I did address that in my previous post - please check.
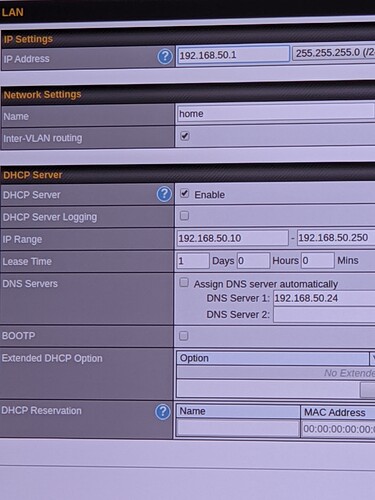
With regards to your router's DNS proxy option, I find your manual to be inconclusive.
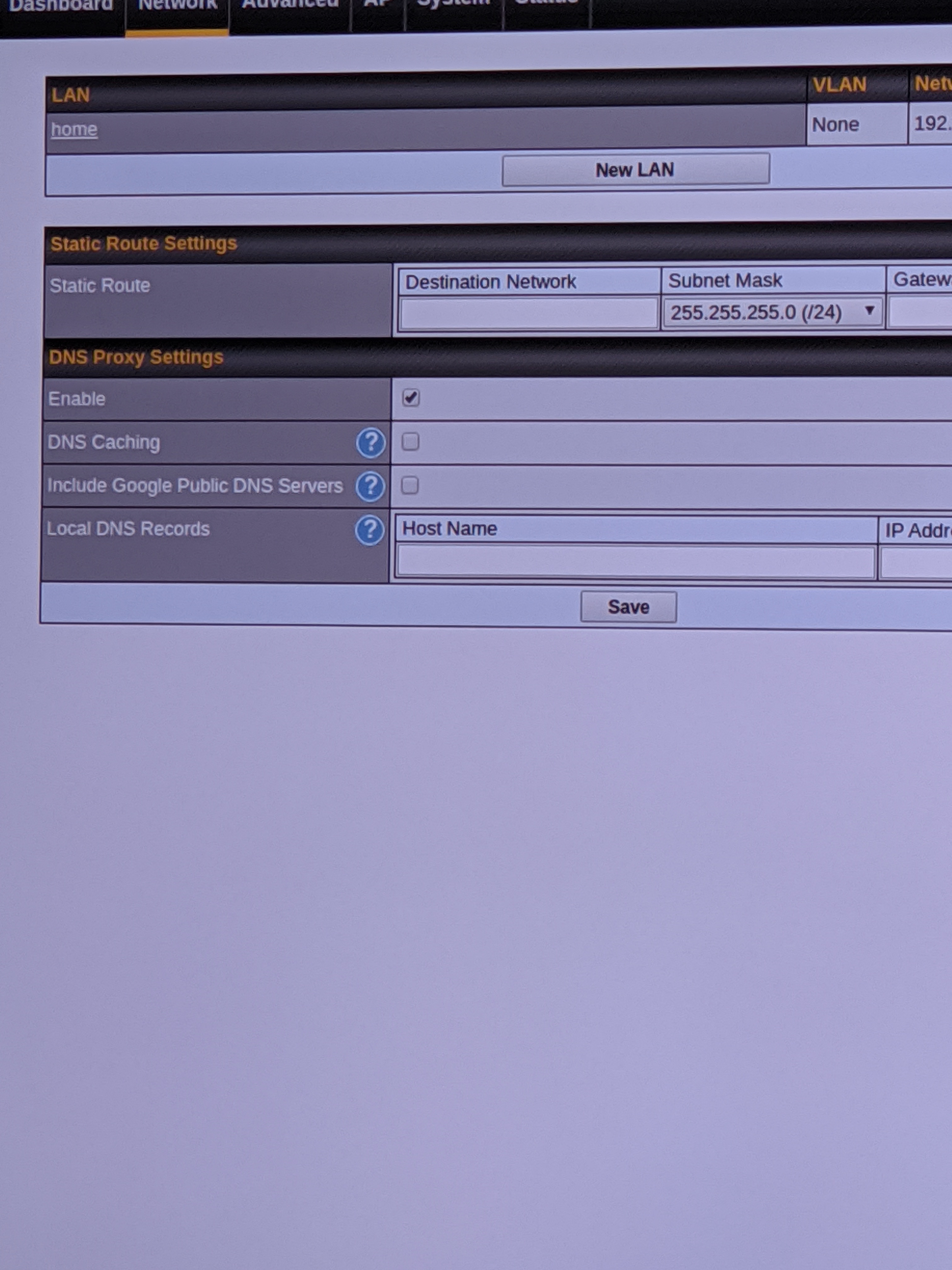
The DNS proxy screenshot shows a section labeled DNS Resolvers that would allow you to define a custom DNS server for a LAN connection, which seems to be what you want.
