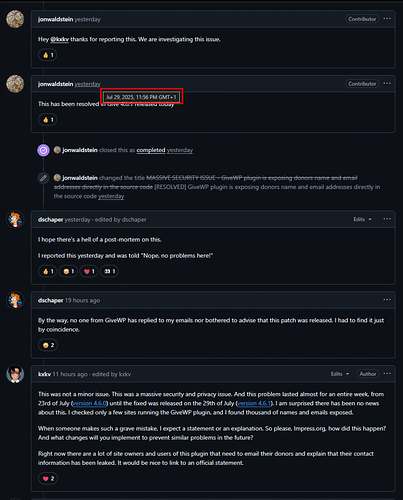
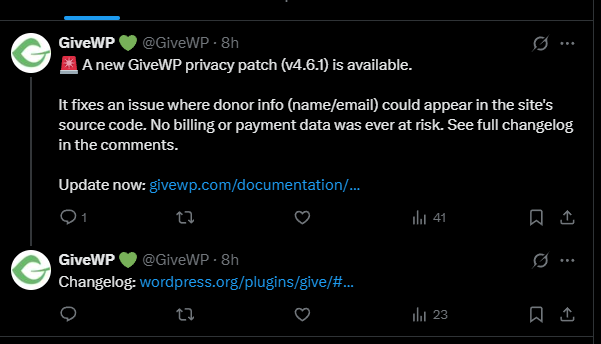
The next day, we discovered that the donation plugin we use, GiveWP, had released an update with the description: “Security: Addressed an issue with donor information visibility.”
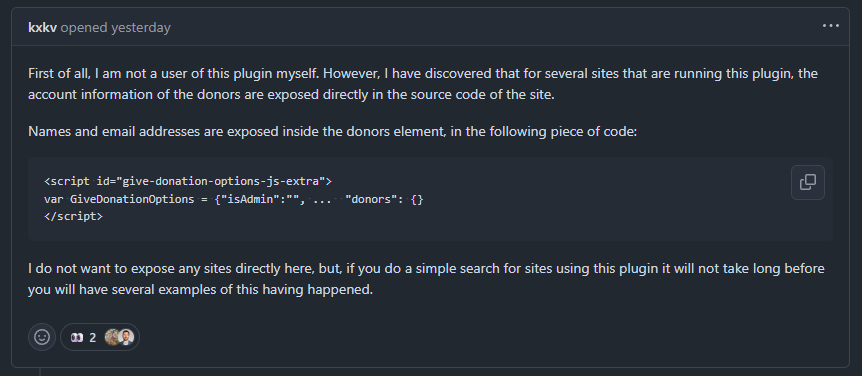
Further investigation revealed a public issue had been filed on their GitHub repository by another user, detailing the vulnerability. (For transparency, we have archived a copy of the report here).
The names and email addresses of anyone that had ever donated via our donation page was there for the entire world to see (provided they were savvy enough to right click->View page source)
Within a couple of hours of this report, they had patched the bad code and released 4.6.1
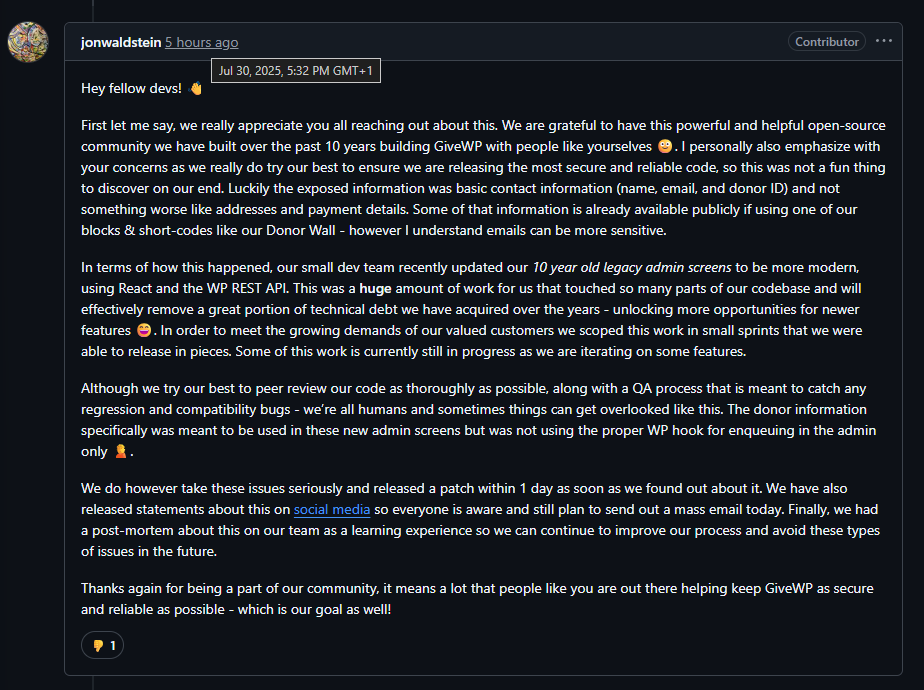
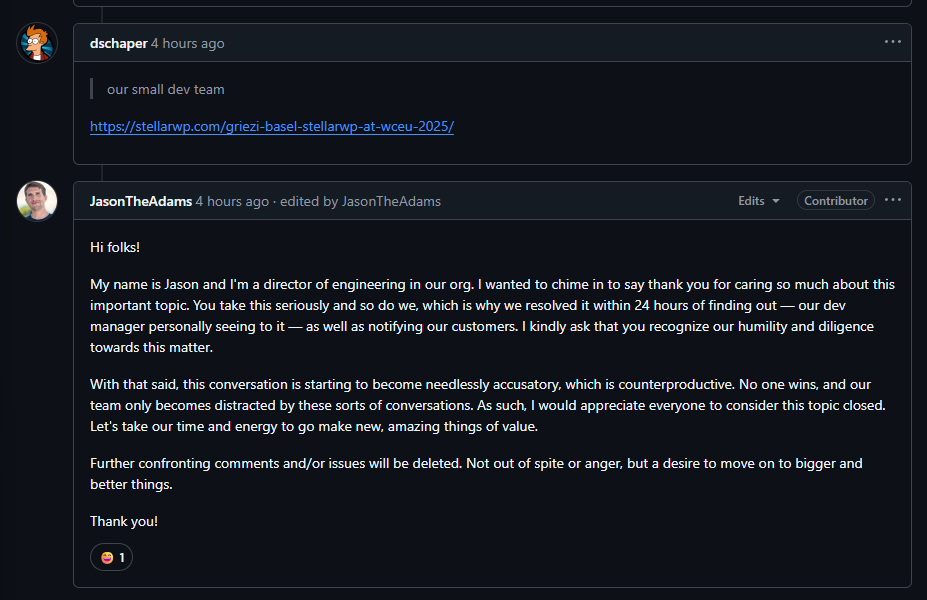
While the patch was released quickly, we were concerned by the 17.5-hour delay (“4 business hours”…) between the critical security fix and any official notification from the GiveWP team. However, In our view, their public statement did not sufficiently address the potential impact of exposing donor names and email addresses.
