Very interested in your solution, wondering how this works.
I have phole + unbound, without all-servers. Unbound is configured to listen on server=127.10.10.2#5552 and server=fdaa:bbcc:ddee:2::5552#5552
I don't know why, but dnsmasq appears to prefer the IPv6 resolver, even though I have configured only the pi's IPv4 address as DNS server, using DHCP, on all the clients, some, if not most, devices don't even have an IPv6 address.
dashboard / Queries answered by:
- blocklist 27.3%
- cache 11.9%
- unbound-ipv6 56.9%
- unbound-ipv4 4 4%
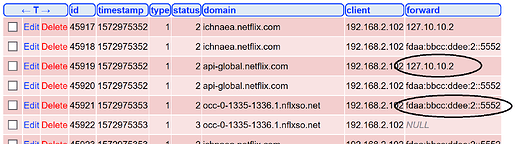
Looking at the FTL database (updated installation instructions in my installation manual, chapter 20, section 3 - the referred topic is for an older version), I see the results in the queries table:
I wonder if:
- When using
all-servers, are the requests to all the resolvers in thequeries table, or just the one served to the client? This would also be visible in thepihole query log(uses that table) - How does your `dashboard / Queries answered by graph look like? All resolvers same percentage or actually reflecting the fasted response?
@DL6ER: If this feature request makes it into pihole, obviously the query table (dashboard) could use an additional column answered by (the IP or name of the resolver), the info is already available in the database.