I voted for this feature request, but unfortunately, I don't think it is possible.
I used to enable this feature in pihole, when it was still using dnsmasq, but after numerous discussions on this forum, I decided to disable DNSSEC on dnsmasq (=pihole-FTL) and enabled DNSSEC validation on unbound.
With or without proxy-dnssec, there appears to be no way to distinguish the difference, e.g. the results in the logs are always the same:
Dec 8 19:20:48 dnsmasq[9241]: query[A] sigok.verteiltesysteme.net from 127.0.0.1
Dec 8 19:20:48 dnsmasq[9241]: forwarded sigok.verteiltesysteme.net to 127.10.10.2
Dec 8 19:20:48 dnsmasq[9241]: reply sigok.verteiltesysteme.net is 134.91.78.139
Dec 8 19:20:50 dnsmasq[9241]: query[A] sigfail.verteiltesysteme.net from 127.0.0.1
Dec 8 19:20:50 dnsmasq[9241]: forwarded sigfail.verteiltesysteme.net to 127.10.10.2
Dec 8 19:20:50 dnsmasq[9241]: reply error is SERVFAIL
A valid response with proxy-dnssec enabled simply returns the A record, an invalid response returns SERVFAIL.
When DNSSEC is enabled in pihole-FTL, response would be SECURE, INSECURE, BOGUS
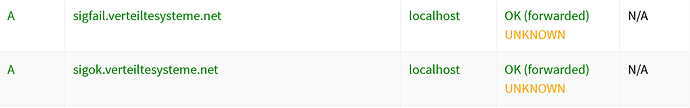
The query log currently cannot handle this configuration, confirmed by the following test:
- move
proxy-dnssecinto /etc/dnsmasq.d/01-pihole.conf - as soon as you start performing queries and refresh the query log in the admin console, every entry will have an UNKNOWN status, the query log doesn't even show SERVFAIL, even though the dig command showed that result.
dig sigfail.verteiltesysteme.net @127.0.0.1
; <<>> DiG 9.11.5-P4-5.1-Raspbian <<>> sigfail.verteiltesysteme.net @127.0.0.1
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 2120
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
Don't forget to undo the test scenario!
There are DNSSEC plugins for chrome and firefox, the proposed configuration might still be beneficial for these browsers, using that plugin, but I didn't test this....