And with that, the conversation is effectively shut down.
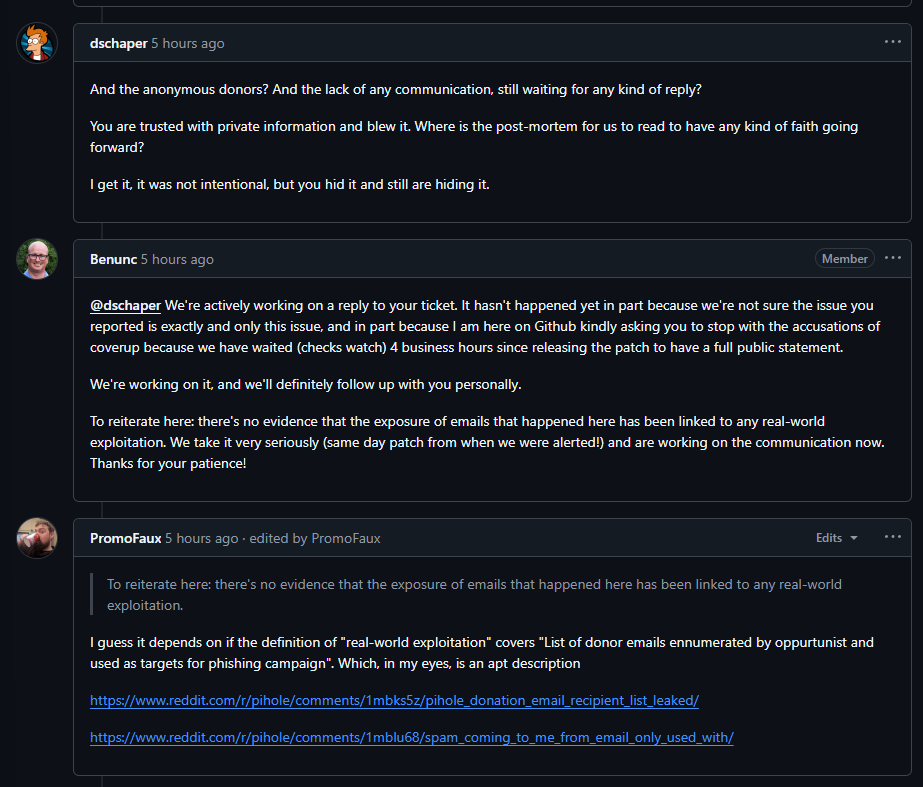
And yes, while no billing or payment info was at risk, they really downplay the impact that the accidental reveal of names and email addresses can have. (To quote: “there’s no evidence that the exposure of emails that happened here has been linked to any real-world exploitation”)
If we’re being entirely honest, the response from the GiveWP team has been disappointing.
Where we’re left
We take full responsibility for the software we deploy. We placed our trust in a widely-used plugin, and that trust was broken. This incident exposed our donors’ information and put our reputation at risk. This is an unacceptable outcome.
While there is no way for us to have forseen this happening, we cannot apologise enough to anyone of our donors who have seen an increase in spam due to this. We put our trust in a WordPress plugin, and they broke that trust – in turn putting our own reputation at risk.
It sucks, and it’s not a position we ever thought we’d be in, but here we are. We hope that we can gain back the trust of those affected by this.