However, the description for DNS Resolvers reads
Check the box to enable the WINS server
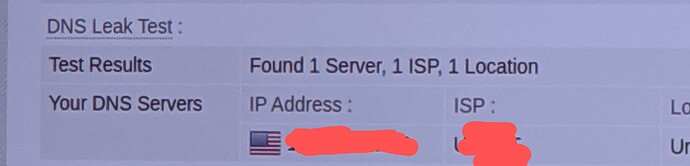
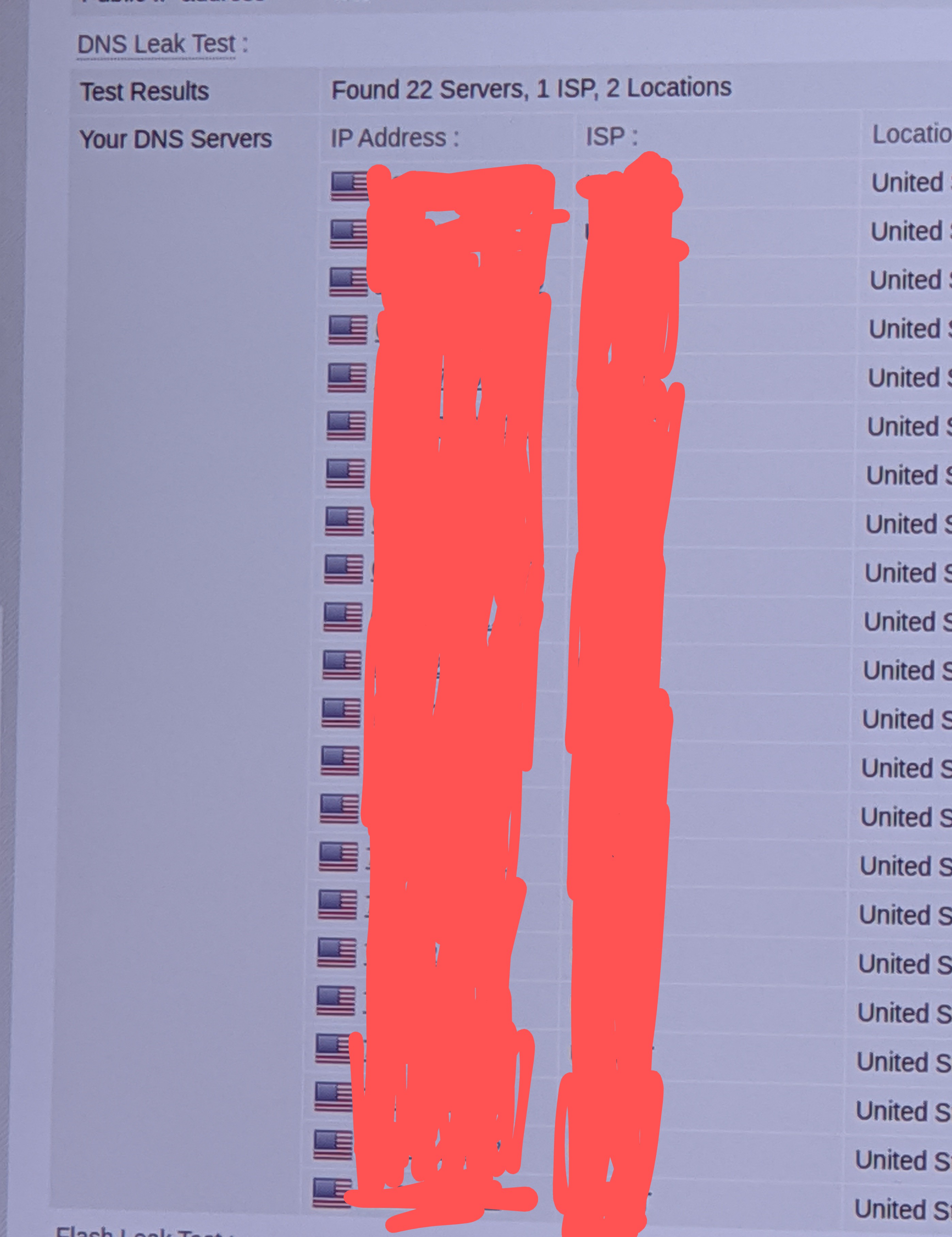
From your observation, yubiuser is right in diagnosing a DNS loop, but it is not entirely clear if you had used that last option or not.
Either way, you may want to seek clarification with the folks at Pepwave - their forum runs on Discourse as well, and they seem friendly enough over there.
The term NAT might lead to misunderstandings when used to discuss with Pepwave support.
Commonly, a full NAT (or network address translatin) would be understood to comprise your entire network traffic and include address rewriting, i.e. replacing the sending computer's IP with your router's, forcing all traffic -send and receive- through your router.
You'd effectively be double-NATting your network to the external public and to internal Pi-hole, which is not required.
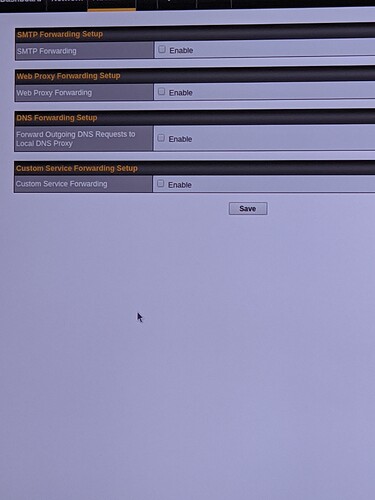
What you need here is a simple port redirection for DNS protocols, rerouting DNS traffic directed at an arbritary IP to your Pi-hole machine and have Pi-hole provide answers directly to clients in the same local network.
While this is still achieved by defining a rule in the NAT table, it is distinctively different from the rules and behaviour invoked when using the term NAT for routers.
If your router ultimately does not support DNS port redirection, you should consider yubiuser's early advice of blocking DNS ports at your router. Again, you should probably check the Pepwave forums for configuration specifics - they likely are more experienced in these matters over there.
That said, our forum would appreciate if you'd still share your findings here once you've got things sorted.
Independent from that, we'll be here to assist you with any Pi-hole issues you may encounter.