Hi!
I have already opened a bug report on github, but I also wanted to use the opportunity to describe my errors here. I don't know if this is directly related to the upgrade to the v6 developer - but everything worked until today at noon before the update.
Versions
Pi-hole version is development-v6 v5.17.1-161-g2841a33 (Latest: v5.17.2)
web version is development-v6 v5.19-334-ge3a547df (Latest: v5.20.2)
FTL version is development-v6 vDev-c5067b3 (Latest: v5.23)
Platform
raspberry pi 3, raspberry pi os 32 bit
Expected behavior
I expected that the pihole worked after upgraded to development v6 and after removal of php and lighthttpd.
Actual behavior / bug
Pihole didnt work. No DNS requests worked, on all devices which are connected to pihole.
Then I got an error:
Maximum number of concurrent DNS queries reached (max: 150)
Needed to follow this to fix my issue.
Edit: Nope, it didnt fix my issue. Issue still active.
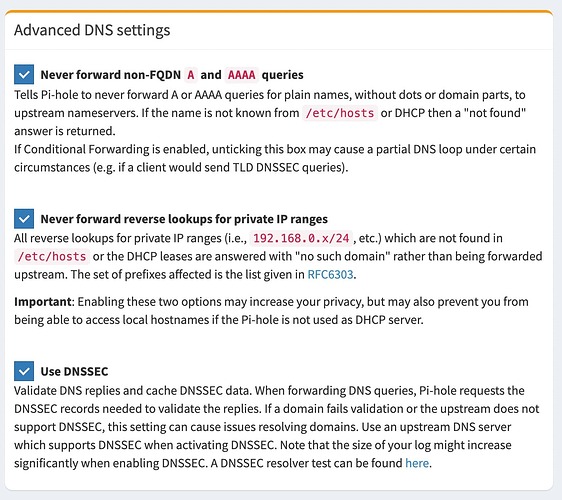
As in the thread, there was no 02-custom-settings.conf in /etc/dnsmasq.d
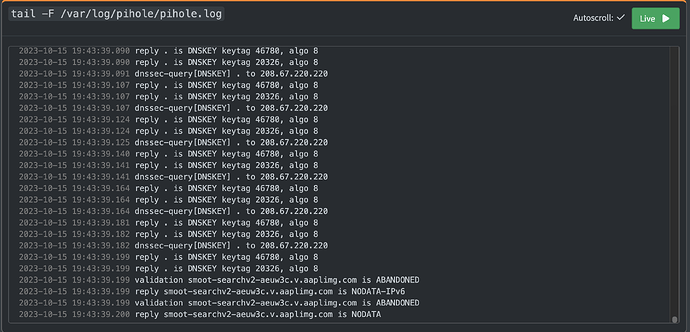
Also seen this maaaany requests / logs in my pihole.log:
2023-10-15 13:49:51.666 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.684 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.684 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.684 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.700 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.700 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.701 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.722 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.723 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.723 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.740 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.740 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.741 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.756 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.756 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.757 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.775 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.775 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.776 dnssec-query[DNSKEY] . to 208.67.222.222
2023-10-15 13:49:51.802 reply . is DNSKEY keytag 46780, algo 8
2023-10-15 13:49:51.802 reply . is DNSKEY keytag 20326, algo 8
2023-10-15 13:49:51.803 dnssec-query[DNSKEY] . to 208.67.222.222
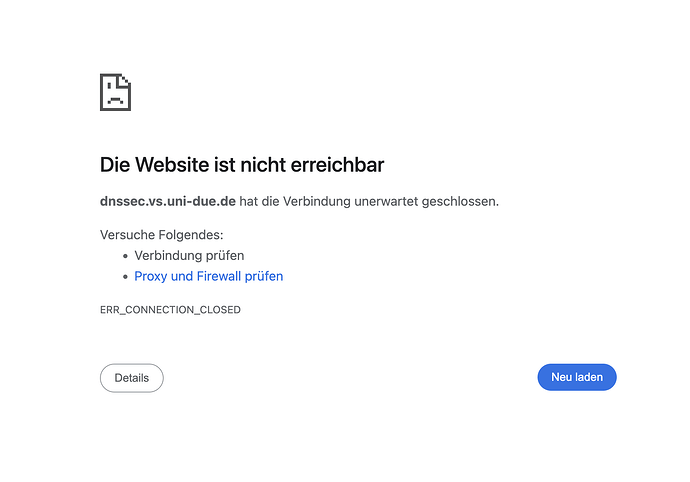
Also this on my webinterface dashbord:
![]()
Steps to reproduce
Steps to reproduce the behavior:
Update from latest stable release to development release